Update the load balancer's certificate
Usually, your browser should warn you with a certificate validation error whenever you try to connect to a server with a self-signed certificate. This is because with any self-signed certificate, the browser cannot automatically validate the certificate's signature with a trusted third party certificate authority (CA), and therefore the browser doesn't know if the certificate was sent by an attacker or not. When installed, Deep Security Manager is initially configured to use a self-signed certificate for HTTPS connections (SSL or TLS), so you must manually verify that the server certificate fingerprint used to secure the connection belongs to your Deep Security server. This is normal until you replace the self-signed certificate with a CA-signed certificate.
The same error will occur if you have an AWS Elastic Load Balancer (ELB) or other load balancer, and it presents a self-signed certificate to the browser.
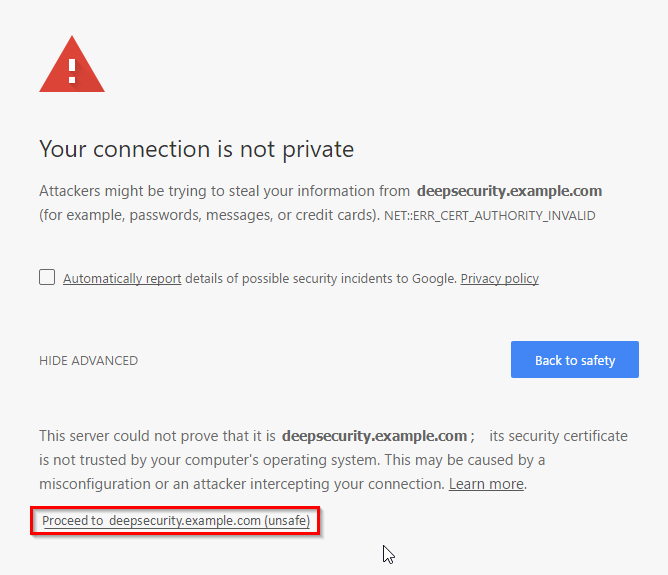
You can still access Deep Security Manager if you ignore the warning and proceed (method varies by browser). However, this error will occur again each time you connect, unless you either:
- add the certificate to your computer's store of trusted certificates (not recommended) or
- replace the load balancer's certificate with one signed by a trusted CA (strongly recommended)
-
With a CA that is trusted by all HTTPS clients, register the fully qualified domain name (not IP address) that administrators, relays, and agents will use to connect to Deep Security Manager.
Specify the sub-domain (for example, deepsecurity.example.com) that will uniquely identify Deep Security Manager. For nodes behind an SSL terminator load balancer, this certificate will be presented to browsers and other HTTPS clients by the load balancer, not by each Deep Security Manager node.
When the CA signs the certificate, download both the certificate (with public key) and the private key.
Store and transmit the private key securely. If file permissions or unencrypted connections allow a third party to access your private key, then all connections secured by that certificate and key are compromised. You must revoke that certificate, remove the key, and get a new certificate and key. - Add the certificate to your certificate store (optional if your computer trusts the CA that signed the certificate).
- Update the DNS settings of the load balancer to use the new domain name.
- Replace the SSL certificate of the load balancer.