Deep Security Manager 10 has reached end of support. Use the version selector (above) to see more recent versions of the Help Center.
Define a firewall rule for use in policies
Firewall Rules examine the control information in individual packets. The Rules either block or allow those packets based on rules that are defined on these pages. Firewall Rules are assigned directly to computers or to policies that are in turn assigned to a computer or collection of computers.
Create a new firewall rule
There are three ways to add a new firewall rule on the Policies > Common Objects > Rules > Firewall Rules page:
- To create a new rule, click New > New Firewall Rule.
- To import a rule from and XML file, click New > Import From File.
- To copy and then modify an existing rule, select the rule from the list and then click Duplicate. To edit the new rule, select it and then click Properties.
Configure firewall rule properties
These properties are available when you create a new rule or edit an existing one.
General Information
- Name: The name of the Firewall Rule.
- Description: A detailed description of the Firewall Rule.
- Action: Your Firewall Rule can behave in four different ways. These are described here in order of precedence:
- The traffic can bypass the firewall completely. This is a special rule that can cause the packets to bypass the Firewall and Intrusion Prevention engine entirely. Use this setting for media intensive protocols where filtering may not be desired.
- It can log only. This means it will only make an entry in the logs and not interfere with the traffic.
- It can force allow defined traffic (it will allow traffic defined by this rule without excluding any other traffic.)
- It can deny traffic (it will deny traffic defined by this rule.)
- It can allow traffic (it will exclusively allow traffic defined by this rule.)
For detailed information on how actions and priority work together, see Firewall rule actions and priorities.
If you have no Allow rules in effect on a computer, all traffic is permitted unless it is specifically blocked by a Deny rule. Once you create a single Allow rule, all other traffic is blocked unless it meets the requirements of the Allow rule. There is one exception to this: ICMPv6 traffic is always permitted unless it is specifically blocked by a Deny rule.Only one rule action is applied to any particular packet, and rules (of the same priority) are applied in the order listed above. - Priority: If you have selected "force allow", "deny", or "log only" as your rule action, you can set a priority here of 0 (low) to 4 (highest). Setting a priority allows you to combine the actions of rules to achieve a cascading rule effect. Log only rules can only have a priority of 4, and Allow rules can only have a priority of 0.
The priority determines the order in which rules are applied. High priority rules get applied before low priority rules. For example, a port 80 incoming deny rule with a priority of 3 will drop a packet before a port 80 incoming force allow rule with a priority of 2 ever gets applied to it.
- Packet Direction: The Deep Security firewall is a bidirectional firewall. Therefore, it is able to enforce rules on traffic originating from the network to the Deep Security host, referred to as incoming, and traffic from the host to the network, referred to as outgoing. Select whether this rule will be applied to incoming or outgoing traffic.
-
Firewall rules only apply to a single direction; therefore Firewall Rules for specific types of traffic often come in pairs.
- Frame Type: Select a frame type. Use the Not checkbox to specify whether you will be filtering for this frame type or anything but this frame type. The term "frame" refers to Ethernet frames, and the available protocols specify the data that the frame carries. Internet Protocol (IP), Address Resolution Protocol (ARP), and Reverse Address Resolution Protocol (REVARP) are the most commonly carried protocols on contemporary Ethernet networks but by selecting "Other" from the list you can specify any other frame type by its "frame number".
-
You can exclusively select IPv4 or IPv6. To specify either (both), select IP.Solaris Agents will only examine packets with an IP frame type, and Linux Agents will only examine packets with IP or ARP frame types. Packets with other frame types will be allowed through. Note that the Virtual Appliance does not have these restrictions and can examine all frame types, regardless of the operating system of the virtual machine it is protecting.For a list of frame types, see the Internet Assigned Numbers Authority (IANA) Web site.
If you select the Internet Protocol (IP) frame type, the Protocol field is enabled, where you specify the transport protocol that your rule will look for. Use the checkbox to specify whether you will be filtering for this protocol or anything but this protocol. You can choose from the drop down list of predefined common protocols, or you can select "Other" and enter the protocol code yourself (a three digit decimal value from 0 to 255).
Packet Source and Packet Destination
The firewall can use an IP address, MAC address, or Port to determine traffic source and destination:
IP Address
These options are available for defining IP addresses:
- Any: No address is specified so any host can be either a source or destination
- Single IP: A specific machine is identified using its IP address.
- Masked IP: This applies the rule to all machines that share the same subnet mask
- Range: This applies the rule to all machines that fall within a specific range of IP addresses
- IP(s): Use this when applying a rule to several machines that do not have consecutive IP addresses.
- IP List: Enables you to select a value that you defined on the Policies > Common Objects > Lists > IP Lists page.
MAC Address
The following options are available for defining MAC addresses:
- Any: No MAC address was specified, so the rule applies to all addresses
- Single MAC: Rule applies to a specific MAC address
- MAC(s): Rule applies to the MAC addresses specified here
- MAC List: Enables you to select a value that you defined on the Policies > Common Objects > Lists > MAC Lists page.
Port
The following options are available for defining Port addresses:
- Any: Rule applies to all ports
- Port(s): Rule applies to multiple ports specifiedhere
- Port List: Enables you to select a value that you defined on the Policies > Common Objects > Lists > Port Lists page.
Specific Flags
If you have selected TCP, ICMP, or TCP+UDP as your protocol in the General Information section, you can direct your Firewall Rule to watch for specific flags. If the rule does not apply to all flags, you can choose from these flags:
- URG
- ACK
- PSH
- RST
- SYN
- FIN
There are a number of ways these flags can be used in different attacks. Only a selection will be discussed here.
The URG flag indicates that the packet is urgent and must be processed before all others, while the PSH flag sets the TCP stack to flush its buffers and send all information up to the application. Both flags can be used in a type port scan called the Xmas scan which is typically a FIN packet with the URG and PSH flags enabled. This scan gets its name from the alternating bits turned on and off in the flags byte (00101001), much like the lights of a Christmas tree.
When an unprotected machine receives packets related to a Xmas scan, the following happens:
| Condition | Response |
|---|---|
| Closed Port | Returns an RST packet |
| Open Port | No response, exposing existence of the open port |
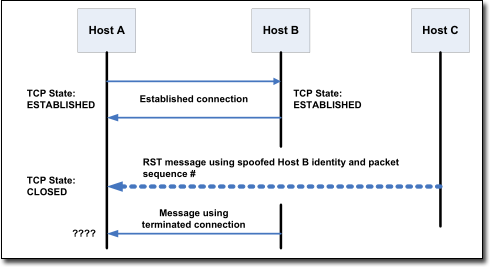
The RST, or RESET, flag abruptly terminates TCP connections. As described above, among its legitimate uses is to terminate connects to closed ports indicating an impossible or disallowed connection. However, the RST flag can also be used as part of a RESET attack, designed to disrupt existing sessions. The following diagram illustrates a situation where an attack, Host C, was able to calculate the TCP sequence number that Host A expected from a packet from Host B, thereby spoofing Host A into believing that Host B had sent it a RST packet. The end result is a denial of service attack:
Events
Select whether to enable or disable logging events because of this rule. If event logging is enabled, you can record the packet data with the event.
Options
Alert
Specify whether this firewall rule should trigger an alert when it is triggered. If you only want this rule to be active during specific periods, assign a schedule from the list.
Schedule
Select whether the firewall rule should only be active during a scheduled time.
 .
.
Context
Rule contexts are a powerful way of implementing different security policies depending on the computer's network environment. You will most often use contexts to create policies that apply different Firewall and Intrusion Prevention rules to computers (usually mobile laptops), depending on whether that computer is in or away from the office.
Contexts are designed to be associated with Firewall and Intrusion Prevention Rules. If the conditions defined in the context associated with a rule are met, the rule is applied.
To determine a computer's location, contexts examine the nature of the computer's connection to its domain controller. For more information on contexts, see Policies > Common Objects > Other > Contexts.
Assigned To
This tab displays a list of policies that include this firewall rule, as well as any computers to which this firewall rule has been assigned directly. Firewall rules can be assigned to policies in the Policies page and to computers in the Computers page.