Deep Security Manager 10 has reached end of support. Use the version selector (above) to see more recent versions of the Help Center.
Automated policy management in NSX environments
Applies to on-premise Deep Security software installations only
See Deploy Deep Security for steps that you must perform before proceeding with the steps in this article.
Before you begin, make sure you've followed the NSX set-up steps to deploy the appliance with NSX.
Once you've completed the tasks below, move on to Create NSX security groups and policies.
The security configuration of a VM in an NSX environment can be automatically modified based on changes to the VM's NSX Security Group. To automate the security configuration, use the NSX Security Group Change Event-Based Task.
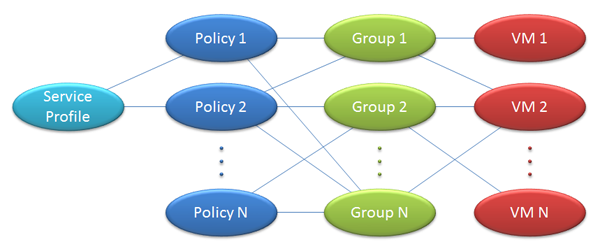
VMs are associated with NSX Security Groups, NSX Security Groups are associated with NSX Security Policies, and NSX Security Policies are associated with NSX Service Profiles.
"NSX Security Group Change" event-based task
Deep Security has event-based tasks (EBTs) that can be configured to perform actions when specific events with specific conditions are detected. The NSX Security Group Change EBT exists to let you modify the protection settings of a VM if changes to the NSX Security Group that a VM belongs to are detected.
To modify that task, in Deep Security Manager, go to Administration > Event-Based Tasks.
The NSX Security Group Change EBT is triggered when any of the following events occur:
- A VM is added to an NSX Group that is (indirectly) associated with theDefault (EBT) NSX Service Profile.
- A VM is removed from an NSX Group that is associated with the Default (EBT) NSX Service Profile.
- An NSX Policy associated with the Default (EBT) NSX Service Profile is applied to an NSX Group.
- An NSX Policy associated with the Default (EBT) NSX Service Profile is removed from an NSX Group.
- An NSX Policy is associated with the Default (EBT) NSX Service Profile.
- An NSX Policy is removed from the Default (EBT) NSX Service Profile.
- An NSX Group that is associated with an Default (EBT) NSX Service Profile changes name.
An event is triggered for each individual VM affected by a change.
Conditions under which to perform tasks
The following conditions are applicable to the NSX Security Group Change event-based task and can be tested against before performing an action:
- Computer Name: The hostname of the VM.
- ESXi Name: The Hostname of the ESXi the VM is a guest on.
- Folder Name: The name of the VM's folder in the ESXi folder structure.
- NSX Security Group Name: The name of the NSX Security Group that has undergone a change.
- Platform: the operating system of the VM.
- vCenter name; The name of the vCenter the VM is a part of.
- Appliance Protection Available: A Deep Security Virtual Appliance is available to protect VMs on the ESXi on which the VM is hosted. The VM may or may not be in a "Activated" state.
- Appliance Protection Activated: A Deep Security Virtual Appliance is available to protect VMs on the ESXi on which the VM is hosted and the VM is "Activated".
- Last Used IP Address: The current or last known IP address of the computer.
The NSX Security Group Name condition is explicitly for changes to the NSX Security Group Change event-based task.
It accepts a java regular expression match to the NSX Security Group the VM belongs to whose properties have changed. Two special cases are considered:
- A match for membership in any group. In this case the recommended regular expression is ".+".
- A match for membership in no groups. In this case the recommended regular expression is "^$".
Other regular expressions can include a specific group name or partial name (to match more than one group) as desired.
Available actions
The following actions can be performed on a VM when Deep Security detects a change to the NSX Security Group the VM belongs to:
- Activate Computer: Activate Deep Security protection by the Deep Security Virtual Appliance. Use this when a VM is moved into a Deep Security-protected NSX Security Group.
- Deactivate Computer: Deactivate Deep Security protection by the Deep Security Virtual Appliance. Use this when moving a VM out of a Deep Security-protected NSX Security Group. An Alert will be raised if this action is not performed when a VM is moved out a NSX Security Group protected by Deep Security because the VM can no longer be protected.
- Assign Policy: Assign a Deep Security Policy to a VM.
- Assign Relay Group: Assign a Relay Group to a VM.
Event-based tasks created when adding a vCenter to Deep Security Manager
Two event-based tasks can be created when adding an NSX vCenter to DSM. The last page of the Add vCenter wizard displays a checkbox. If selected, this option creates two event-based tasks. One to activate VMs when protection is added and the other to deactivate VMs when protection is removed.
The first event-based task is configured as follows:
- Name: Activate <vCenter Name>, where <vCenter Name> is the value seen in the Name field on the vCenter properties.
- Event: NSX Security Group Changed
- Task Enabled: True
- Action: Activate Computer after a delay of five minutes
- Conditions:
- vCenterName: <vCenter Name> Must match because the EBT is vCenter-specific.
- Appliance Protection Available: True. Must have an activated Deep Security Virtual Appliance deployed on the same ESXi.
- Appliance Protection Activated: False. This only applies to unactivated VMs.
- NSX Security Group: ".+". Must be a member of one or more Deep Security Groups.
You can modify the actions associated with this event-based task, for example by applying a Deep Security protection policy or assigning a different relay group. The actions (and other properties) of any existing event-based tasks can be edited on the Administration > Event-Based Tasks page in the Deep Security Manager.
The second event-based task is configured as follows:
- Name: Deactivate <vCenter Name>, where <vCenter Name> is the value seen in the Name field on the vCenter properties.
- Event: NSX Security Group Changed
- Task Enabled: False
- Action: Deactivate Computer
- Conditions:
- vCenterName: <vCenter Name>. Must match because the event-based task is vCenter-specific.
- Appliance Protection Activated: True. This only applies to activated VMs.
-
NSX Security Group: "^$". Must not be a member of any Deep Security Group.
This event-based task is disabled by default. You can enable it and customize it as desired after the vCenter installation is complete.
Removal of a vCenter from Deep Security Manager
Whenever a vCenter is removed from Deep Security Manager, it disables all event-based tasks that meet the following criteria:
-
The vCenter Name condition matches the name of the vCenter being removed.
This must be an exact match. Event-based tasks which match multiple vCenter names will not be disabled.
- The event-based task Event Type is "NSX Security Group Changed". Event-based tasks with other event types are not disabled.
To remove a vCenter from Deep Security Manager, you'll first need to remove Deep Security artifacts from NSX. For instructions on removing Deep Security from NSX and vCenter from Deep Security Manager, see Uninstall Deep Security from your NSX environment.