Customize the dashboard
The dashboard is the first page that appears after you log in to Deep Security Manager.
Each user can customize the contents and layout of their dashboard. Deep Security Manager automatically saves your settings, and will remember your dashboard the next time that you log in. You can also configure the data's time period, and which computer's or computer group's data is displayed.
Specify date and time range
The dashboard can display data from either the last 24 hours or the last seven days, as per the following illustration:
Specify computers and computer groups
You can use the Computer option to filter the displayed data to only data from specific computers. For example, only computers using the Linux Server security policy, as per the following illustration:
Filter by tags
In Deep Security, a tag is a unit of metadata that you can apply to an event in order to create an additional attribute for the event that is not originally contained within the event itself. Tags can be used to filter events to simplify the task of event monitoring and management. A typical use of tagging is to distinguish between events that require action and those that have been investigated and found to be benign.
Data displayed in the Dashboard can be filtered by tags, as per the following illustration:
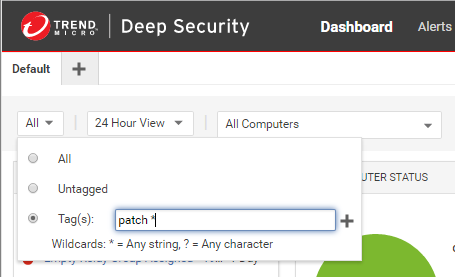
For more information, see Apply tags to identify and group events.
Select dashboard widgets
Click Add/Remove Widgets to display the widget selection window and choose which widgets to display, as per the following illustration:
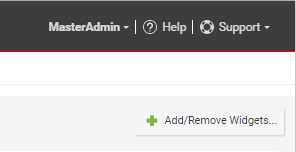
If widgets take up extra space on the dashboard (more than 1x1), their dimensions are listed next to their names.
The following widgets are available:
Monitoring:
- Activity Overview: Overview of activity, including the number of protected hours and size of database.
- Alert History [2x1]: Recent alert history, including the severity of alerts.
- Alert Status: Summary of alerts, including their age and severity.
- Computer Status: Summary of computers, including whether they are managed or unmanaged, and if there are any warnings or critical alerts.
- Manager Node Status [3x1]: The name, CPU usage, memory, jobs, and system events on the manager node.
- Security Update Status: The update status of computers, including the number of computers that are up-to-date, out-of-date, and unknown.
- Tenant Database Usage: The top five tenants ranked by their database size.
- Tenant Job Activity: The top five tenants ranked by their total number of jobs.
- Tenant Protection Activity: The top five tenants ranked by the hours they've been protected.
- Tenant Security Event Activity: The top five tenants ranked by their total number of security events.
- Tenant Sign-In Activity: The top five tenants ranked by their sign-in activity.
- Tenant System Event Activity: The top five tenants ranked by their total number of system events.
- Tenants: Tenant information, including the number of tenants and the amount of hours they have been protected.
Note that the out-of-date category does not include computers with the status Anti-malware Configuration Off, Anti-malware Engineer Offline, and Agent Offline. These statuses have been separated from the general out-of-date classification and categorized individually as Out of Date (Anti-Malware Configuration Off), Out of Date (Anti-Malware Offline), and Out of Date (Agent Offline). Computers with these statuses are not counted in the total displayed on the Security Update Status widget under Out-of-Date.
System:
- My Sign-in History: The last 50 sign-in attempts and whether or not they were successful.
- My User Summary [2x1]: A summary of the user, including name, role, and sign-in information.
- Software Updates: Out-of-date computers.
- System Event History [2x1]: Recent system event history, including the number of events that are categorized as info, warning, or error.
Ransomware:
- Ransomware Event History [3x1]: Recent ransomware event history, including the event type.
- Ransomware Status: The status of ransomware, including the number of ransomware events that occurred in the last 24 hours, the last 7 days, or the last 13 weeks.
Anti-Malware:
- Anti-Malware Event History [2x1]: Recent anti-malware event history, including the action taken for the events.
- Anti-Malware Protection Status: A summary of Anti-Malware Protection status on computers, including whether they are protected, unprotected, or not capable of being protected.
- Anti-Malware Status (Computers) [2x1]: The top five infected computers, including the amount of uncleanable files and the total number of files affected.
- Anti-Malware Status (Malware) [2x1]: The top five detected malware, including their name, amount of uncleanable files, and number of times it was triggered.
- Malware scan Status [2x1]: The top five appliances with incomplete scheduled malware scans.
Web Reputation:
- Web Reputation Computer Activity: The top five computers with Web Reputation events, including the number of events.
- Web Reputation Event History [2x1]: Recent Web Reputation event history, including the events severity.
- Web Reputation URL Activity: The top five URLs that triggered Web Reputation events, including the number of times they were accessed.
Firewall:
- Firewall Activity (Detected): The top five reasons packets were detected, including the number of times.
- Firewall Activity (Prevented): The top five reasons packets were prevented, including the number of times.
- Firewall Computer Activity (Detected): The top five computers that generated detected Firewall events and the number of times they occurred.
- Firewall Computer Activity (Prevented): The top five computers that generated prevented Firewall events and the number of times they occurred.
- Firewall Event History [2x1]: Recent Firewall event history, including if the events were detected or prevented.
- Firewall IP Activity (Detected): The top five source IPs that generated detected Firewall events and the number of times they occurred.
- Firewall IP Activity (Prevented): The top five source IPs that generated prevented Firewall events and the number of times they occurred.
- Firewall Port Activity (Detected): The top five destination ports for detected Firewall events and the number of times they occurred.
- Firewall Port Activity (Prevented): The top five computers that generated prevented Firewall events and the number of times they occurred.
- Reconnaissance Scan Activity: The top five detected reconnaissance scans, including the number of times they occurred.
- Reconnaissance Scan Computers: The top five computers where reconnaissance scans occurred and the number of times they occurred.
- Reconnaissance Scan History [2x1]: Recent reconnaissance scan history, including the type of scan that occurred.
Intrusion Prevention:
- Application Type Activity (Detected): The top five detected application types, including the number of times they were triggered.
- Application Type Activity (Prevented): The top five prevented application types, including the number of times they were triggered.
- Application Type Treemap (Detected) [2x2]: A map of detected application types. Hover over the boxes to display the severity of the events, the number of times it was triggered, and the percentage for each severity level.
- Application Type Treemap (Prevented) [2x2]: A map of prevented application types. Hover over the boxes to display the severity of the events, the number of times it was triggered, and the percentage for each severity level.
- IPS Activity (Detected): The top five reasons Intrusion Prevention events were detected, including the number of times it was triggered.
- IPS Activity (Prevented): The top five reasons Intrusion Prevention events were prevented, including the number of times it was triggered.
- IPS Computer Activity (Detected): The top five computers with detected Intrusion Prevention events.
- IPS Computer Activity (Prevented): The top five computers with prevented Intrusion Prevention events.
- IPS Event History [2x1]: Recent Intrusion Prevention event history, including if the events were detected or prevented.
- IPS IP Activity (Detected): The top five source IPs that generated detected Intrusion Prevention events.
- IPS IP Activity (Prevented): The top five source IPs that generated prevented Intrusion Prevention events.
- Latest IPS Activity (Detected): The top five reasons Intrusion Prevention events were detected since the latest update.
- Latest IPS Activity (Prevented): The top five reasons Intrusion Prevention events were prevented since the latest update.
Integrity Monitoring:
- Integrity Monitoring Activity: The top five reasons Integrity Monitoring events occurred, including the number of times. In this case, the reason refers to the rule that was triggered.
- Integrity Monitoring Computer Activity: The top five computers where Integrity Monitoring events occurred, including the number of events.
- Integrity Monitoring Event History [2x1]: Recent Integrity Monitoring event history, including the severity of events.
- Integrity Monitoring Key Activity: The top five keys for Integrity Monitoring events. The source of the key varies by Entity Set - for files and directories, it is their path, whereas for ports, it is their unique protocol, IP, port number, or tuple.
Log Inspection:
- Log Inspection Activity: The top five reasons Integrity Monitoring events occurred, including the number. In this case, the reason refers to the rule that was triggered.
- Log Inspection Computer Activity: The top five computers where Log Inspection events occurred, including the number of events.
- Log Inspection Description Activity: The top five descriptions for Log Inspection events, including the number of times they occurred. The description refers to the event that was triggered.
- Log Inspection Event History [2x1]: Recent Log Inspection event history, including the severity of events.
Application Control:
- Application Control Maintenance Mode Status [2x1]: The computers in maintenance mode, including their start and end time.
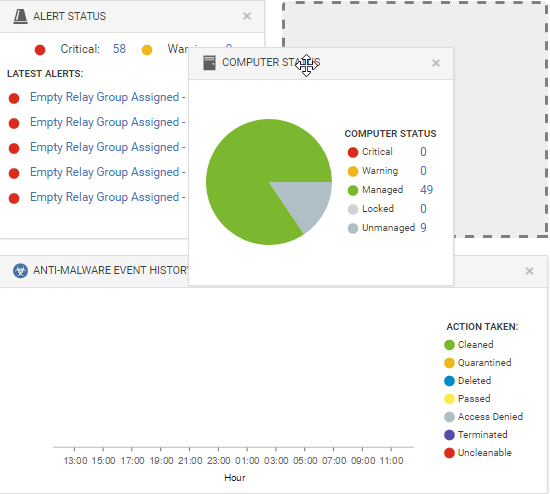
Change the layout
You can move the selected widgets around the dashboard by dragging them by their title bar. That is, if you move a widget over an existing one, they will exchange places. The widget that is about to be displaced will temporarily gray out.
Save and manage dashboard layouts
You can create multiple dashboard layouts and save them as separate tabs. Your Dashboard settings and layouts are not visible to other users after you sign out. To create a new Dashboard tab, click the plus symbol to the right of the last tab on the Dashboard, as per the following illustration: