Deep Security 12 FR has reached end of support. Use the version selector (above) to see more recent versions of the Help Center.
Configure DPDK mode
Trend Micro supports this feature on NSX-T Data Center 3.x only.
Intel Data Plane Development Kit (DPDK) is a collection of open-source libraries that have been integrated into VMware to speed up packet processing for services that use VMware Network Introspection. In the case of Deep Security, these services are Firewall, Intrusion Prevention, and Web Reputation.
To take advantage of the performance improvements offered by DPDK, you can configure the Deep Security Virtual Appliance in DPDK mode, as follows.
Before you begin:
- Review Deep Security Virtual Appliance requirements. There are specific requirements for DPDK mode.
- Make sure you have configured DPDK in VMware. See this VMWare DPDK document for an overview.
- Understand that DPDK mode is configured during the appliance deployment. If you already have an appliance up and running, you'll need to redeploy it.
Configure DPDK mode:
- Start the appliance deployment (see Deploy the appliance (NSX-T 3.x)) and stop when you get to Configure and start the service deployment under Install the appliance on NSX-T 3.x.
- Click Configure Attributes.
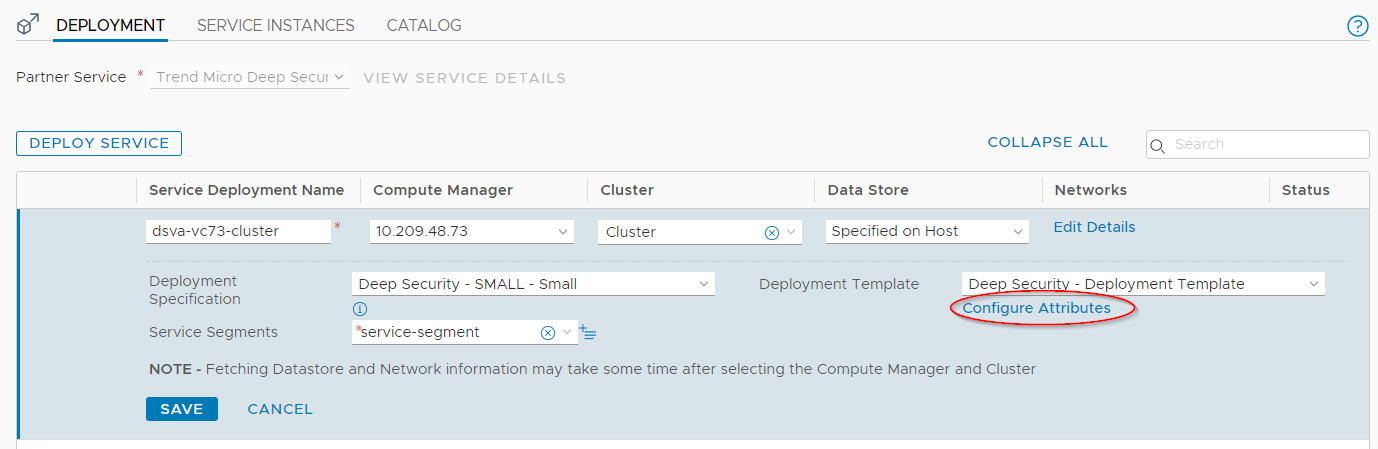
The Configure Attributes dialog box appears.
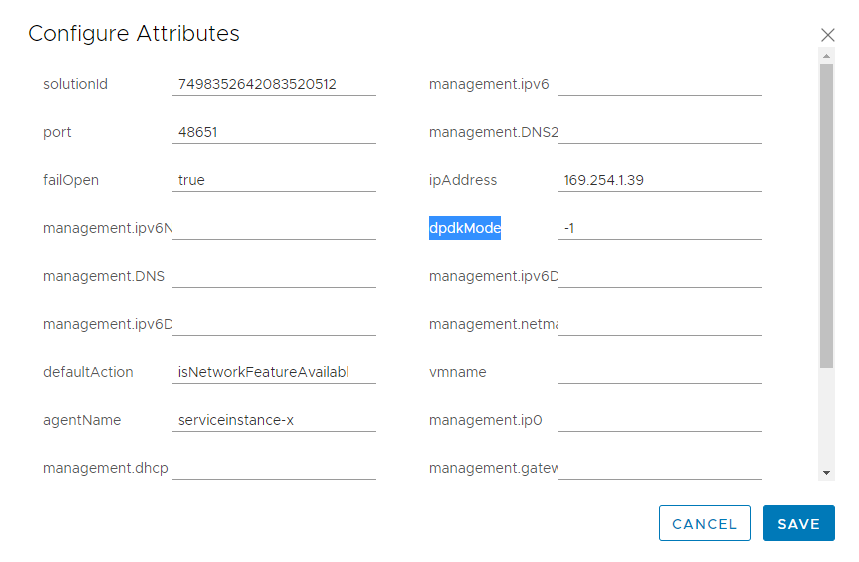
- Find the dpdkMode field and modify the value according to your ESXi host resource and the size of Deep Security Virtual Appliance. The possible values are:
- -1: Deep Security Virtual Appliance determines the optimal CPU usage for the DPDK mode.
- 0 (default): Disables DPDK mode. Deep Security Virtual Appliance uses the RAW Socket mode for Network Introspection.
- 1: Deep Security Virtual Appliance occupies 1 CPU in DPDK mode (if the appliance has 2 CPUs and above)
- 2: Deep Security Virtual Appliance occupies 2 CPUs in DPDK mode (if the appliance has 4 CPUs and above)
- 4: Deep Security Virtual Appliance occupies 4 CPUs in DPDK mode (if the appliance has 8 CPUs and above)
- <custom_integer>: Deep Security Virtual Appliance occupies a custom number of CPUs in DPDK mode.
- Click SAVE to start the appliance deployment.
- Monitor and verify your deployment following the instructions in Monitor and verify the deployment