Automatically assign policies using cloud provider tags/labels
AWS tags, Azure tags, and GCP labels allow you to categorize your resources by assigning metadata to AWS EC2 instances, Azure VMs, or GCP VM instances in the form of keys and values. You can also tag Amazon WorkSpaces with the similar key and value pair. Deep Security can use this metadata to trigger the automatic assigning of a policy to a Deep Security Agent when that agent is activated. This is done by creating an event-based task in Deep Security and defining the event, policy, and metadata. Event-based tasks are used to monitor protected resources for specific events and then perform tasks based on certain conditions: in this case the event is agent-initiated activation and a specific AWS instance tag is the condition.
This article describes how to do this using the following examples:
- Policy: AIA_Policy
- AWS tag key: Group
- AWS tag value: development
The example below is based on the assumption that the policy AIA_Policy has already been created.
- Go to Administration -> Event-Based Tasks in the Deep Security Manager console and click New.
- Select Agent-Initiated Activation from the Event list and click Next.
- Select the Assign Policy check box, select AIA_Policy from the list, and click Next.
- Select Cloud Instance Metadata from the list, type Group in the key field, and development into the value field.
- (Optional) To restrict the scope to only one cloud vendor, select Cloud Vendor from the list and select AWS, Azure, or GCP as the matching criteria. If you want to apply the rule to all three, don't define the Cloud Vendor condition.
- Click Next.
- Type and name for the event-based task and click Finish to save it.
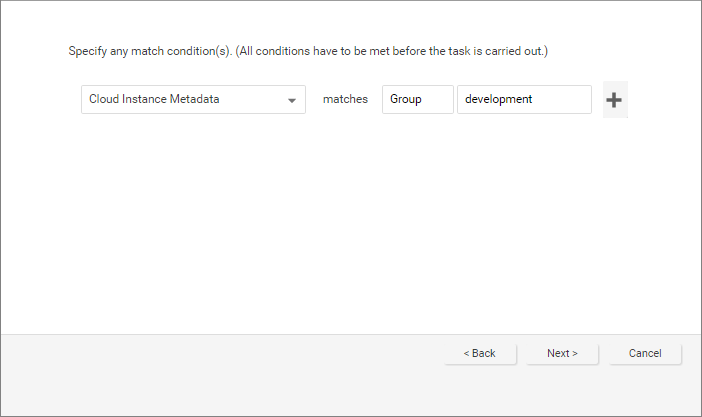
You have now created an event-based task that will apply the AIA_Policy to an instance tagged with the key "Group" and the value "development" when the agent is activated on that instance.