Before deploying the appliance
Before you deploy the Deep Security Virtual Appliance, complete the tasks below.
If you want to upgrade the appliance, see instead Upgrade Deep Security Virtual Appliance
Review system requirements
- Review this table to see which NSX licenses and versions are supported.
- Review these system requirements.
Install or upgrade NSX, Deep Security Manager and other components
After reviewing the system requirements, do the following:
- Install or upgrade NSX and make sure you're using a license that supports the features you want.
- Install or upgrade Deep Security Manager.
- Install or upgrade other required software and hardware.
Re-register NSX-T
Read this section if you previously added NSX-T to Deep Security Manager using the instructions in Add a VMware vCenter.
You may need to re-register NSX-T.
To check whether NSX-T needs to be re-registered:
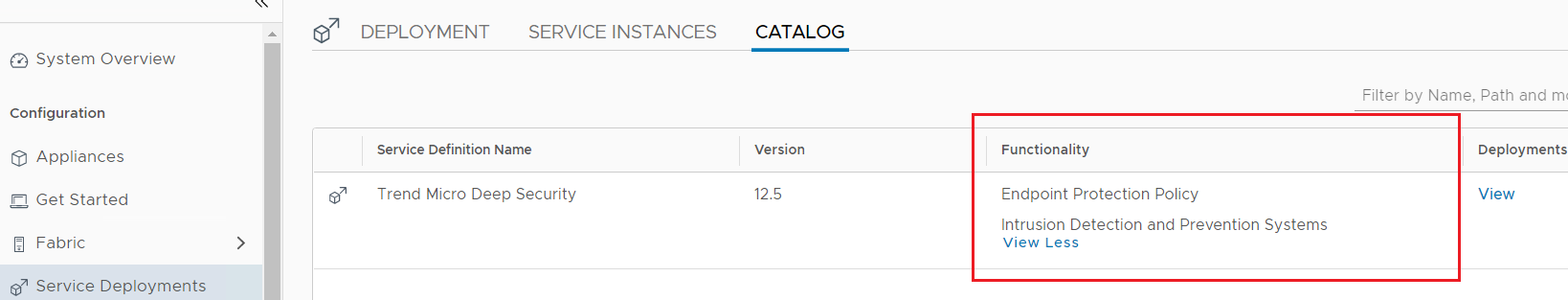
- Go to NSX-T Manager and click System > Service Deployments > CATALOG.
- Make sure both Endpoint Protection Policy and Intrusion Detection and Prevention Systems are present, as shown in the image below. If not, it means a re-registration is required.
To re-register NSX-T:
- Uninstall Deep Security from your NSX environment. See Uninstall Deep Security from your NSX environment for details.
- Re-register NSX in the manager. See Add a VMware vCenter.
Set up communication
- Allow inbound and outbound communication to and from the appliance on the appropriate port numbers. See Deep Security port numbers.
- Make sure the virtual appliance—known as a 'service VM' in VMware terminology—can communicate with the partner Service Manager (console) at the management network level. For details, see Deploy a Service for East-West Traffic Introspection or this NSX-V help page.
(Optional) Install Deep Security Agents
- If the features you want are not available agentlessly, install agents on your VMs and use 'combined mode' so that protection duties are shared by the virtual appliance and agent.
- If you configured guest VMs to have direct access to a network card, install agents on those VMs. In this case there is no opportunity to intercept packets and an in-guest agent is preferable. See Choose agentless vs. combined mode protection for details.
(Optional) Configure high-availability
If you want to use VMware Distributed Resource Scheduler (DRS) for high availability (HA), configure DRS.
Next steps
You are now ready to deploy the appliance. Proceed to one of these pages depending on your VMware environment: