Upgrade Deep Security Manager VM for Azure Marketplace
To determine which version of Deep Security Manager you have, go to Support > About. The version number of the currently available version is listed on the description page for the Deep Security Manager in Azure Marketplace. Compare these two numbers to determine if you need to upgrade.
Each node must have the same version of Deep Security Manager VM for Azure Marketplace. If you are planning on adding a new node, the version of the new node must match the version used by the existing nodes. This might mean that you have to upgrade the version on the existing nodes to make sure they match the new node.
Will my virtual machines still be protected during the upgrade?
Your virtual machines will still continue to be protected throughout the entire upgrade process. There will be a brief outage for the Deep Security Manager nodes when they are upgraded but all existing Deep Security Agents will continue to function normally during this period. New agents cannot be activated until the Deep Security Manager services have been restored.
Before you begin
Before you upgrade to the latest version of Deep Security Manager VM for Azure Marketplace, ensure that you have the following information about your current version:
- Resource group name
- Database credentials: hostname, name, admin name, and admin password
- License type: You can view this by going to Administration > Licenses in Deep Security Manager.
Upgrade to the latest version
The diagram below provides an overview of the upgrade process. Detailed instructions follow the diagram.
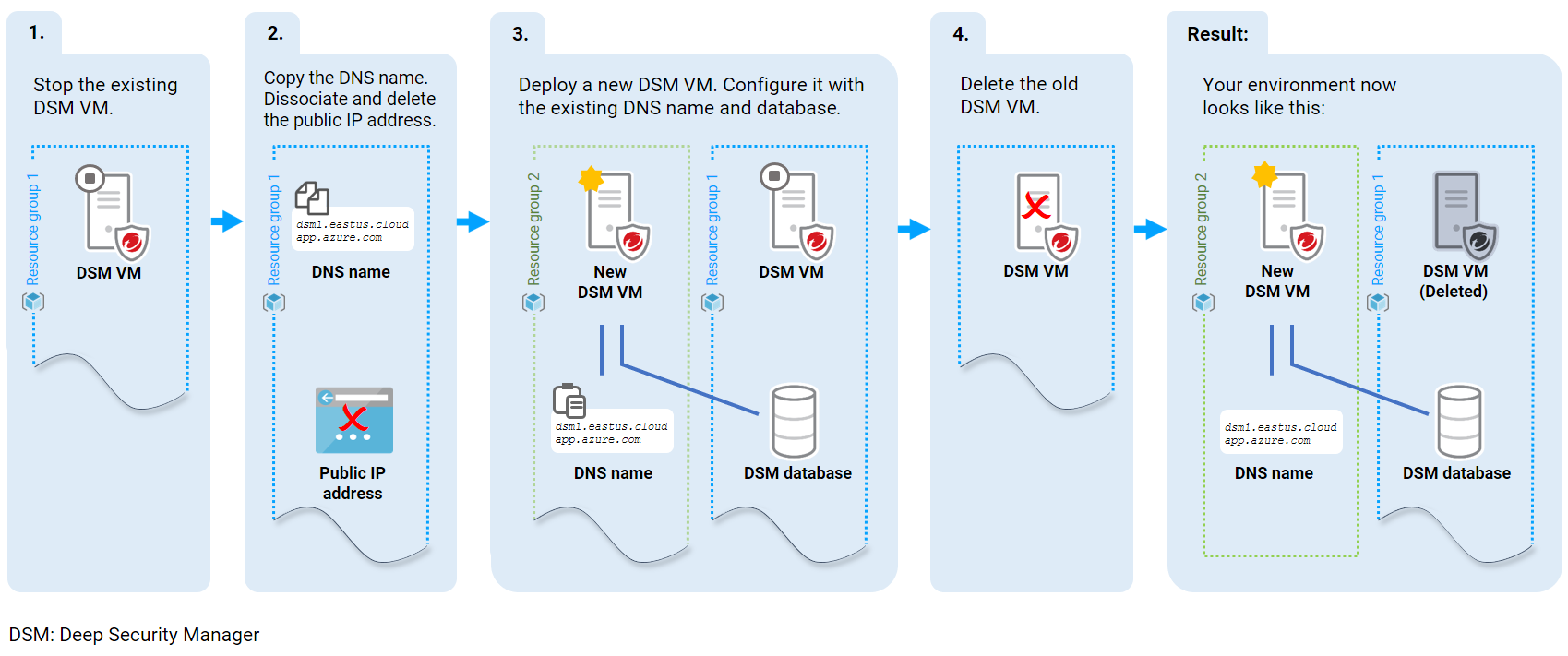
First, stop the existing Deep Security Manager:
Do not delete the existing Deep Security Manager.
- Log in to the Azure portal.
- On the left, click Resource groups.
- In the main pane, click the resource group that contains your existing Deep Security Manager.
- In the main pane, click the Deep Security Manager VM link to show its dashboard page.
- Near the top of the page, click Stop. Wait for the onscreen message indicating a successful stop.
Next, copy the DNS name, dissociate the public IP address, and then delete it:
- On the left, click Resource groups, and then click the resource group that contains your Deep Security Manager.
- In the main pane, look for the Public IP address line, and click the associated link to open the public IP address details.
- Copy the DSN name value to the clipboard or to a file. The value looks similar to: dsm1.eastus.cloudapp.azure.com.
- Click Dissociate and then click Delete to deleted the public IP address.
This step ensure that the DNS name stays the same after the upgrade, and this is recommended to ensure that agents keep functioning properly.
Next, deploy a new Deep Security Manager VM and configure it with the old DNS name:
- Make sure your existing Deep Security Manager is still present and stopped.
- In the search bar at the top of the Azure portal, begin typing Deep Security and select Deep Security Manager (BYOL) from the search results. The Deep Security Manager (BYOL) page appears.
- Click Create.
- Under Deep Security Manager VM name, specify the name of the new VM. The name can be the same or different from your existing Deep Security Manager VM.
- Under Your Username, specify a user name. You will use this user name to log in to the new Deep Security Manager VM.
- Under Authentication type, select Password or SSH public key and then specify a password or SSH public key.
- Under Subscription, select the Azure subscription you want to use with the Deep Security Manager VM. Usage fees accrued under this subscription are billed by Microsoft (not Trend Micro).
- Under Resource Group, select Create new and enter a name to create a new resource group. Alternatively, click Select existing to use an existing empty resource group.
- Under Location, select an Azure region. Make sure you select the same location as your original Deep Security Manager VM.
- Under VM Size, accept the default or click Change size to select another size. If no sizes are selectable, clear the filters.
- Under Public IP address, keep the default or enter another name to set the label of the public IP address resource. This label appears in the Azure portal interface.
- Under Deep Security Manager URL, enter the host name of your original Deep Security Manager. This host name combined with the trailing domain name must match the original Deep Security Manager 'DNS name' that you copied in an earlier step. For example: dsm1.eastus.cloudapp.azure.com.
- Under Deep Security Manager console port and Heartbeat Port, accept the defaults or specify different port numbers. For details on ports, see Port numbers, URLs, and IP addresses.
- Click OK. The Deep Security Database blade appears.
- Under Azure SQL Database, click Use Existing and enter the credentials you recorded in the Before you begin section above. Click OK.
- Wait for a Validation passed message near the top of the screen. Click OK. The Create page appears with the terms of use.
- Leave the check box at the bottom of the agreement deselected unless you want Microsoft to contact you.
- Click Create. On the top-right, click the notifications icon to view the progress of the deployment.
- Verify that the upgrade was successful:
- Open a browser and go to the following address: https://<DNS name> where <DNS name> is replaced with the DNS name of your new Deep Security Manager. For example, https://dsm1.eastus.cloudapp.azure.com. The Deep Security Manager login page appears.
- Log in. The Deep Security Manager dashboard page appears.
- At the top-right, go to Support > About and check the version number. It should be the same as the version number listed on the Deep Security Manager (BYOL) page in Azure.
Finally, delete the old Deep Security Manager VM and its resources:
- In the Azure portal, on the left, click Resource groups.
- In the main pane, click the resource group containing the original Deep Security Manager VM to view its details.
- Delete the original Deep Security resources of Type:
- Virtual machine
- Disk (optional)
- Network interface
- Network security group
- Storage account (optional)
- Virtual network
Post-upgrade tasks
After the upgrade, you may choose to complete the following tasks:
- Replace the server certificate: After the upgrade, the Deep Security Manager's server certificate is preserved, unless you performed a fresh install. If your certificate was created using a weak cryptographic algorithm, such as SHA-1, consider replacing the certificate. Using stronger cryptography ensures compliance with the latest standards and provides better protection against the latest exploits and attacks. See Replace the Deep Security Manager TLS certificate.