Deep Security Manager 10 has reached end of support. Use the version selector (above) to see more recent versions of the Help Center.
Enable application control
This is new in Deep Security 10.
Application control is designed for software change management that is easy—even on thousands of computers—with no business disruption or high workload.



Application control detects change to executables, such as:
- Users installing unwanted software
- New PHP pages, Python scripts, or Java applications
- Unscheduled auto-updates
- Zero-day ransomware
Once detecting changes, you can optionally lock down the computer to block unauthorized software.
To use application control, the basic steps are:
- Install all of the computer's normal software, including installing the Deep Security agent
-
Red Hat Linux 6 or 7 or Amazon Linux is required. Additional Linux distribution and Microsoft Windows support for application control will be added in a future release.
Proxies are not supported, and will not work in many topologies. Proxy support will be added in a future release. - Monitor for application control events
- Allow or block software (unless locked down)
- During maintenance windows, allow the software update
For more information, see:
Turn on application control
To roll out application control gradually, enable application control on one or a few computers at a time.
-
Install Deep Security Agent 10.0 or later. (Application control does not support agentless topologies).
Also remove software that you want to block, and install normal software if it's missing.
Before you start, verify that unwanted software is not currently installed. Enabling application control will add all currently installed software to the allow rules — even if it is insecure, or malware. If you are not sure what is installed, the safest way is to make a clean install, and then enable application control.If a computer's software normally changes frequently, even without a maintenance window — such as with development build servers — then don't use application control. (Alternatively, enable app control, but use the API in your DevOps build pipeline to enable maintenance mode during builds.)
For details, see Reset application control after too much software change.
- Activate the agent. You may also need to activate the application control license.
-
In Deep Security Manager, go to Computer or Policy editor
 You can change these settings for a policy or for a specific computer.
To change the settings for a policy, go to the Polices page and double-click the policy that you want to edit (or select the policy and click Details).
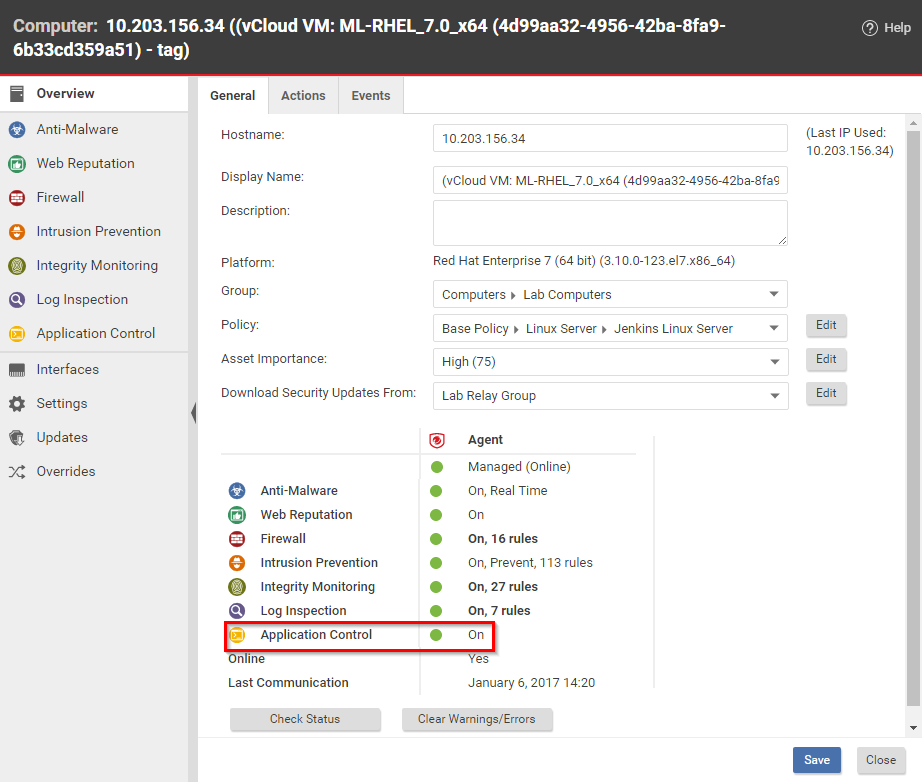
To change the settings for a computer, go to the Computers page and double-click the computer that you want to edit (or select the computer and click Details). > Application Control > General.
You can change these settings for a policy or for a specific computer.
To change the settings for a policy, go to the Polices page and double-click the policy that you want to edit (or select the policy and click Details).
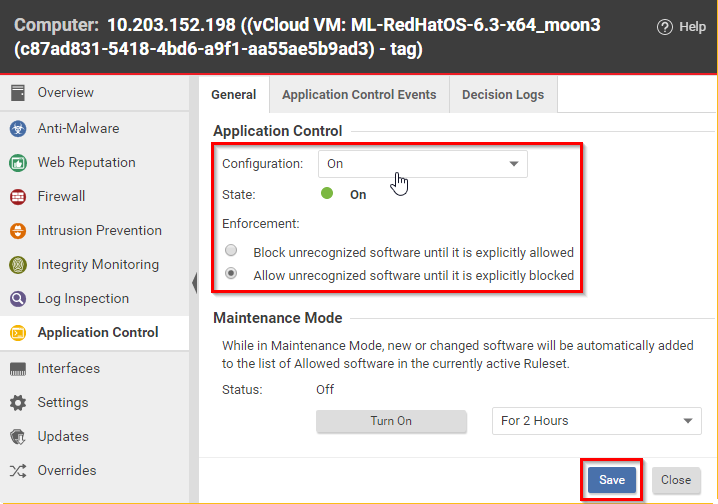
To change the settings for a computer, go to the Computers page and double-click the computer that you want to edit (or select the computer and click Details). > Application Control > General.Enable the application control engine by selecting On or Inherited (On).
If you want exactly the same ruleset to apply to many identical computers (even in the future), use shared rules created via API.
-
If you want to automatically block all new or changed software until you make an allow or block rule, select Block unrecognized software until it is explicitly allowed.
Some software such as web hosting software, Microsoft Exchange, and Oracle PeopleSoft can change its own files. In those cases, instead of a complete lockdown, select Allow unrecognized software until it is explicitly blocked so that the software's self-change isn't automatically blocked. Then manually add block rules for unwanted software if it is detected. - If you created a ruleset that multiple computers will use via API , select the shared ruleset.
-
Click Save.
The next time that Deep Security Manager and the agent connect, it will enable application control engine on the computer, and either make local, initial allow rules based on currently installed software, or download a shared ruleset. Time required varies by:
- heartbeat interval and bi-drectional communications
- number of files
- computer's disk and CPU speed (local rulesets only)
- bandwidth (shared rulesets only)
- number of routers, firewalls, or proxies in between with limited system resources (shared rulesets only)
- ruleset deployment via relay (shared rulesets only)
 Application control will not allow or block software until it has either a shared ruleset or initial local rules built from the inventory.In Deep Security Agent 10.0 GA and earlier, agents didn't have support for connections through a proxy to relays. If the ruleset download fails due to a proxy, and if either your agents require a proxy to access the relay or manager, then you must either:
Application control will not allow or block software until it has either a shared ruleset or initial local rules built from the inventory.In Deep Security Agent 10.0 GA and earlier, agents didn't have support for connections through a proxy to relays. If the ruleset download fails due to a proxy, and if either your agents require a proxy to access the relay or manager, then you must either:- update agents' software, then configure the proxy
- bypass the proxy
- change the application control rulesets relay setting as a workaround
When application control is enabled, and has finished its initial software inventory scan:
- The State field indicates "On" or "On, Blocking unrecognized software".
- On Computers, the Status field changes from "Application Control Ruleset Build In Progress" to "Managed (Online)".
- Events & Reports > Events > System Events will record “Application Control Ruleset Build Started” and “Application Control Ruleset Build Completed”. (If you don’t see any logs, see Choose which application control events to log.)
-
To verify that application control is working, either copy an executable to the computer, or add execute permissions to a plain text file. Try to run the executable.
Depending on your enforcement setting for unrecognized software, it should be either blocked or allowed. Once app control has built initial allow rules or downloaded a shared ruleset, if any change is detected, it should appear in the Actions tab, which you can use to create allow and block rules. Depending on your alert configuration, you will also see an alert if unrecognized software is detected, or if application control blocks software from launching. The event should persist until the software change no longer exists, or until the oldest data has been pruned from the database.
Add an allow or block rule for your test software, and then try again. This time, app control should apply your allow or block rule.
If software is accidentally blocked because you've selected Block unrecognized software until it is explicitly allowed and the software isn't being recognized, the Reason column in app control event logs can help you to troubleshoot the cause.
If more computers will be added in the future, continue with Automatically enable application control on new computers. If they will be identical, see also Reuse shared allow and block rules on other computers.
When you patch a computer, update a golden image, or push to production, remember to enable Maintenance Mode to add new or changed software to your ruleset. For details, see Allow software updates.
Automatically enable application control on new computers
- If you don’t yet have a policy that applies application control to multiple computers, follow the steps in Turn on application control, but configure it on Policies, not Computers.
- Go to Administration > Event-Based Tasks.
-
Either:
- Select the row for an existing event-based task that triggers when new computers are detected and then click Properties, or
- Click New to create a new task that triggers for either Agent-Initiated Activation or Computer Created.
-
Select a policy where application control is enabled.
The next time that Deep Security Manager and the agent connect, the agent will download the policy with its application control settings. If using a shared ruleset, the computer must also download the shared ruleset. Time required varies by:
- heartbeat interval and bi-drectional communications
- number of files
- computer's disk and CPU speed (local rulesets only)
- bandwidth (shared rulesets only)
- number of routers, firewalls, or proxies in between with limited system resources (shared rulesets only)
- ruleset deployment via relay (shared rulesets only)
When applying the same policy to multiple computers, it will apply the same application control enforcement settings, but not the same ruleset unless you have selected a shared ruleset. This means that although the policy enables application control on many computers, by default, they will each generate their own local ruleset. Therefore you could accidentally allow an application on one computer, but block it on another computer. If you want software to be blocked or allowed in the same way on all computers, then you create and apply a shared ruleset.