Deep Security Manager 10 has reached end of support. Use the version selector (above) to see more recent versions of the Help Center.
Create and manage users
Deep Security has users, roles, and contacts which can be created and managed under Administration > User Management.
- Users are Deep Security account holders who can sign in to the Deep Security Manager with a unique user name and password.
- Roles are a collection of permissions to view data and perform operations within Deep Security Manager. Each user is assigned a role.
- Contacts do not have a user account and cannot sign in to Deep Security Manager but they can be designated as the recipients of email notifications and scheduled Reports.
Although contacts cannot sign in to Deep Security Manager, they are assigned roles that define the scope of the information that is sent to them.
For example, three contacts may each be listed as the recipients of a weekly summary report but the contents of the three reports could be entirely different for each contact depending on their computer rights.
In this topic:
- Create new users
- Role-based access to computers and policies
- Role-based editing privileges
- User rights
- Default settings for full access, auditor, and new roles
Create new users
- In the Deep Security Manager go to Administration > User Management > Users.
Role-based access to computers and policies
Access rights and editing privileges are attached to Roles and not to users. To change the access rights and editing privileges of an individual user, the user must be assigned a different role, or the role itself must be edited.
The access that roles have to computers and policies can be restricted to subsets of computers and policies. This can be controlled at a fairly granular level. For example, users can be permitted to view all existing computers, but only permitted to modify those in a particular group. To edit a role, go to Administration > User Management > Roles and double-click a Role (or click New) to display the Roles Properties window.
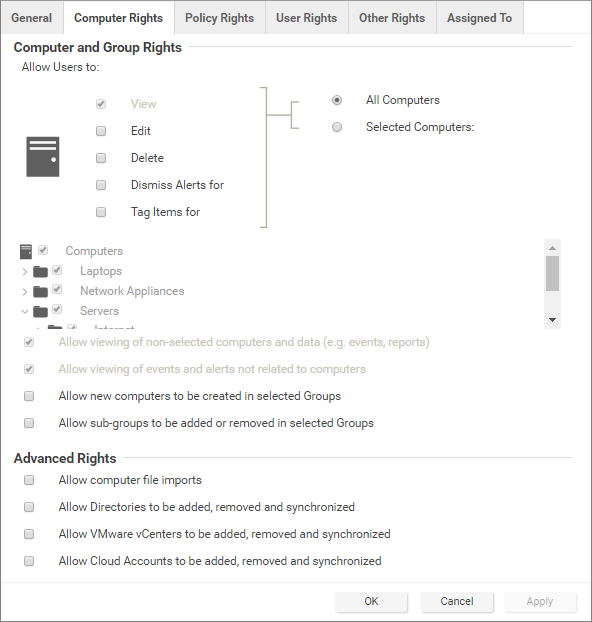
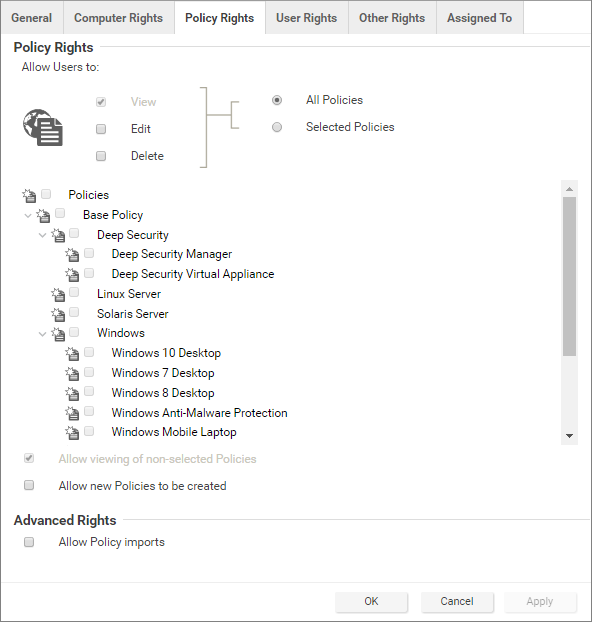
Role-based editing privileges
Within those access restrictions, Roles can have limitations placed on their editing privileges.
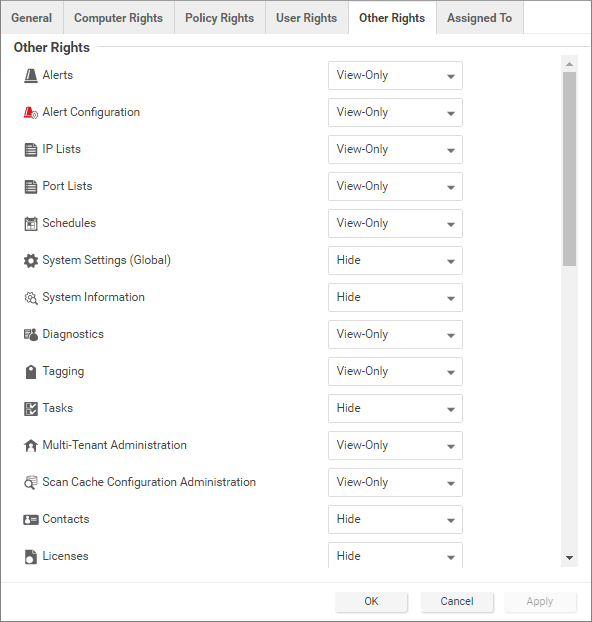
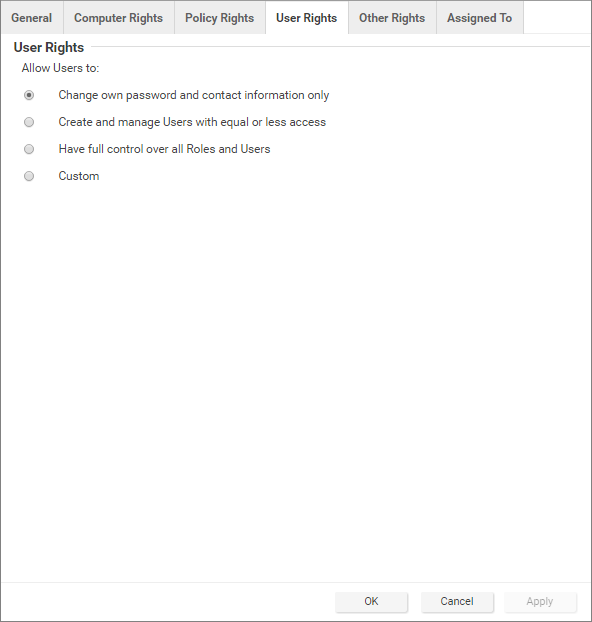
User rights
The User rights area on the User Rights tab of the Role Properties window has the following options:
- Change own password and contact information only
- Create and manage users with equal or less access
- Have full control over all roles and users
- Custom
A role can give users delegated rights over other users. That is, the users with that role can create and modify the properties of users only with equal or less access than themselves.
Default settings for full access, auditor, and new roles
The following table identifies the default rights settings for the full access role and the auditor role. Also listed are the rights settings that are in place when creating a new role by clicking New in the toolbar on the Roles page.
| RIGHTS | SETTINGS BY ROLE | ||
| General | Full Access Role | Auditor Role | New Role Defaults |
| Access to DSM User Interface | Allowed | Allowed | Allowed |
| Access to Web Service API | Allowed | Allowed | Not allowed |
| Computer Rights | Full Access Role | Auditor Role | New Role Defaults |
| View | Allowed, All Computers | Allowed, All Computers | Allowed, All Computers |
| Edit | Allowed, All Computers | Not allowed, All Computers | Not allowed, All Computers |
| Delete | Allowed, All Computers | Not allowed, All Computers | Not allowed, All Computers |
| Dismiss Alerts for | Allowed, All Computers | Not allowed, All Computers | Not allowed, All Computers |
| Tag Items for | Allowed, All Computers | Not allowed, All Computers | Not allowed, All Computers |
| Allow viewing of non-selected computers and data (e.g. events, reports) | Allowed | Allowed | Allowed, All Computers |
| Allow viewing of events and alerts not related to computers | Allowed | Allowed | Allowed, All Computers |
| Allow new computers to be created in selected Groups | Allowed | Not allowed | Not allowed |
| Allow sub-groups to be added or removed in selected Groups | Allowed | Not allowed | Not allowed |
| Allow computer file imports | Allowed | Not allowed | Not allowed |
| Allow Cloud Accounts to be added, removed and synchronized | Allowed | Not allowed | Not allowed |
| Policy Rights | Full Access Role | Auditor Role | New Role Defaults |
| View | Allowed, All Policies | Allowed, All Policies | Allowed, All Policies |
| Edit | Allowed, All Policies | Not allowed, All Policies | Not allowed, All Policies |
| Delete | Allowed, All Policies | Not allowed, All Policies | Not allowed, All Policies |
| View non-selected Policies | Allowed | Allowed | Allowed |
| Create new Policies | Allowed | Not allowed | Not allowed |
| Import Policies | Allowed | Not allowed | Not allowed |
| User Rights (See note on User rights below) | Full Access Role | Auditor Role | New Role Defaults |
| View Users | Allowed | Allowed | Not allowed |
| Create Users | Allowed | Not allowed | Not allowed |
| Edit User Properties | Allowed | Not allowed | Not allowed |
| Delete Users | Allowed | Not allowed | Not allowed |
| View Roles | Allowed | Allowed | Not allowed |
| Create Roles | Allowed | Not allowed | Not allowed |
| Edit Role Properties | Allowed | Not allowed | Not allowed |
| Delete Roles | Allowed | Not allowed | Not allowed |
| Delegate Authority | Allowed | Not allowed | Not allowed |
| Other Rights | Full Access Role | Auditor Role | New Role Defaults |
| Alerts | Full (Can Dismiss Global Alerts) | View-Only | View-Only |
| Alert Configuration | Full (Can Edit Alert Configurations) | View-Only | View-Only |
| IP Lists | Full (Can Create, Edit, Delete) | View-Only | View-Only |
| Port Lists | Full (Can Create, Edit, Delete) | View-Only | View-Only |
| Schedules | Full (Can Create, Edit, Delete) | View-Only | View-Only |
| System Settings (Global) | Full (Can View, Edit System Settings (Global)) | View-Only | Hide |
| Diagnostics | Full (Can Create Diagnostic Packages) | View-Only | View-Only |
| Tagging | Full (Can Tag (Items not belonging to Computers), Can Delete Tags, Can Update Non-Owned Auto-Tag Rules, Can Run Non-Owned Auto-Tag Rules, Can Delete Non-Owned Auto-Tag Rules) | View-Only | View-Only |
| Tasks | Full (Can View, Add, Edit, Delete Tasks, Execute Tasks) | View-Only | Hide |
| Multi-Tenant Administration | Full | Hide | View-Only |
| Scan Cache Configuration Administration | Full | View-Only | View-Only |
| Contacts | Full (Can View, Create, Edit, Delete Contacts) | View-Only | Hide |
| Licenses | Full (Can View, Change License) | View-Only | Hide |
| Updates | Full (Can Add, Edit, Delete Software; Can View Update For Components; Can Download, Import, Apply Update Components; Can Delete Deep Security Rule Updates) | View-Only | Hide |
| Asset Values | Full (Can Create, Edit, Delete Asset Values) | View-Only | View-Only |
| Certificates | Full (Can Create, Delete SSL Certificates) | View-Only | View-Only |
| Relay Groups | Full | View-Only | View-Only |
| Proxy | Full | View-Only | View-Only |
| SAML Identity Providers | Full | Hide | Hide |
| Malware Scan Configuration | Full (Can Create, Edit, Delete Malware Scan Configuration) | View-Only | View-Only |
| Quarantined File | Full (Can Delete, Download Quarantined File) | View-Only | View-Only |
| Web Reputation Configuration | Full | View-Only | View-Only |
| Directory Lists | Full (Can Create, Edit, Delete) | View-Only | View-Only |
| File Lists | Full (Can Create, Edit, Delete) | View-Only | View-Only |
| File Extension Lists | Full (Can Create, Edit, Delete) | View-Only | View-Only |
| Firewall Rules | Full (Can Create, Edit, Delete Firewall Rules) | View-Only | View-Only |
| Firewall Stateful Configurations | Full (Can Create, Edit, Delete Firewall Stateful Configurations) | View-Only | View-Only |
| Intrusion Prevention Rules | Full (Can Create, Edit, Delete) | View-Only | View-Only |
| Application Types | Full (Can Create, Edit, Delete) | View-Only | View-Only |
| MAC Lists | Full (Can Create, Edit, Delete) | View-Only | View-Only |
| Contexts | Full (Can Create, Edit, Delete) | View-Only | View-Only |
| Integrity Monitoring Rules | Full (Can Create, Edit, Delete) | View-Only | View-Only |
| Log Inspection Rules | Full (Can Create, Edit, Delete) | View-Only | View-Only |
| Log Inspection Decoders | Full (Can Create, Edit, Delete) | View-Only | View-Only |
The custom settings corresponding to the Change own password and contact information only option are listed in the following table:
| Custom settings corresponding to "Change own password and contact information only" option | |
| Users | |
| Can View Users | Not allowed |
| Can Create New Users | Not allowed |
| Can Edit User Properties (User can always edit select properties of own account) | Not allowed |
| Can Delete Users | Not allowed |
| Roles | |
| Can View Roles | Not allowed |
| Can Create New Roles | Not allowed |
| Can Edit Role Properties (Warning: conferring this right will let Users with this Role edit their own rights) | Not allowed |
| Can Delete Roles | Not allowed |
| Delegate Authority | |
| Can only manipulate Users with equal or lesser rights | Not allowed |
The custom settings corresponding to the Create and manage Users with equal or less access option are listed in the following table:
| Custom settings corresponding to "Create and manage Users with equal or less access" option | |
| Users | |
| Can View Users | Allowed |
| Can Create New Users | Allowed |
| Can Edit User Properties (User can always edit select properties of own account) | Allowed |
| Can Delete Users | Allowed |
| Roles | |
| Can View Roles | Not allowed |
| Can Create New Roles | Not allowed |
| Can Edit Role Properties (Warning: conferring this right will let Users with this Role edit their own rights) | Not allowed |
| Can Delete Roles | Not allowed |
| Delegate Authority | |
| Can only manipulate Users with equal or lesser rights | Allowed |
The custom settings corresponding to the Have full control over all Roles and Users option are listed in the following table:
| Custom settings corresponding to "Have full control over all Roles and Users" option | |
| Users | |
| Can View Users | Allowed |
| Can Create New Users | Allowed |
| Can Edit User Properties (User can always edit select properties of own account) | Allowed |
| Can Delete Users | Allowed |
| Roles | |
| Can View Roles | Allowed |
| Can Create New Roles | Allowed |
| Can Edit Role Properties (Warning: conferring this right will let Users with this Role edit their own rights) | Allowed |
| Can Delete Roles | Allowed |
| Delegate Authority | |
| Can only manipulate Users with equal or lesser rights | Not applicable |