Deep Security Manager 10 has reached end of support. Use the version selector (above) to see more recent versions of the Help Center.
Set up SAP integration
Trend Micro Deep Security supports integration with the SAP NetWeaver platform.
The Trend Micro Deep Security Agent can be called by a library that is automatically deployed on Windows Server 2008 R2 64-bit, Windows Server 2012 R2 64-bit, SUSE Linux Enterprise Server 11 or 12 (SLES) 64-bit, or Red Hat Enterprise Linux 6 or 7 (RHEL) 64-bit operating systems.
This is an overview of the integration steps:
- Install the Deep Security Agent on a Windows Server 2008 R2 64-bit, Windows Server 2012 R2 64-bit, SLES 11 or 12, or RHEL 6 or 7-based SAP application server. See Install the agent .
- Add the SAP server to Deep Security Manager and activate the agent on the SAP server. See Adding the SAP server to the manager.
- Apply a security profile that has anti-malware active to provide the agent with the latest pattern and scan engine. See Assign a security profile.
- Configure the SAP Virus Scan Interface (VSI) by calling the following transactions. See Configure SAP to use the agent:
- VSCANGROUP
- VSCAN
- VSCANPROFILE
- VSCANTEST
Depending on your operating system and environment, the output that you see may differ slightly from what is shown in this article.
Deep Security and SAP components
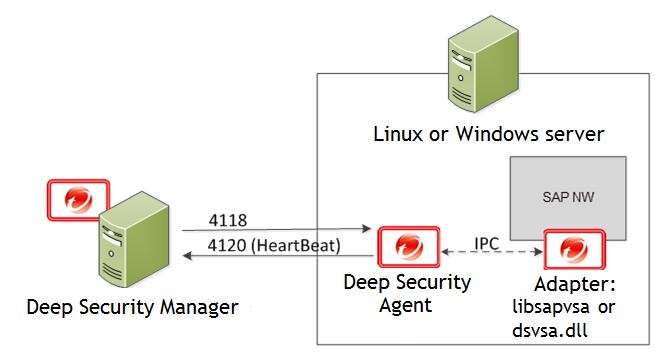
Deep Security Manager connects with the Deep Security Agent located on the SAP NetWeaver server. The agent connects with libsapvsa or dsvsa.dll, which are the virus adapters provided by Trend Micro for scanning purposes.
The components involved in this solution are:
- Deep Security Manager: The centralized web-based management console that administrators use to configure security policy and deploy protection to the Deep Security Agent.
- Deep Security Agent: A security agent deployed directly on a computer. The nature of that protection depends on the rules and security settings that each Deep Security Agent receives from the Deep Security Manager.
- SAP NetWeaver: SAP integrated technology computing platform. The SAP NetWeaver Virus Scan Interface (NW-VSI) provides virus scanning capabilities for third-party products that perform the actual scan. The NW-VSI interface must be activated.
- SAP NetWeaver ABAP WinGUI: A Windows management console used for SAP NetWeaver. In this document, it is used for the configuration of the Deep Security Agent and the SAP NetWeaver Virus Scan Interface.
Install the agent
The Deep Security Agent is installed with core agent functionality only. After the agent is installed on SUSE Linux Enterprise Server or Red Hat Enterprise Linux, you can enable protection modules on the agent. At that point, the plug-ins required for the protection modules will be downloaded and installed.
- Go to the Trend Micro Download Center (http://downloadcenter.trendmicro.com) and download the Deep Security Agent package for your OS.
- Install the agent on the target system. You can use rpm or zypper, depending on the OS. In this example, rpm is used by typing:
rpm -ihv Agent-Core-SuSE_<version>.x86_64.rpm - You should see output similar to what's shown in this example, which indicates that the agent installation is complete:
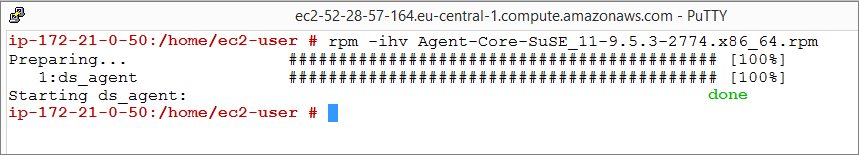
You can also deploy the agent using a deployment script generated from the Deep Security Manager.
Adding the SAP server to the manager
The agent is now installed on the SAP server but no protection modules are active. To enable protection, you need to add the SAP server to the Deep Security Manager console.
Activate SAP in the manager
- In the Deep Security Manager, go to Administration > Licenses.
- Click Enter New Activation Code.
- In the Deep Security Scanner area (under Additional Features), enter your SAP activation code, the click Next and follow the prompts.
In order to use the SAP integration feature, the anti-malware and web reputation modules must also be activated.
Add the SAP server
To add the SAP server, open the Deep Security Manager console and on the Computers tab, click New. There are several ways to add the server, including synchronization with Microsoft Active Directory, VMware vCenter, Amazon Web Services, or Microsoft Azure. You can also add the computer using an FQDN or IP address. For detailed instructions, see Add computers.
Activate the agent
The status of your instance will be either Unmanaged (Activation Required) or Unmanged (Unknown). Next, you will need to activate the agent before the manager can assign rules and policies to protect the computer. The activation process includes the exchange of unique fingerprints between the agent and the manager. This ensure that only one Deep Security Manager can communicate with the agent. There are two ways to activate the agent: agent-initiated or manager-initiated.
Manager-initiated activation
The manager-initiated method requires that the Deep Security Manager can connect to the FQDN or the IP of the agent via the agent's istening port number for heartbeats. This can sometimes be difficult due to NAT port forwarding, firewall, or AWS security groups. To perform manager-initiated activation, go to the Computers tab in the Deep Security Manager console, right-click the instance where the agent is installed and click Actions > Activate.
Agent-Initiated activation
The agent-initiated method requires that the Deep Security Agent can connect to the configured Deep Security Manager address via the manager's listening port number for heartbeats.
You can find the Deep Security Manager address (FQDN or IP) in the Deep Security Manager console, under Administration > Manager Nodes.
You will also need to enable agent-initiated activation from the Deep Security Manager console, by clicking Administration > System Settings > Agents and selecting Allow Agent-Initiated Activation.
Next, use a locally-run command-line tool on the Deep Security Agent to initiate the activation process. The minimum activation instruction contains the activation command and the manager's URL (including the port number):
dsa_control -a dsm://[managerurl]:[port]/
where:
- -a is the command to activate the agent , and
- dsm://managerurl:4120/ is the parameter that points the agent to the Deep Security Manager. ("managerurl" is the URL of the Deep Security Manager, and "4120" is the default agent-to-manager communication port.)
The manager URL is the only required parameter for the activation command. Additional parameters are also available. (For a list of available parameters, see Command-line utilities.)
In the following example, we use the agent-initiated activation by typing:
/opt/ds_agent/dsa_control -a dsm://cetl-dsm.ceur-testlab.trendmicro.de:4120/
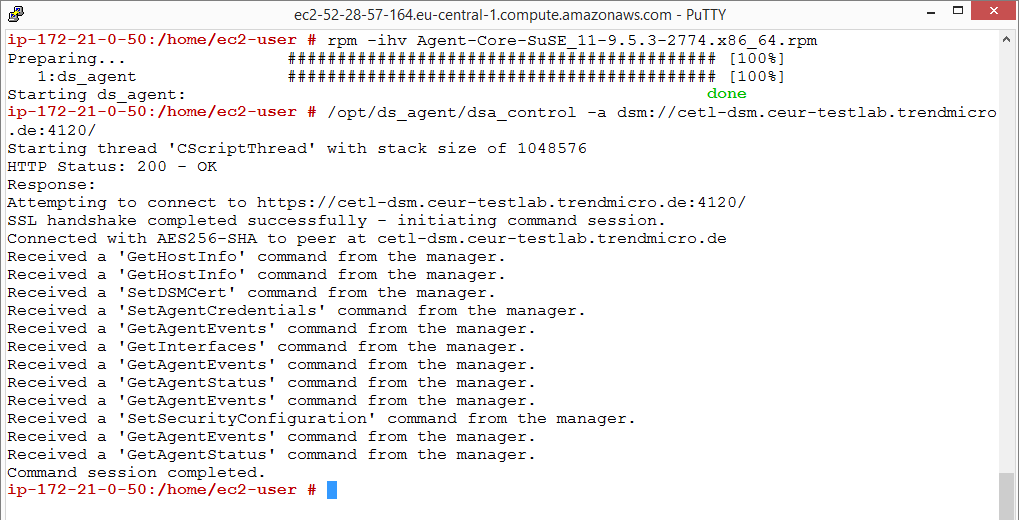
This output indicates that the agent activation is complete.
To confirm the activation:
- In the Deep Security Manager console, go to the Computers tab.
- Click the computer name and then click Details and check that the computer's status is "Managed".
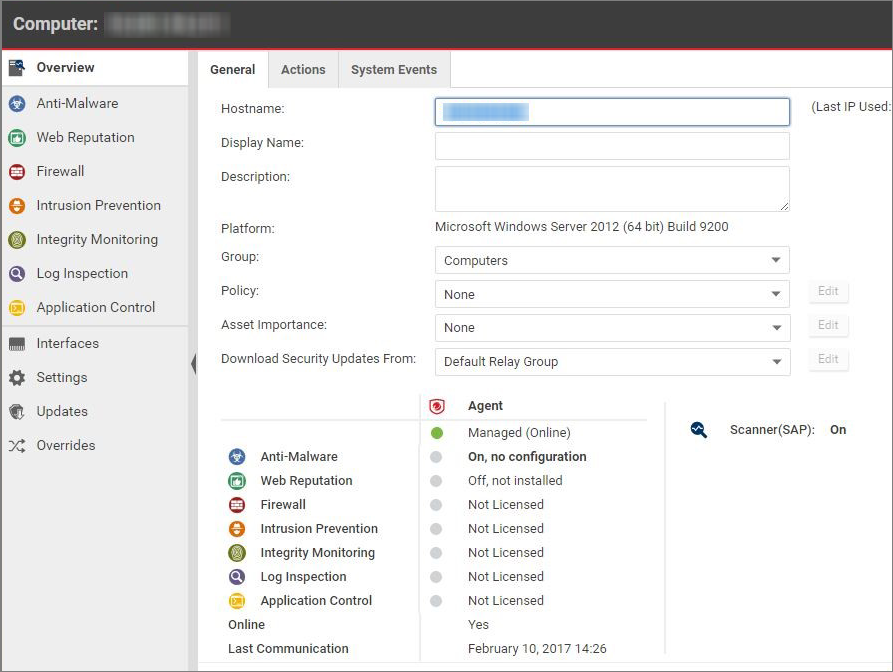
Assign a security profile
At this point, the status of the agent is Managed (Online) but there is no protection module installed. This means that the agent and the manager are communicating but the agent is not using any configuration.
There are several ways to apply protection. In this example, the configuration is done directly on the SAP instance by activating anti-malware and SAP and assigning the default Scan Configurations.
- In the Computer editor
 To open the Computer editor, go to the Computers page and double-click the computer that you want to edit (or select the computer and click Details)., go to Anti-Malware > General.
To open the Computer editor, go to the Computers page and double-click the computer that you want to edit (or select the computer and click Details)., go to Anti-Malware > General. - In the Anti-Malware section, set Configuration to On (or Inherited On) and then click Save.
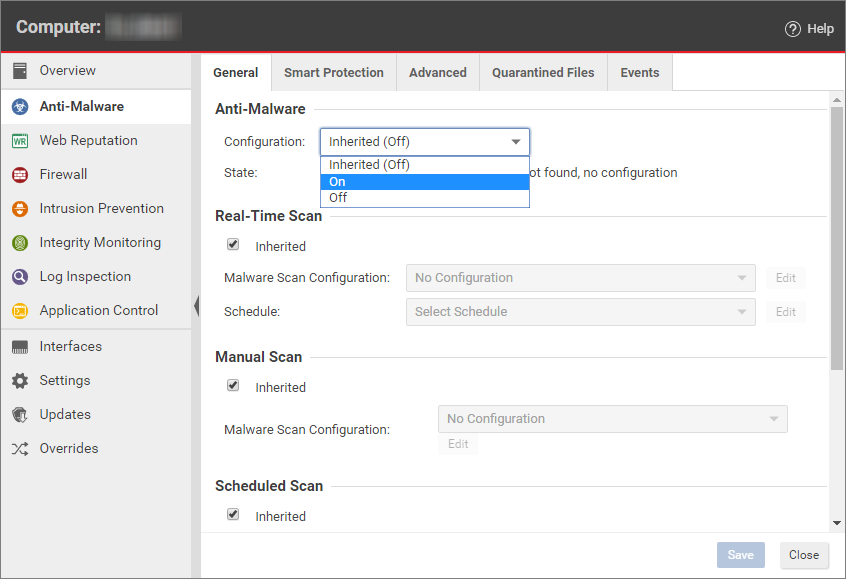
- In the Real-Time Scan, Manual Scan, or Scheduled Scan sections, set the Malware Scan Configuration and Schedule, or allow those settings to be inherited from the parent policy.
- Click Save. The status of the anti-malware module changes to Off, installation pending. This means that the agent is retrieving the required module from the Deep Security Manager. For this to work, the client needs to access the Deep Security Relay on the relay's listening port number. A few moments later, the agent should start downloading security updates such as anti-malware patterns and scan engines.
- In the Computer editor, go to Settings > Scanner.
- In the SAP section, set Configuration to On (or Inherited On) and then click Save.
After status of the agent changes to Managed (Online) again and the anti-malware and Scanner (SAP) modules are On, you can proceed with the SAP configuration.
Configure SAP to use the agent
The Deep Security Agent is now up and running and is able to scan the file system of its operating system. Next, we need to make the agent aware of the SAP application server. To use this, we must create a virus scan adapter inside the application server. The virus scan adapter must be part of a group. After the virus scan adapter and virus scan group are created, we can use virus scan profiles to configure what to scan and how to behave.
These are the required steps:
- Configure the Trend Micro scanner group
- Configure the Trend Micro virus scan provider
- Configure the Trend Micro virus scan profile
- Test the virus scan interface
The virus scan group and the virus scan adapter are both global configurations (client 00). The virus scan profile must be configured in each tenant (client 01, 02, etc.).
Configure the Trend Micro scanner group
- In the SAP WinGUI, run the VSCANGROUP transaction.
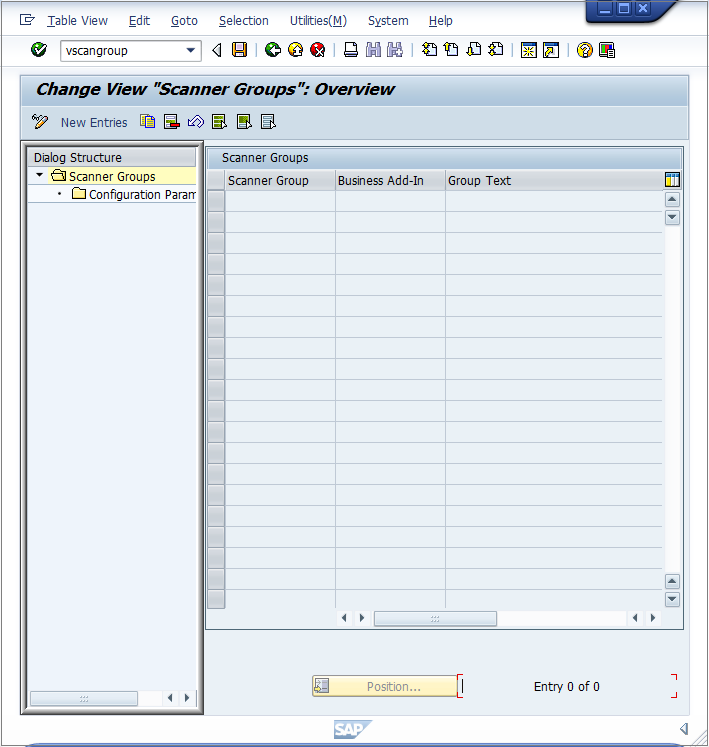
- In Edit mode, click New Entries. Create a new scanner group, specifying a group name in the Scanner Group area and a description of the scanner group in the Group Text area.
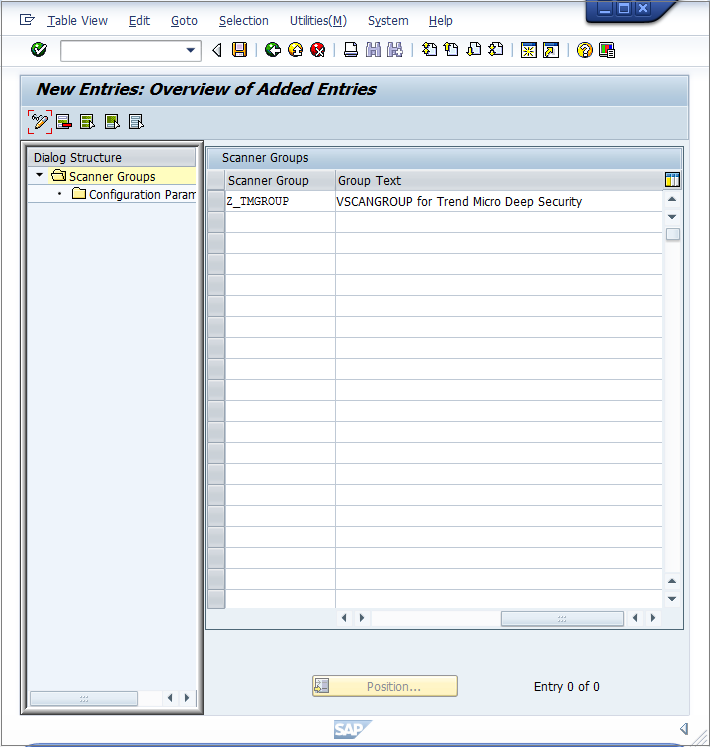
- Clicking Save or leaving the edit mode will prompt you to commit a “workbench request”. In this example, a new workbench request is created to keep track of all the VSI-related changes:
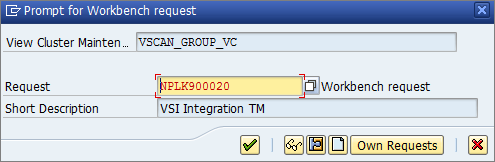
The next step is the actual configuration of the VSI integration. It is called a Virus Scan Adapter.
Configure the Trend Micro virus scan provider
- In the SAP WinGUI, run the VSCAN transaction.
- In Edit mode, click New Entries. Creating a new entry displays a prompt in which the configuration of the VSI- certified solution takes place. In this example, the following configuration parameters are set:
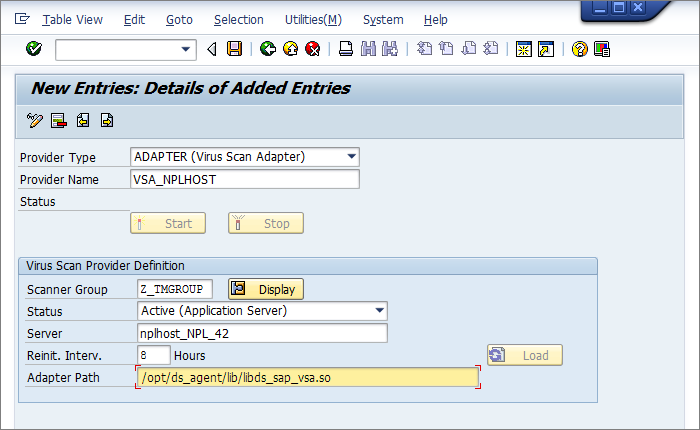
Setting Value Description Provider Type ADAPTER (Virus Scan Adapter) Automatically set (default) Provider Name VSA_<host name> Automatically set, serves as alias Scanner Group Select the group that you configured earlier All previously created scanner groups, which you can display using the input help Status Active (Application Server) Automatically set (default) Server nplhost_NPL_42 Automatically set, hostname Reinit. Interv. 8 Hours Specifies the number of hours after which the Virus Scan Adapter will be reinitialized and load new virus definitions. Adapter Path (Linux) /lib64/libsapvsa.so Default path Adapter Path (Windows) C:\Program Files\Trend Micro\Deep Security Agent\lib\dsvsa.dll Default path - When you click Save or leave the edit mode, there is another prompt to pack this into a workbench request. After confirming, click the Start button. The Status light will turn green, which means the adapter is loaded and active:
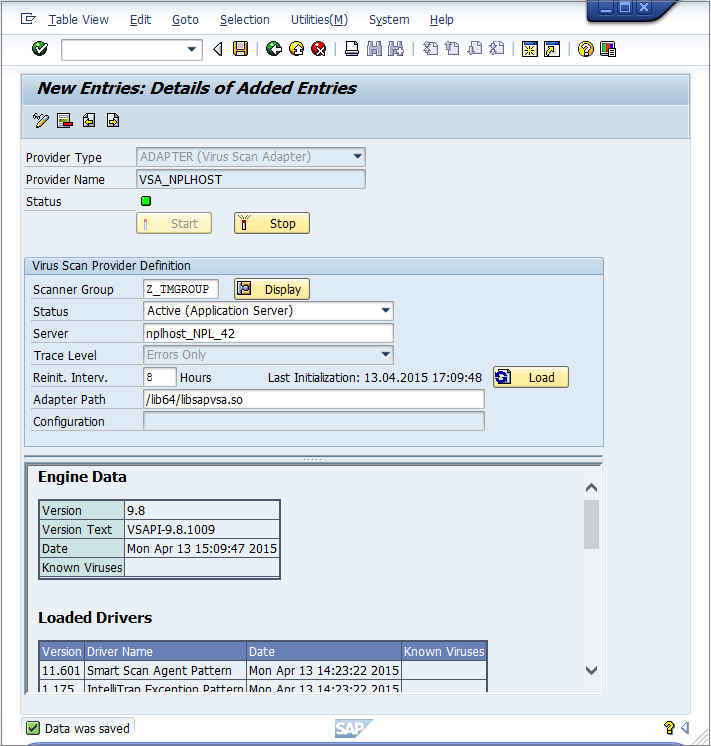
At this point, the VSI configuration is nearly finished. The application server is now ready to process file transactions using a virus scan provided by Trend Micro Deep Security.
Configure the Trend Micro virus scan profile
- In the SAP WinGUI, run the VSCANPROFILE transaction, then select the SAP operation that requires virus scan. For example, check the "Active" checkbox for /SCET/GUI_UPLOAD or /SCET/GUI_DOWNLOAD and then click Save.
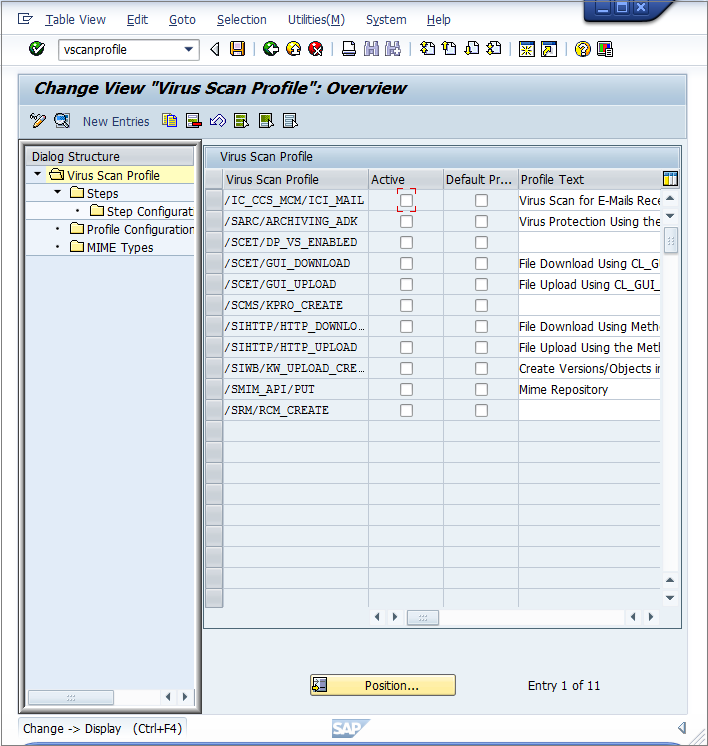
- In Edit mode, click New Entries. The virus scan profiles will define how specific transactions (file uploads, file downloads, etc.) are handled corresponding to the virus scan interface. To have the previously configured virus scan adapter used in the application server, a new virus scan profile needs to be created:
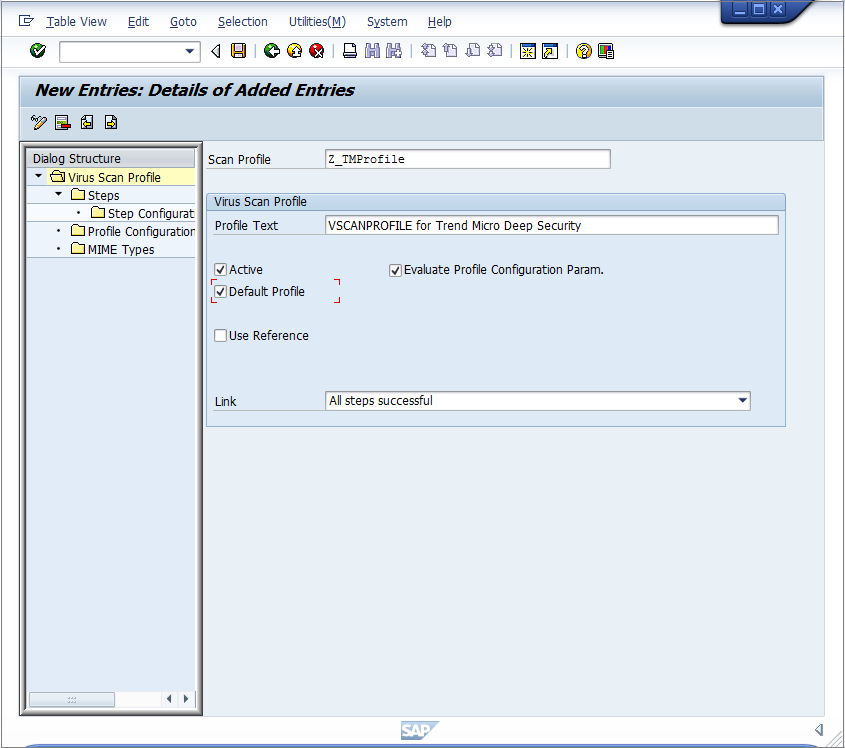
- In the Scan Profile box, enter "Z_TMProfile" and select the Active, Default Profile, and Evaluate Profile Configuration Param check boxes.
- While still in edit mode, double-click Steps to configure the steps:
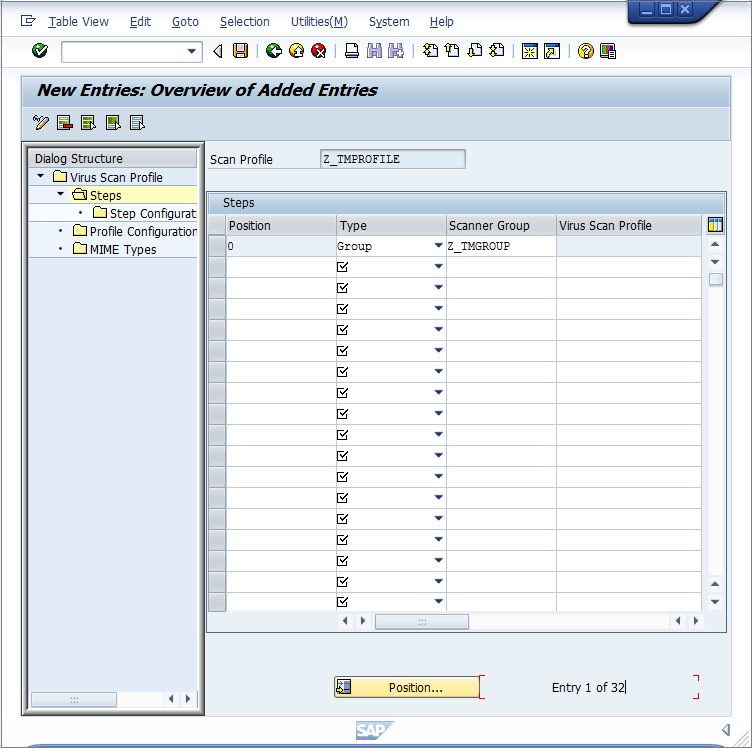
- Click New Entries.
- The steps define what to do when the profile is called by a transaction. Set the Position to "0", Type to "Group" and the Scanner Group to the name of the group that you configured earlier.
- After clicking Save or leaving the edit mode, you will eventually receive a notification about an existing virus scan profile, /SCET/DP_VS_ENABLED. you can ignore this notification because the profile is not active and is not used. After confirming this notification, you will be asked to pack this configuration in a “customization request”. Creating a new request will help keep track of the changes that have been made:
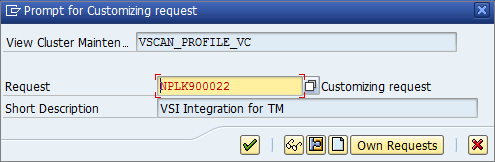
- To create configuration parameters for a step, double-click the Profile Configuration Parameters node. Click New Entries and set the parameters:
Parameter Type Description CUST_ACTIVE_CONTENT BOOL Check whether a file contains script (JavaScript, PHP, or ASP script) and block CUST_CHECK_MIME_TYPE BOOL Check whether the file extension name matches its MIME type. If they do not match, the file will be blocked. All MIME types and extension names can be exactly matched. For example: - Word files must to be .doc or .dot
- JPEG files must to be .jpg
- Text and binary files could be any extension (won’t block)
See Supported MIME types.
- Double-click the Step Configuration Parameters node. Click New Entries and set the parameters:
Parameter Type Description SCANBESTEFFORT BOOL The scan should be performed on the “best effort” basis; that is, all (security critical) flags that allow a VSA to scan an object should be activated, such as SCANALLFILES and SCANEXTRACT, but also internal flags. Details about exactly which flags these are can be stored in the certification. SCANALLFILES BOOL Scans for all files regardless of their file extension. SCANEXTENSIONS CHAR List of the file extensions for which the VSA should scan. Only files with the configured extensions will be checked. Other extensions are blocked. Wildcards can also be used here in order to search for patterns. * stands for this location and following and ? stands for for only this character. The syntax is: exe;com;do?;ht* => `*` therefore means to scan all files. SCANLIMIT INT This settings applies to compressed files. It specifies the maximum number of files that will be unpacked and scanned. SCANEXTRACT BOOL Archives or compressed objects are to be unpacked SCANEXTRACT_SIZE SIZE_T Maximum unpack size SCANEXTRACT_DEPTH INT Maximum depth to which an object is to be unpacked. SCANMIMETYPES CHAR List of the MIME types to be scanned for. Only files with configured MIME types will be checked. Other MIME types are blocked. This parameter works only if CUST_CHECK_MIME_TYPE is enabled. BLOCKMIMETYPES CHAR List of MIME types to be blocked. This parameter works only if CUST_CHECK_MIME_TYPE is enabled. BLOCKEXTENSIONS CHAR List of file extensions to be blocked
This configuration is per-client, so it must be done in each tenant of the SAP application server.
Test the virus scan interface
- In the SAP WinGUI, run the VSCANTEST transaction.
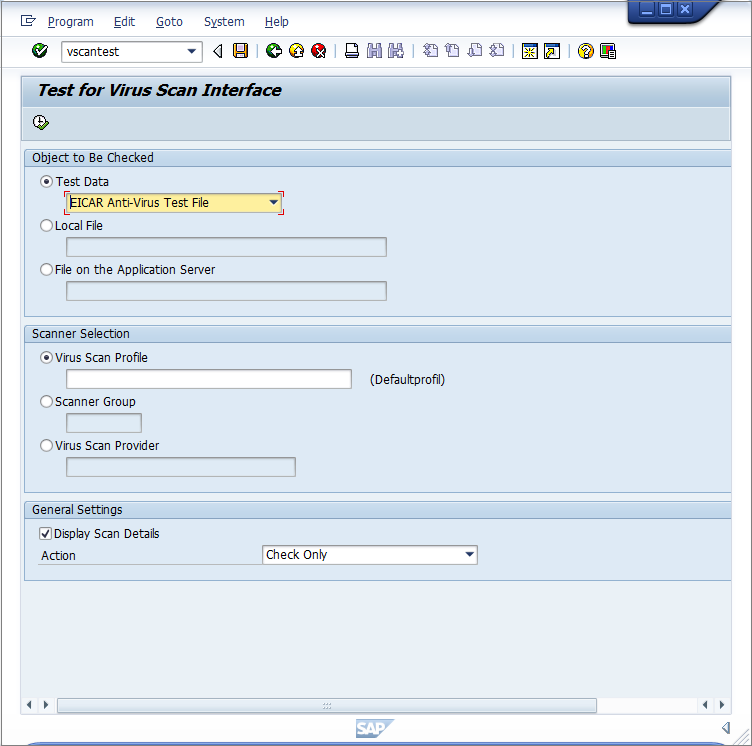
- Every VSI-aware SAP application server also has a built-in test to check whether the configuration steps were done correctly. For this, an EICAR test virus (www.eicar.org) is packed in a transaction that can call a specific scanner. Not filling in anything will call the default profile, which was configured in the last step.
- Clicking Execute prompts a notification that explains what an EICAR test virus is. After confirming this, you will see how the transaction is intercepted:
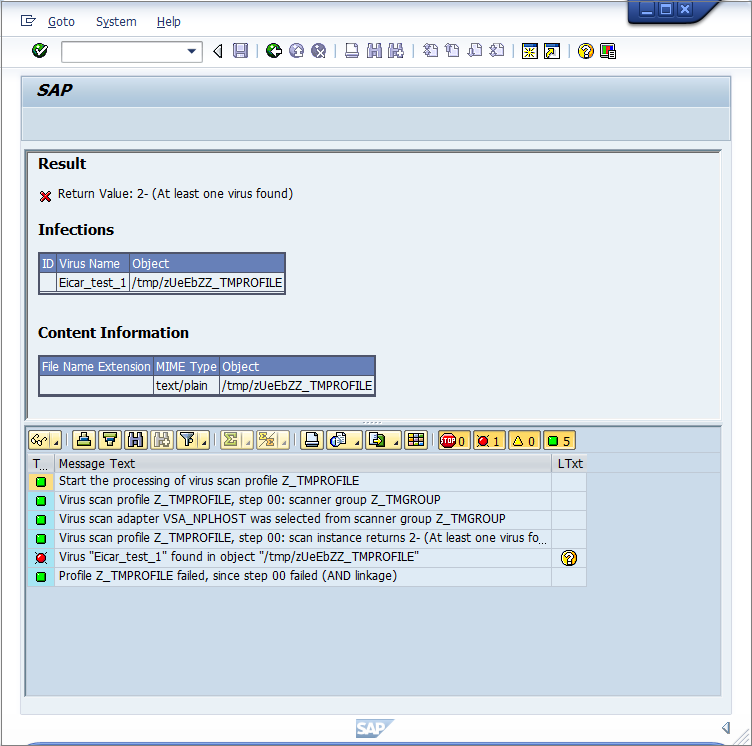
Infections shows information about the detected malware.
Content Information shows the correct MIME-type of the file.
The file name is always a randomly generated 7-letter alphabetic string followed by the virus scan profile name.
After this, there is an output about each step of the transaction:
- The transaction called the default virus scan profile, which is the virus scan profile Z_TMPROFILE.
- The virus scan profile Z_TMPROFILE is configured to call an adapter from the virus scan group Z_TMGROUP.
- The virus scan group Z_TMGROUP has multiple adapters configured and calls one of them (in this case, VSA_NPLHOST).
- The virus scan adapter returns value 2-, which means a virus was found.
- Information about the detected malware is displayed by showing Eicar_test_1 and the file object /tmp/ zUeEbZZ_TMPROFILE.
- The called default virus scan profile Z_TMPROFILE fails because step 00 (the virus scan group) was not successful and therefore the file transaction is stopped from further processing.
For a cross-check, there is also information about this “malware” event in the Deep Security Manager console. To see the event, open the Computer editor![]() To open the Computer editor, go to the Computers page and double-click the computer that you want to edit (or select the computer and click Details). and click Anti-Malware > Events.
To open the Computer editor, go to the Computers page and double-click the computer that you want to edit (or select the computer and click Details). and click Anti-Malware > Events.
Supported MIME types
The MIME types supported by Deep Security Scanner vary depending on which version of the Deep Security Agent you are using.
| MIME Type | Description | Extension | Supported in 9.6 Agent (VSAPI 9.85) |
Supported in 10.0 Agent (ATSE 9.861) |
| application/octet-stream | * | Yes | Yes | |
| application/com | COM File | com | Yes | Yes |
| application/ecmascript | EMCScript File | es | Yes | Yes |
| application/hta | HTA File | hta | Yes | Yes |
| application/java-archive | Java Archive (JAR) file | jar | Yes | Yes |
| application/javascript | Javascript File | js, jsxinc, jsx | Yes | Yes |
| application/msword | Word for Windows | doc, dot | Yes | Yes |
| application/vnd.ms-access | MS Access | mdb | No | No |
| application/vnd.ms-project | MS Project | mpp | No | No |
| application/msword | MS Word | doc, dot | Yes | Yes |
| application/octet-stream | COM File | com | Yes | Yes |
| application/octet-stream | EXE File | exe | Yes | Yes |
| application/pdf | Adobe Portable Document Format file | Yes | Yes | |
| application/postscript | Postscript | ai | Yes | Yes |
| application/postscript | Postscript | ps | Yes | Yes |
| application/postscript | Postscript | ps | Yes | Yes |
| application/rar | RAR File | rar | Yes | Yes |
| application/rtf | Microsoft RTF | rtf | Yes | Yes |
| application/sar | Sar File | sar | Yes | Yes |
| application/vnd.ms-excel | Excel for Windows | xls, xlt, xla | Yes | Yes |
| application/vnd.ms-outlook | Outlook for Windows | msg | No | Yes |
| application/vnd.ms-powerpoint | Windows PowerPoint | ppt, pot, pps, ppa | Yes | Yes |
| application/vnd.ms-publisher | MS Publisher | pub | No | No |
| application/vnd.oasis.opendocument | Open Document | odf | Yes | Yes |
| application/vnd.openxmlformats-officedocument.presentationml.presentation | MS Office File | pptx, potx, ppsx, ppam, pptm, potm, ppsm | Yes | Yes |
| application/vnd.openxmlformats-officedocument.spreadsheetml.sheet | MS Office File | xlsx, xltx, xlsm, xltm, xlam, xlsb | Yes | Yes |
| application/vnd.openxmlformats-officedocument.wordprocessingml.document | MS Office File | docx, dotx, docm, dotm | Yes | Yes |
| application/vnd.rn-realmedia | Real Media | rm | Yes | Yes |
| application/wordperfect | WOrdPerfect | wp, wp5, wp6, wpd, w60, w61 | Yes | Yes |
| application/x-alf | alf | Yes | Yes | |
| application/x-arc-compressed | ARC File | arc | Yes | Yes |
| application/x-bzip2 | bZIP File | * | Yes | Yes |
| application/x-cpio | CPIO File | * | Yes | Yes |
| application/x-director | Macromedia Director Shockwave Movie | dcr | Yes | Yes |
| application/x-gzip | Gzip | * | Yes | Yes |
| application/xhtml+xml | XHTML | dhtm, dhtml, htm, html, htx, sht, shtm, shtml, stml, xht, xhtm, xhtml, xml, txt | Yes | Yes |
| application/x-java-class | JAVA Applet | class | Yes | Yes |
| application/x-kep | kep | Yes | Yes | |
| application/x-otf | otf | Yes | Yes | |
| application/x-sapshortcut | sap, sapc | Yes | Yes | |
| application/x-shockwave-flash | Macromedia Flash | swf | Yes | Yes |
| application/x-silverlight-app | PKZIP | xap | Yes | Yes |
| application/x-sim | sim | Yes | Yes | |
| application/x-tar | TAR File | tar | Yes | Yes |
| application/x-vbs | * | Yes | Yes | |
| application/zip | ZIP File | zip, zipx | Yes | Yes |
| audio/basic | Audio | snd, au | Yes | Yes |
| audio/midi | MIDI | mid, midi, rmi, mdi, kar | Yes | Yes |
| audio/x-aiff | Audio InterChange File Format from Apple/SGI | aiff, aif, aifc | Yes | Yes |
| audio/x-mpeg-3 | MP3 | mp3 | Yes | Yes |
| audio/x-realaudio | Real Audio | ra | Yes | Yes |
| audio/x-voc | Creative Voice Format(VOC) | voc | Yes | Yes |
| image/bmp | Windows BMP | bmp | Yes | Yes |
| image/gif | GIF | gif | Yes | Yes |
| image/ico | Windows Icon | ico | Yes | Yes |
| image/jpeg | JPEG | jpg, jpeg, jpe, jif, jfif, jfi | Yes | Yes |
| image/msp | Microsoft Paint | msp | Yes | Yes |
| image/png | Portable Network Graphics | png | Yes | Yes |
| image/ppm | PPM image | ppm | Yes | Yes |
| image/svg+xml | svg | Yes | Yes | |
| image/tiff | TIFF | tif, tiff | Yes | Yes |
| image/vnd.ms-modi | Microsoft Document Imaging | mdi | Yes | Yes |
| image/x-cpt | Corel PhotoPaint | cpt | Yes | Yes |
| image/x-pcx | PCX | pcx | Yes | Yes |
| image/x-pict | Macintosh Bitmap | pct | Yes | Yes |
| image/x-ras | Sun Raster(RAS) | ras | Yes | Yes |
| image/x-wmf | Windows Metafile | wmf | Yes | Yes |
| text/csv | CSV | csv, txt | Yes | Yes |
| text/html | HTML | dhtm, dhtml, htm, html, htx, sht, shtm, shtml, stml, xht, xhtm, xhtml, xml, txt | Yes | Yes |
| text/plain | * | Yes | Yes | |
| text/plain | Text File | txt | Yes | Yes |
| text/xml | XML | dhtm, dhtml, htm, html, htx, sht, shtm, shtml, stml, xht, xhtm, xhtml, xml, txt | Yes | Yes |
| text/xsl | XSL | xsl | Yes | Yes |
| unknown/unknown | * | Yes | Yes | |
| video/mpeg | * | Yes | Yes | |
| video/quicktime | Quick Time Media | qt | Yes | Yes |
| video/x-fli | AutoDesk Animator | fli | Yes | Yes |
| video/x-flv | Macromedia Flash FLV Video | flv | Yes | Yes |
| video/x-ms-asf | Advanced Streaming Format | asf | Yes | Yes |
| video/x-scm | Lotus ScreenCam Movie | scm | Yes | Yes |