Deep Security coverage of Log4j vulnerability
On December 9, 2021, a new critical zero-day vulnerability impacting multiple versions of the popular Apache Log4j 2 logging library was publicly disclosed. If exploited, this vulnerability could result in Remote Code Execution (RCE) by logging a certain string on affected installations. This specific vulnerability has been assigned CVE-2021-44228 and is also being commonly referred to as "Log4Shell" in various blogs and reports.
Deep Security includes the Intrusion Prevention module (IPS), which protects your computers from zero-day vulnerabilities and other attacks. Intrusion Prevention rules provide "virtual patching" by intercepting traffic that's trying to exploit the vulnerability, protecting your computers until vendor's patches that fix the vulnerability are released, tested, and deployed.
The Trend Micro Labs team has provided a new IPS rule to address this vulnerability:
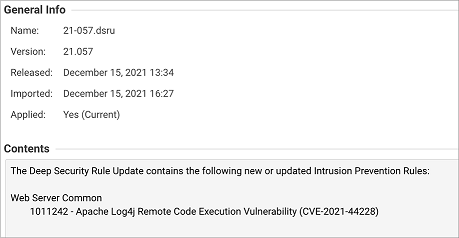
1011242 - Apache Log4j Remote Code Execution Vulnerability (CVE-2021-44228)
Apply virtual patching for the Log4j vulnerability
Follow the steps below to check whether the new rule is protecting your computers.
- In Deep Security Manager, go to Administration > Updates > Security > Rules.
- The new rule is included in 21-057.dsru. Check that the rule update is shown as Applied.
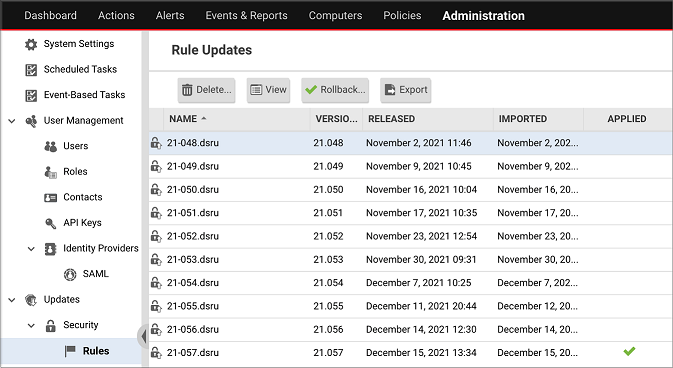
- If the rule isn't applied, run a recommendation scan. We suggest that you create a 'run once' scheduled task and select the Run Task on 'Finish' option.
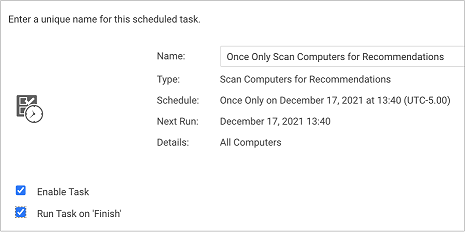
- To ensure that the rule gets applied wherever it's recommended, open the policy that is assigned to the computers you just scanned, go to Intrusion Prevention > General, and search for rule 1011242. Select the checkbox next to the rule name to assign it to the policy. All computers protected by this policy will have the rule applied to it.
- Intrusion Prevention operates in either Detect or Prevent mode. Detect mode generates events about rule violations but doesn't block traffic. Prevent mode generates events and blocks traffic that matches rules, to prevent attacks. To set Prevent mode, open the computer or policy editor, go to Intrusion Prevention > General and set Intrusion Prevention Behavior to Prevent. Click Save.
Identify potentially affected hosts
If you are also using Trend Micro Vision One, you can use the following query to identify hosts that may be affected by this vulnerability:
eventName:DEEP_PACKET_INSPECTION_EVENT AND (ruleId:1008610 OR ruleId:1011242 OR ruleId:1005177) AND ("${" AND ("lower:" OR "upper:" OR "sys:" OR "env:" OR "java:" OR "jndi:"))
Use a custom Log Inspection rule to investigate activity
Trend Micro has provided a Log Inspection rule to help identify activity related to this vulnerability:
1011241 - Apache Log4j Remote Code Execution Vulnerability (CVE-2021-44228)
You can also create a custom Log Inspection rule to detect patterns that are discovered in the future. For details, see Custom Log Inspection Rules for Log4Shell Vulnerability on Trend Cloud One - Endpoint & Workload Security and Deep Security.
More resources from Trend Micro about this vulnerability
- For up-to-date information about how Trend Micro can help, see Apache Log4j (Log4Shell) Vulnerability.
- For a video with information about this vulnerability.
- For details on this vulnerability and how Trend Micro can help protect your environment from attack, see SECURITY ALERT: Apache Log4j "Log4Shell" Remote Code Execution 0-Day Vulnerability (CVE-2021-44228).