Deep Security Manager 10 has reached end of support. Use the version selector (above) to see more recent versions of the Help Center.
Set up log inspection
The log inspection protection module helps you to identify important events that may be buried in your operating system and application logs. These events can be sent to a security information and event management (SIEM) system or centralized logging server for correlation, reporting, and archiving. All events are also securely collected in the Deep Security Manager.
For information on forwarding events to a syslog server or SIEM, see Forward events to an external Syslog or SIEM server.
The log inspection module lets you:
- Meet PCI DSS log monitoring requirements.
- Detect suspicious behavior.
- Collect events across heterogeneous environments containing different operating systems and diverse applications.
- View events such as error and informational events (disk full, service start, service shutdown, etc.).
- Create and maintain audit trails of administrator activity (administrator login or logout, account lockout, policy change, etc.).
This article covers:
- Enable log inspection
- Work with log inspection events
- Thresholds for Event Storage or Event Forwarding
- Test Log Inspection
Enable log inspection
This is a typical procedure for enabling log inspection:
1. Turn on log inspection
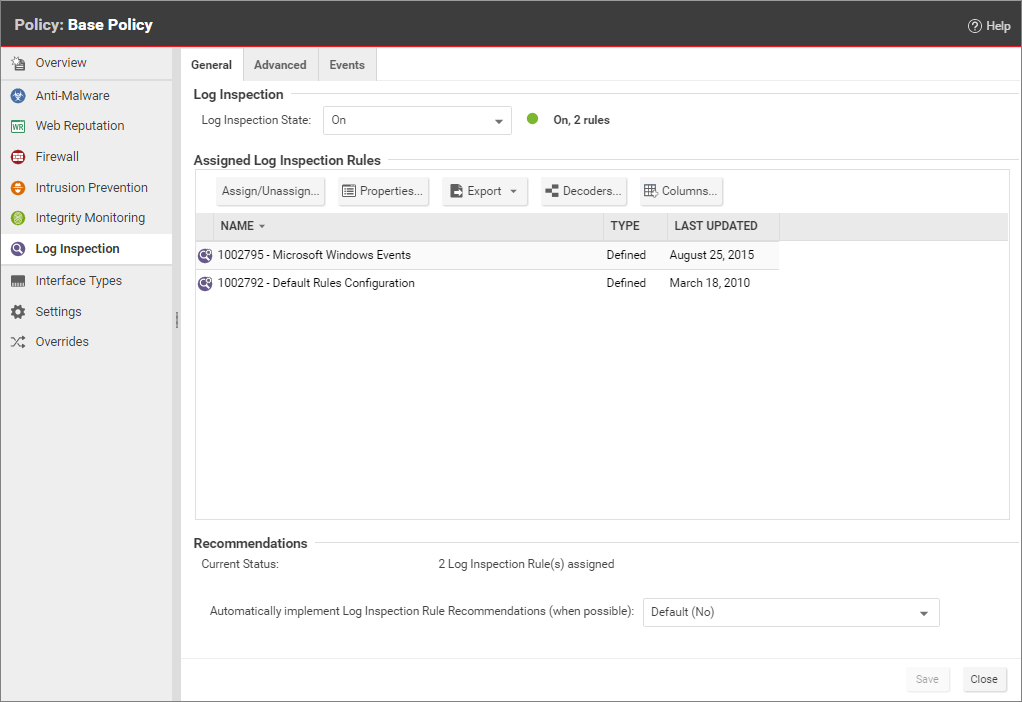
You can enable log inspection in the settings for a computer or in policies. To do this, open the Policy or Computer editor and go to Log Inspection > General. Set the Configuration to "On" or "Inherited (On)" and then click Save.
2. Run a recommendation scan
Run a recommendation scan on the computer to get recommendations about which rules would be appropriate. To do this, open the Computer editor and go to log inspection > General. In the Recommendations section, click Scan for Recommendations. You can optionally specify that Deep Security should implement the rule recommendations that it finds.
For more information about recommendation scans, see Manage and run recommendation scans.
Some log inspection rules written by Trend Micro require local configuration to function properly. If you assign one of these rules to your computers or one of these rules gets assigned automatically, an alert will be raised to notify you that configuration is required.
Rules need to be set to gather security events relevant to your requirements. When improperly set, events for this feature can overwhelm the Deep Security database if too many log entries are triggered and stored.
3. Apply the log inspection rules
As described above, when you run a recommendation scan, you can have Deep Security implement the recommended rules automatically. You can also select and manually assign rules. Deep Security ships with many pre-defined rules covering a wide variety of operating systems and applications.
In the Computer or Policy editor, go to Log Inspection > General. The "Assigned Log Inspection Rules" section displays the rules that are in effect for this policy or computer. To add or remove log inspection rules, click Assign/Unassign. This will display a window showing all available log inspection rules, from which you can select or deselect rules.
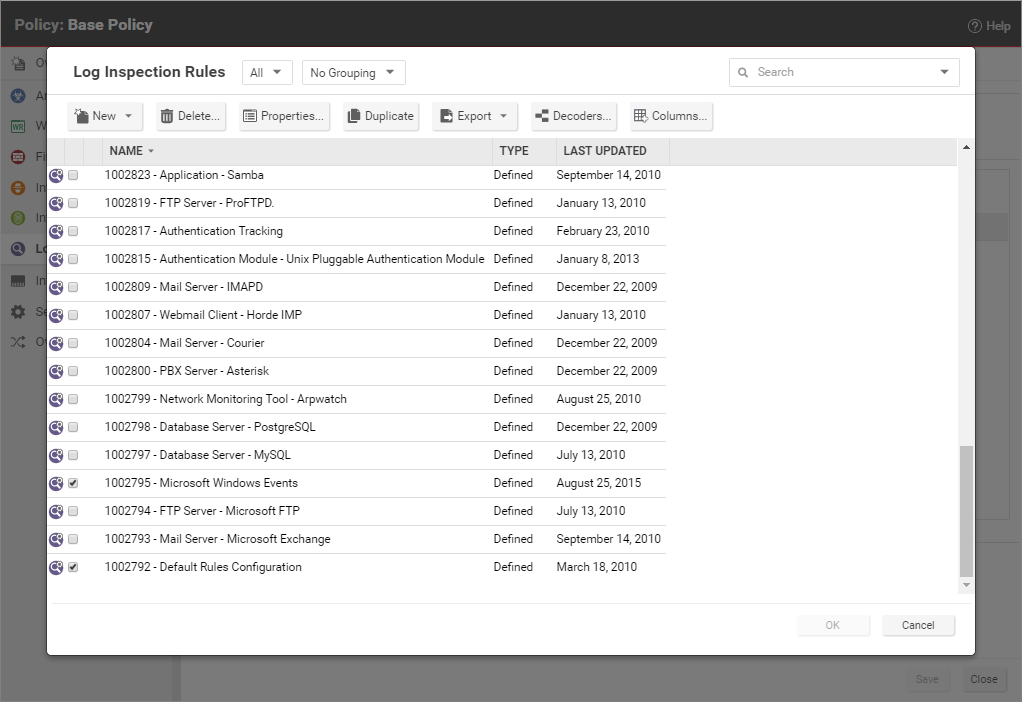
You can edit a log inspection rule locally so that the changes apply only to the computer or policy being edited, or globally so that the changes apply to all other policies or computers that are using the rule. To edit a rule locally, right-click it and click Properties. To edit a rule globally, right-click it and click Properties (Global).
Although Deep Security ships with log inspection rules for many common operating systems and applications, you also have the option to create your own custom rules. To create a custom rule, you can either use the "Basic Rule" template, or you can write your new rule in XML. For information on how to create a custom rule, see Define a Log Inspection rule for use in policies.
Work with log inspection events
The events generated by the log inspection module are displayed in Deep Security Manager, under Events & Reports > Log Inspection Events. Event tagging can help you to sort events and determine which ones are legitimate and which ones need to be investigated further.
You can manually apply tags to events by right-clicking the event and then clicking Add Tag(s). You can choose to apply the tag to only the selected event or to any similar log inspection events. You can also use the auto-tagging feature to group and label multiple events.
For details, see Log inspection events.
Thresholds for Event Storage or Event Forwarding
Severity clipping allows you to send events to a syslog server (if enabled) or to store events based on the severity level of the log inspection rule.
There are two "severity clipping" settings available in the Policy and Computer editors, on the Details window of a computer or policy, under Log Inspection > Advanced:
- Send Agent events to syslog when they equal or exceed the following severity level: This setting determines which events triggered by those rules get sent to the syslog server, if syslog is enabled. (To enable syslog, go to Administration > System Settings > Event Forwarding > SIEM.)
- Store events at the Agent for later retrieval by Deep Security Manager when they equal or exceed the following severity level: This setting determines which log inspection events are kept in the database and displayed in the Log Inspection Events page.
Test Log Inspection
Before continuing with further Log Inspection configuration steps, test that the rules are working correctly:
- Ensure Log Inspection is enabled.
- Go to Computer or Policies editor > Log Inspection > Advanced. Change Store events at the Agent/Appliance for later retrieval by DSM when they equal or exceed the following severity level to Low (3) and click Save.
- Go to the General tab, and click Assign/Unassign. Search for and enable:
- 1002792 - Default Rules Configuration – This is required for all other Log Inspection rules to work.
If you're a Windows user, enable:
- 1002795 - Microsoft Windows Events – This logs events every time the Windows auditing functionality registers an event.
If you're a Linux user, enable:
- 1002831 - Unix - Syslog - This inspects the syslog for events.
- Click OK, and then click Save to apply the rules to the policy.
- Attempt to log in to the server with an account that does not exist.
- Go to Events & Reports > Log Inspection Events to verify the record of the failed login attempt. If the detection is recorded, the Log Inspection module is working correctly.