Deploy additional relays
After deploying your first Deep Security Relay, you should deploy at least one more for redundancy and load-balancing reasons. You may even need to deploy more depending on the size and scope of your deployment.
When deploying relays, you need to do the following:
Plan the best number and location of relays
The optimal number and placement of relays depends on the following factors:
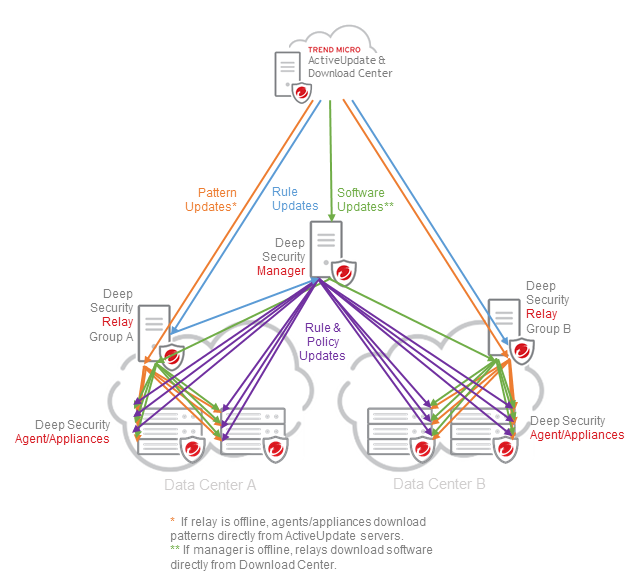
Geographic region and distance
Ideally, each geographic region should have its own relay group with at least two relays.
Agents should use local relays in the same geographic region. Long distance and network latency can slow down update redistribution. Downloading from other geographic regions can also increase network bandwidth and/or cloud costs.
Network architecture and bandwidth limits
Ideally, each network segment of agents with limited bandwidth should have its own relay group with at least two relays.
Low bandwidth Internet/WAN connections, routers, firewalls, VPNs, VPCs, or proxy devices (which can all define a network segment) can be bottlenecks when large traffic volumes travel between the networks. Bottlenecks slow down update redistribution. Agents therefore usually should use local relays inside the same network segment — not relays outside on bottlenecked external networks.
For example, your relay group hierarchy could minimize Internet and internal network bandwidth usage. Only one parent relay group might use the Internet connection; subgroups would download from the parent, over their local network connection. Agents would download from their local relay group.
Large scale deployments might have many agents connect to each relay. This requires relays on more powerful, dedicated servers, as opposed to more relays on shared servers. For more information, see Deep Security Agent sizing and resource consumption.
Air-gapped environments
Most deployments can connect to the Internet. But if your relays cannot connect to the Trend Micro ActiveUpdate server on the Internet because they are on an isolated network (an "air-gapped" deployment), then you need to do the following:
- Add a separate relay in a demilitarized zone (DMZ) (which can connect to the Internet) to get the security updates.
- Copy updates from the DMZ relay to your other, air-gapped relays.
For details, see Configure agents that have no internet access.
Configure the update source
Before setting up relays, perform the following to define the source of updates and when to bypass the usual relay hierarchy to get updates:
- Go to Administration > System Settings > Updates.
-
Optionally, configure Primary Security Update Source and Secondary Source.
By default, the primary source is Trend Micro Update Server which is accessed via the Internet. Do not change the setting, unless your support provider has told you to configure Other update source. Alternative update source URLs must include "http://" or "https://".
-
Typically, agents connect to a relay to get security updates when Deep Security Manager tells them to. But if computers cannot always connect with the manager or relays (such as during scheduled maintenance times) and enough Internet/WAN bandwidth is available, you can select the following:
- Allow Agents/Appliances to download security updates directly from Primary Security Update Source if Relays are not accessible
- Allow Agents/Appliances to download security updates when Deep Security Manager is not accessible
If you protect laptops and portable computers, they might sometimes be far from support services. To avoid risk of a potentially problematic security update while they travel, deselect these options.
- If you require security updates for older agents, select Allow supported 8.0 and 9.0 Agents to be updated. By default, Deep Security Manager does not download updates for Deep Security Agent 9.0 and earlier because most of these agents are no longer supported. For details on which older agents are still supported, see Deep Security LTS lifecycle dates.
- If you would like Deep Security Manager to auto-import agent update builds to your local inventory, select Automatically download updates to imported software.
This setting imports the software to Deep Security Manager but does not automatically update your agent or appliance software. See Upgrade Deep Security Agent for more information.
- Typically, relays connect to Deep Security Manager to get software updates to redistribute. However, if relays cannot always connect with the manager (such as during scheduled maintenance times or when there is an enterprise firewall between the manager and relays), you can select Allow Relays to download software updates from Trend Micro Download Center when Deep Security Manager is not accessible. Relays will get software updates directly from the Download Center instead.
- Configure Alternate software update distribution server(s) to replace Deep Security Relays to specify an alternative source for software updates, noting that security updates still need to come from a relay. Consider an alternative server if your relay has an elastic IP address, if you plan on configuring your relays to only receive security updates (not software updates), or if you want to host software on a web server for efficiency and availability reasons. Enter
https://<IP_or_hostname>:<port>/replacing <IP_or_hostname>:<port> with one of the following:- The private network IP address and port of the relay that has an elastic IP address.
- The web server and port where you plan to host the Deep Security software.
Hybrid cloud environments often have some agents and relays in a public cloud, while others (and the manager) are inside your private network. To avoid the risk of opening port numbers on your private network firewall, or manually copying software packages to your relays in the cloud, select this option.
Configure relays
After determining the location and the number relays, as well as what update sources they should use, you can do the following:
- Create relay groups
- Enable relays
- Assign agents to a relay group
- Connect agents to a relay's private IP address
Create relay groups
Relays must be organized into relay groups. The relay groups themselves can be further organized into hierarchies.
If you installed a co-located relay during the Deep Security Manager installation, then it automatically created a default relay group. But if you need more groups for other locations (see Plan the best number and location of relays), you can create more.
- Go to Administration > Updates > Relay Management to open the Relay Group Properties pane.
- Click New Relay Group.
- Type a Name for the relay group.
-
In Update Source, select either Primary Security Update Source or, in case of a subgroup, the name of the parent relay group.
Note that the Default Relay Group is not included in the list of update sources, and therefore cannot be configured as a parent.
Consider selecting the update source with the best cost and speed. Even if a relay group is part of a hierarchy, sometimes it might be cheaper and faster to download updates from the Primary Security Update Source instead, not the parent relay group.
-
If this relay group must use a proxy when connecting to the Primary Security Update Source, select Update Source Proxy. For details, see Connect to the Primary Security Update Source via proxy.
Unlike other relay groups, Default Relay Group uses Primary Security Update Proxy used by Agents, Appliances, and Relays setting available in the Administration > System Settings > Proxies tab.
If this relay group usually connects to a parent relay group, then the subgroup does not use the proxy unless the parent relay group is unavailable and it is configured to fall back to using the Primary Security Update Source.
- Under Update Content, select either Security and software updates or Security updates only. If you select Security updates only, you must configure an alternative software update source. For details, see Configure the update source.
To minimize latency and external/Internet bandwidth usage, create a relay group for each geographic region and/or network segment.
Enable relays
- Make sure the relay computer meets the requirements. See Deep Security Agent sizing and resource consumption and Deep Security Relay requirements.
- Make sure you allow inbound and outbound communication to and from the relay on the appropriate port numbers. See Deep Security port numbers.
- If the relay must connect through a proxy, see Connect to the Primary Security Update Source via proxy.
- Deploy an agent on the chosen computer. See Get Deep Security Agent software and Install the agent.
- Enable the agent as a relay:
- Log in to Deep Security Manager.
- Click Administration at the top.
- Click Relay Management in the left navigation pane.
- If you are using Linux, before enabling the relay, create a user nobody and a relay group nogroup.
- Select the relay group into which the relay will be placed. If a relay group does not exist, create one. If you are using Linux, create a user nobody and a relay group nogroup.
- Click Add Relay.
- In Available Computers, select the agent you just deployed.
- Click Enable Relay and Add to Group.
The agent is enabled as a relay and is displayed with a relay icon (
).
To minimize latency and the Internet bandwidth usage, group together relays that are in the same geographic region and network segment.
You can use the search field to filter the list of computers.
Assign agents to a relay group
You must indicate which relay group each agent should use. Either assign each agent to a relay group manually, or set up an event-based task to assign new agents automatically.
- Go to Computers.
-
Right-click the computer and select Actions > Assign Relay Group.
To assign multiple computers, Shift-click or Ctrl-click computers in the list, and then select Actions > Assign Relay Group.
-
Select the relay group that computer should use.
To minimize latency and external/Internet bandwidth usage, assign agents to relays that are in the same geographic region and/or network segment.
Connect agents to a relay's private IP address
If your relay has an elastic IP address, agents within an AWS VPC may not be able to reach the relay via that IP address. Instead, they must use the private IP address of the relay group.
- Go to Administration > System Settings.
- In the System Settings area, click the Updates tab.
- Under Software Updates, in the window Alternate software update distribution server(s) to replace Deep Security Relays , type:
https://<IP>:<port>/where
<IP>is the private network IP address of the relay, and<port>is the relay port number - Click Add.
- Click Save.
If your relay group’s private IP changes, you must manually update this setting, as it does not update automatically.