Set up Application Control
For information about how Application Control works, see About Application Control.
To enable Application Control and monitor software changes:
- Turn on Application Control
- Monitor new and changed software
- Turn on maintenance mode when making planned changes
This article also provides Application Control tips and considerations that you should be aware of when working with Application Control.
Once you've enabled Application Control, you can also learn how to:
- View and change Application Control rulesets
- Reset Application Control after too much software change
- Monitor Application Control events
- Use the API to create shared and global rulesets
Turn on Application Control
You can enable Application Control in the settings for a computer or in policies:
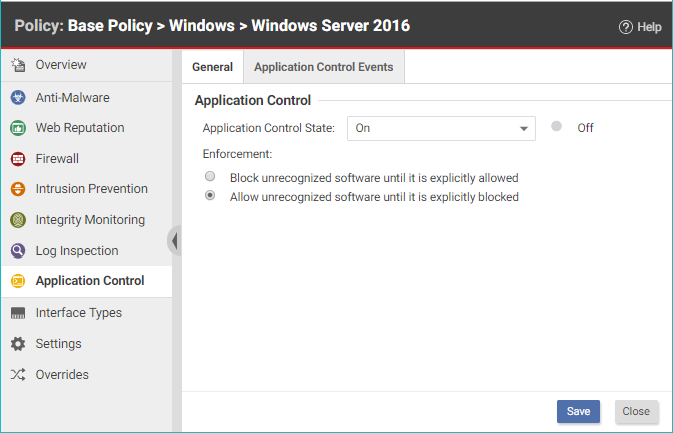
- Open the Computer or Policy editor and go to Application Control > General.
- Set the Application Control State to "On" or "Inherited (On)".
- Under Enforcement, select your targeted protection state:
- Block unrecognized software until it is explicitly allowed
- Allow unrecognized software until it is explicitly blocked (we recommend that you choose this option when initially setting up Application Control)
- Click Save.
The next time that the Deep Security Manager and agent connect, the agent scans and then generates an inventory of all software installed on the computer and creates rules that allow all the software that it finds. This initial inventory can take 15 minutes or longer, depending on your environment.
When generating an inventory, Application Control does not include software on remote file systems such as a CIFS (Common Internet File System) or NFS (Network File System). Software on remote file systems must be manually added to the inventory.
To check that Application Control is working as expected, follow the instructions in Verify that Application Control is enabled.
Monitor new and changed software
Once an inventory has been created on a protected computer, any software executable files that are added or changed are classified as a "software change" and appear on the Actions page in Deep Security Manager. When unrecognized software runs, or attempts to run and is blocked, the event is listed under Events & Reports > Events > Application Control Events > Security Events. For more information, see Application Control events
After you initially enable Application Control, you will likely see a lot of software changes on the Actions page. This can happen when allowed software creates new executables, renames files, or relocates files through the normal course of operation. As you add rules to tune Application Control, you should see fewer software changes.
To quickly find all software changes on all computers and easily create allow or block rules for them, use the Actions tab.
You can automate the creation of allow or block rules using the Deep Security API. For more information, see the Allow or block unrecognized software guide in the Deep Security Automation Center.
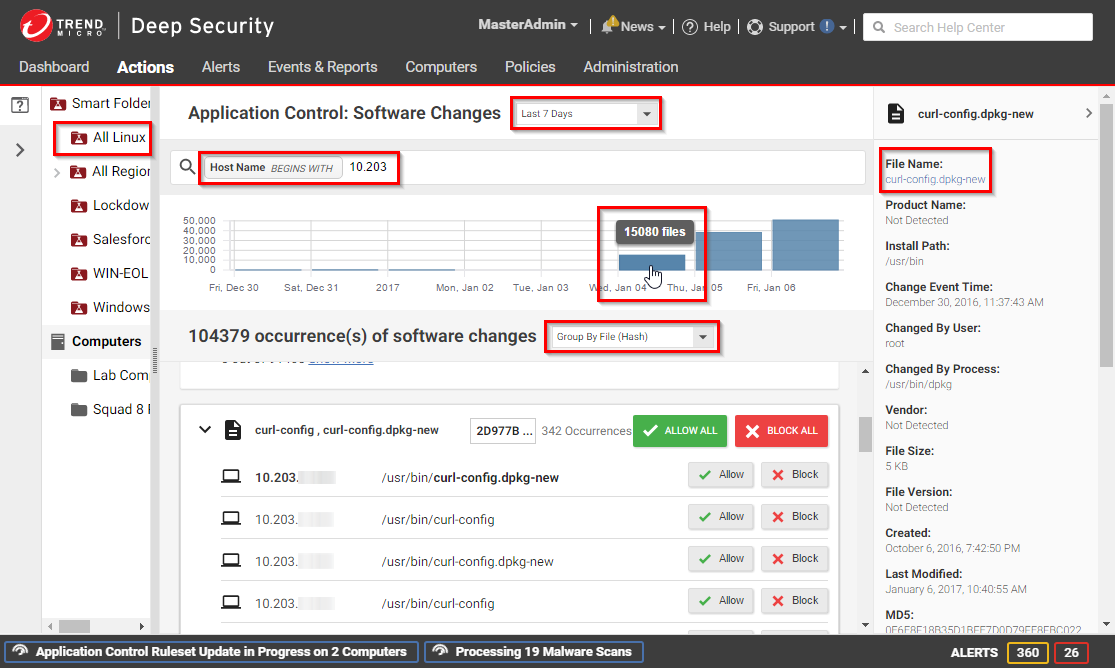
- In Deep Security Manager, go to Actions.
- There are several ways you can filter to see only specific occurrences of unrecognized software.
Instead of evaluating each software change on each computer individually, use the filters described below to find software changes that you know are good, and allow them in bulk.
To reduce the number of software changes being displayed:
- From the drop-down list next to Application Control: Software Changes, select a time range such as Last 7 Days. You can also click a bar in the graph near the top of the page to display the changes for that time period.
- In the pane on the left, click Computers and select an individual computer or group, or click Smart Folders to display only the computers that are included in a particular smart folder (see Group computers dynamically with smart folders).Unlike the Computers tab, the Software Changes pane usually does not show all computers. It only displays computers where Application Control has detected software changes that don't already have allow or block rules.
- Enter search terms and operators in the search filter field. You search for these attributes: Change By Process, Change By User, File Name, Host Name, Install Path, MD5, SHA1, and SHA256. For example, you could find all changes made by a particular user that you trust and click Allow All to allow all of their changes. Or if a particular software update was installed across your organization (while maintenance mode was not enabled), filter the page according to the hash value of the file and click Allow All to allow all occurrences.
Details about a software change are displayed in the right pane. You can click the file name or computer name in the details to add it to your search filter.
- Select whether to Group by File (Hash) or Group by Computer.
- Click either Allow or Block to add an allow or block rule on that computer, for that software. If you need more information to decide whether to allow or block, click the software name, then use the details panel on the right side.
The next time that the agent connects with the Deep Security Manager, it receives the new rules.
Tips for handling changes
- For most environments, we suggest that you select the Allow unrecognized software until it is explicitly blocked option to allow software changes by default when you first enable Application Control and add allow and block rules for changes that you see on the Actions page. Eventually, the rate of software changes should decrease. At that point, you could consider blocking software changes by default and creating allow rules for the software that you know is good. Some organizations prefer to continue to allow changes by default and monitor the Actions page for software that should be blocked.
- You may prefer to start by evaluating security events, rather than dealing with unrecognized software first. Security events show you which unrecognized software has run (or attempted to run). For information on security events, see Monitor Application Control events.
- When an unrecognized file is allowed to execute and you want to continue to allow it, create an Allow rule. In addition to allowing the file's execution, the event is no longer logged for that file, which reduces noise and makes important events easier to find.
- When a known file's execution is blocked, consider cleaning that file from the computer, especially for repeated occurrences.
- Keep in mind that software changes are listed for each computer where they occur. You must allow or block the software for each computer.
- Rules are assigned to computers, not to policies. For example, if
helloworld.pyis detected on three computers, when you click Allow All or Block All, this would affect only three computers. It won't affect future detections on other computers, because they have their own rulesets. - If you see changes related to software updates that you can control, use the maintenance mode feature when performing those updates. See Turn on maintenance mode when making planned changes.
Turn on maintenance mode when making planned changes
With maintenance mode enabled, Application Control does not scan remote file systems such as a CIFS (Common Internet File System) or NFS (Network File System). Since software changes on remote file systems cannot be auto-authorized, we recommended that you manually add them to the software inventory as required.
When you install patches, upgrade software, or deploy web applications, Application Control will detect them. Depending on your setting for how to handle unrecognized software, this could block that software until you use the Actions tab to create allow rules.
To avoid extra down time and alerts during deployment and maintenance windows, you can put Application Control into a mode designed for maintenance windows. While maintenance mode is enabled, Application Control will continue to enforce rules that block software, but it will allow new or updated software to run and automatically add it to the computer's inventory.
You can automate maintenance mode using the Deep Security API. For more information, see the Configure maintenance mode during upgrades guide in the Deep Security Automation Center.
- In Deep Security Manager, go to Computers.
- Select one or more computers, then click Actions > Turn On Maintenance Mode.
- Select the duration of your maintenance window.
Maintenance mode will automatically disable itself when your maintenance window is scheduled to end. Alternatively, if you'd prefer to manually disable maintenance mode when updates are finished, select Indefinite.
On the Dashboard, the Application Control Maintenance Mode Status widget indicates whether the command succeeded.
- Install or upgrade software.
- If you chose to disable maintenance mode manually, remember to disable maintenance mode in order to start to detect software changes again.
Application Control tips and considerations
- For better performance with Application Control, use Deep Security anti-malware instead of Windows Defender. See Coexistence of Deep Security Agent with Microsoft Defender Antivirus.
- If you create a block rule for a batch file or PowerShell script, you will not be able to copy, move, or rename the file when using its associated interpreter (powershell.exe for PowerShell scripts or cmd.exe for batch files).
- If you add an allow or block rule, it is normally sent to the agent the next time the agent connects to Deep Security Manager. If you see an error saying that the ruleset upload was not successful, verify that network devices between the agent and the manager or relay allow communications on the heartbeat port number or relay port numbers.
- To verify that a block rule is working, try to run the software that you just blocked. (For details on how Deep Security Agent detects changes, see What does application control detect as a software change?)
- When blocked software remains installed, Application Control continues to record logs and show alerts when it blocks the software from running. To reduce the permission error logs on the computer and also reduce your attack surface, uninstall the software that Application Control is blocking. Once that is done, if you want to dismiss related alerts, either go to Alerts or go to Dashboard, click the alert, and then click Dismiss Alert. Not all alerts can be dismissed. For more information, see Predefined alerts.
- For performance reasons, if the computer has too much software change, Application Control will continue to enforce existing rules, but stop detecting and displaying software changes. To resolve this, see Reset Application Control after too much software change.