Integrate with Cisco Identity Services Engine (ISE)
Cisco Identity Services Engine (ISE) in Deep Security performs network containment by assigning an Adaptive Network Control (ANC) policy to target MAC addresses as soon as a threat is detected on a specific host.
This feature enables the Deep Security Manager to continuously monitor threat detection events, such as those from the Anti-Malware and Intrusion Prevention System protection modules. When detection events meet certain configurable criteria, the manager instructs Cisco ISE to quickly apply the ANC policy to all MAC addresses associated with the host from which the detection events originated. The ANC policy allows Cisco ISE to implement security measures, such as moving the targeted MAC addresses to a quarantine VLAN or shutting down the network device port to which the MAC is connected.
Integration flow is shown in the diagram below.
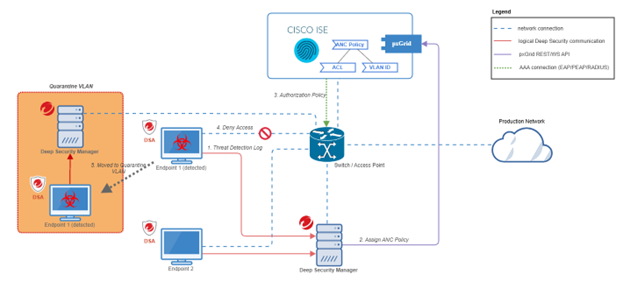
The integration flow functions as follows:
- Deep Security Agent sends detection logs to Deep Security Manager.
- If the detection log meets the configured criteria, such as CVSS score or ransomware malware type, the manager instructs Cisco ISE to apply the Adaptive Network Control (ANC) policy to all MAC addresses associated with the affected endpoint.
- Cisco ISE applies the network Access Control Lists (ACL) associated with the ANC policy on the underlying network switches that have been configured to use Cisco ISE as the authentication server.
- The endpoint's network session is reauthenticated by network switch, resulting in denied access.
- The endpoint may be moved to a quarantine VLAN, where threat diagnosis and remediation are managed by the manager node residing within that VLAN.
This article provides guidelines for configuring the Cisco Identity Services Engine (ISE) connection and utilizing its integration with Deep Security. For more information on Cisco ISE, Adaptive Network Control (ANC) policy, and Access Control Lists (ACLs), please refer to the official Cisco ISE documentation.
Prerequisite Cisco ISE connection configuration
Deep Security Manager connects to Cisco ISE through the Cisco Platform Exchange Grid (pxGrid). pxGrid allows clients to exchange information and communicate via REST API and Websocket. pxGrid ensures secure communication, with only trusted clients gaining access to shared data through controlled pxGrid connections.
Before connecting with Deep Security Manager, the following configurations must be made in the Cisco ISE web console:
- Go to Administration > pxGrid Services > Client Management > Certificates, and click Create to generate the pxGrid client certificate, private key, and root certificate in PEM format.
Your browser will download a ZIP bundle containing the root certificate (files with RootCA in their names), client certificate (files that contain the Common Name specified during pxGrid client certificate creation), and private key.The ZIP file contains multiple certificates, which use the following naming conventions:
- Files that include RootCA in their names typically represent the Cisco ISE root certificate for self-signed certificates.
- Files that contain the Common Name specified during the creation of the pxGrid client certificate generally correspond to the client certificate and the associated client private key.
The image below shows an example of the files contained within a ZIP bundle.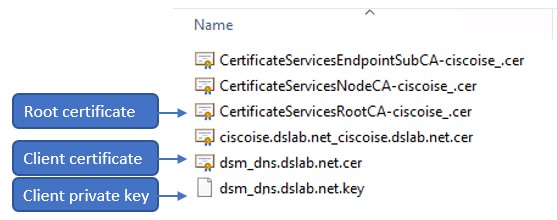
If Cisco ISE was deployed using a certificate signed by a public Certificate Authority, the root certificate will need to be extracted from the ZIP bundle and submitted when you Configure the Cisco ISE connection in Deep Security Manager.
- Go to Operations > Adaptive Network Control > Policy List and create or provide an Adaptive Network Control (ANC) policy for use with Deep Security Manager. Make note of the ANC policy name, since you will need it in order to configure the pxGrid connection for Deep Security Manager.
- Shut down all Deep Security Manager nodes to prevent dangling cache data across manager nodes.
- Enable fast-path event retrieval via IoT/MQTT to speed up event retrieval to near real-time using the following command:
dsm_c -action iotevent -configuration enable -ciscortcRunning this command for one manager will apply the change to all of your manager nodes. This is required in order to provide the near real-time event transmission needed to integrate Cisco ISE with Deep Security Manager.
- Manually start all manager nodes.
Configure the Cisco ISE connection in Deep Security Manager
To connect Cisco ISE to Deep Security Manager:
- Go to Administration > System Settings > Cisco Threat Containment.
- Select Enable Cisco Threat Containment and then click Configure pxGrid Connection.
The Cisco ISE threat containment window appears.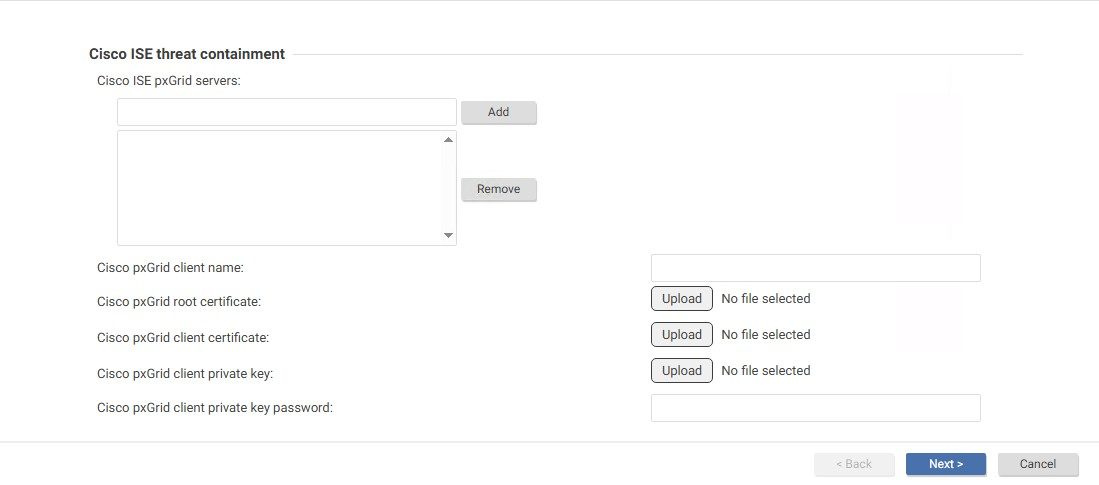
- Add the information and upload the files required for the Cisco pxGrid client. For details, see the following table.
- Once all fields have been completed, click Next. Deep Security Manager attempts to connect to pxGrid using the information provided.
- If the connection is successful, the manager submits a client registration request to the pxGrid server which will require approval from the Cisco ISE administrator.
- If the connection is unsuccessful, you are redirected to the information input page. Return to step 3 above and check that the information entered and files uploaded are correct and complete.
- To approve a successful client registration request, the Cisco ISE administrator should navigate to Cisco ISE Administration > pxGrid Services > Client Management > Clients > pxGrid Clients. From there, the administrator can select the appropriate name and click Approve.
- Once the administrator approves your registration request, return to the Deep Security Manager Cisco Threat Containment tab and click Refresh Connection Status. The connection status label changes to Enabled, and the ANC Policy Name and Network Containment Criteria fields are enabled.
- Select the ANC Policy Name, select the appropriate Alert Criteria checkboxes, and then click Save. The configuration is now complete and Deep Security Manager will actively listen to security events that match the specified alert criteria, and will apply the ANC policy to the MAC addresses of the original hosts involved in the events.
| Field Name | Description |
| Cisco ISE pxGrid servers | Enter the pxGrid server addresses in the format https://<fqdn>:<port>. For example, within the URL you may input multiple server addresses; the API invocation will cycle through these addresses using a round-robin mechanism. |
| Cisco pxGrid client name | This is the name used to register the pxGrid client. Once the client registration request has been submitted, this name will appear in the pxGrid client list within the Organization ISE. |
| Cisco pxGrid root certificate | This is the root certificate of the Public Key Infrastructure (PKI) signing path for the pxGrid server certificate. Please refer to the Prerequisite Cisco ISE connection configuration above for instructions on how to obtain this file. |
| Cisco pxGrid client certificate | The pxGrid client certificate. Please refer to the Prerequisite Cisco ISE connection configuration above for instructions on how to obtain this file. |
| Cisco pxGrid client private key | Private key of pxGrid client certificate. Please refer to the Prerequisite Cisco ISE connection configuration above for instructions on how to obtain this file. |
| Cisco pxGrid client private key password | This is the passphrase used during the generation of the pxGrid client certificate. |
Cisco ISE connection status list
| Status | Description |
| Cisco pxGrid connection information has not been configured. | Cisco pxGrid connection information has not been configured in DSM. |
| Cisco pxGrid client registration has been submitted. | Cisco pxGrid connection information has been configured, and DSM has already sent client account registration request. DSM is waiting for ISE administrator to approve the client request. |
| Cisco pxGrid connected and client status is Enabled. | Cisco pxGrid connection information has been configured and client account approved (enabled). DSM connection to pxGrid is working. However, users should now provide ANC policy name. |
| Cisco pxGrid has been connected and ANC policy has been configured. | DSM connection to pxGrid is working and ANC policy name has been configured in DSM. Furthermore, DSM has already validated that the ANC policy exists in Cisco ISE. Note: This is the fully functional connection status. |
| Cisco pxGrid client status is Disabled. | The pxGrid client account is disabled in Cisco ISE. ISE administrator should enable pxGrid client account. |
| Cannot connect to Cisco ISE pxGrid server. | DSM unable to connect to Cisco pxGrid server. Please see DSM log for details of the error. Some possible causes:
|
Monitor and troubleshoot
A system event is generated whenever a computer or host has an ANC policy assigned or failed be assigned, and whenever a Cisco pxGrid connection fails or a Cisco pxGrid client certificate expires:
- Event ID: 9210
- Event Name: Cisco ANC policy has been assigned
- Event ID: 9211
- Event Name: Cisco ANC policy assignment failure
- Event ID: 9212
- Event Name: Cisco pxGrid connection failure
- Event ID: 9213
- Event Name: Cisco pxGrid client certificate expired
The description of a system event will include the name of the ANC policy and the MAC addresses associated with the successful assignment.
For more details, see System events.
You can check if a MAC address exists in the ANC assignment list by navigating to Cisco ISE Operations > Adaptive Network Control > Endpoint Assignment.
Deep Security Manager will not reassign an ANC policy if the MAC address it uses is already assigned in Cisco ISE. In such cases where a malware or ransomware event is generated by the host but the MAC address has not been assigned an ANC policy, instead of generating an event, the manager will log the following message:
Jun 04, 2025 2:29:42.268000000 PM [+0800] com.trendmicro.manager.core.cisco.RapidThreatContainmentHandler assignAncPolicy
INFO: ThID:258|TID:0|TNAME:Primary|UID:-1|UNAME:|Skipping assign ANC policy ANC_QUARANTINE to MAC 00:50:56:75:**:** as it has been already assigned in Cisco ISE.
Jun 04, 2025 2:29:42.271000000 PM [+0800] com.trendmicro.manager.core.cisco.RapidThreatContainmentHandler assignAncPolicy
INFO: ThID:258|TID:0|TNAME:Primary|UID:-1|UNAME:|Skipping assign ANC policy ANC_QUARANTINE to HostID 1 as all MACs already assigned in Cisco ISE