Deep Security Manager 10 has reached end of support. Use the version selector (above) to see more recent versions of the Help Center.
Integrate with VMware vRealize Operations Manager
Deep Security support for the vRealize Operations adapter ended Dec 31, 2018.
The Deep Security Management Pack for vRealize Operations (vROps) displays security events that occur on your protected virtual machines in the vROps console. Security and operational data appear simultaneously so that you can correlate security status with the overall health of your virtual data center.
The Deep Security Management Pack for vRealize Operations does not support application control.
During each data collection cycle, the management pack connects to Deep Security Manager and queries it for specific metrics. The management pack collects performance data, relationships, and events for Trend Micro Deep Security resources.
- Requirements
- Download the management pack
- Install and Configure
- Migrate from a 5.x Environment
- Navigate Deep Security in vROps
- Dashboards
- Metrics
- Alerts, Symptoms, and Recommendations
Requirements
Before you install the management pack, ensure that your system meets the following requirements.
Deep Security:
- Deep Security 10.0 is installed. Note that versions 9.5 and 9.6 are also supported.
- Access to the Deep Security Manager web console via a web browser
- Deep Security Manager user name and password
- The Deep Security Manager server has network access to the vCenter on which VMware vRealize Operations Manager is installed
- The management pack package is stored in a local directory that is available to the VMware vRealize Operations Manager web console
- The management pack certificate import script (import-cert)
VMware vRealize Operations Management:
- VMware vCenter is installed
- VMware vRealize Operations Manager v6.0.x (Advanced Edition) is installed (requires custom dashboard functionality)
- vRealize User Name and Password
- SSH access to vRealize Operations Manager vApp
- Client Integration Plug-in 6.0.0 Build 4275819
Download the management pack
The Deep Security Management Pack for vROps is available to download from the Deep Security Software page. Click the tab for the current version of Deep Security, and click the link in the Support Files area.
Install and Configure
To install and configure the management pack, complete the following tasks:
- Create a vRealize Operations Manager user account in Deep Security Manager
- Enable SOAP Web Services in Deep Security Manager
- Export the Deep Security Manager certificate
- Import the Deep Security Manager certificate into vRealize Operations Manager
- Install the Deep Security Management Pack in vRealize Operations
- Configure the Deep Security Management Pack in vRealize Operations
- Validate Data Collection in vRealize Operations
Create a vRealize Operations Manager user account in Deep Security Manager
Create a read-only Auditor account that the management pack uses to access Deep Security Manager.
- In the Deep Security Manager console, click Administration > User Management > Users.
- Click New and create a new User account with the role of Auditor.
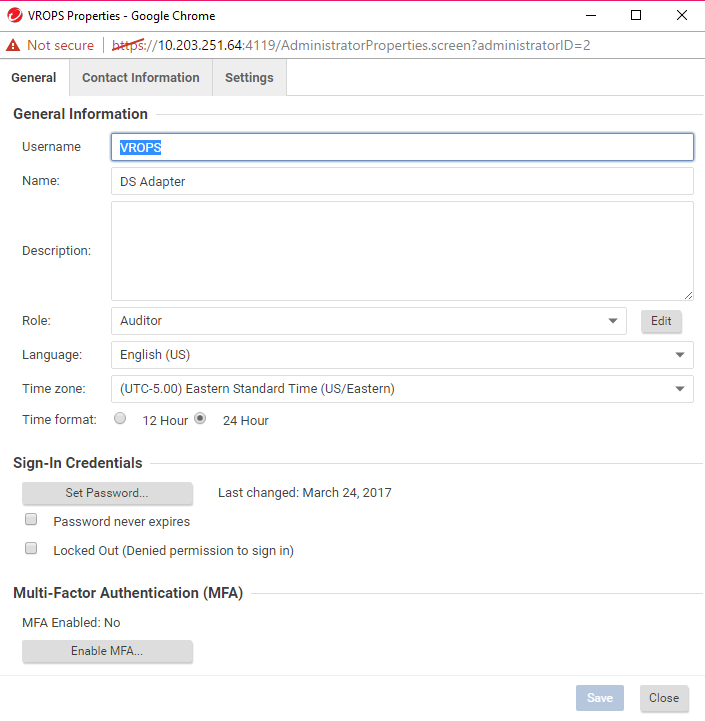
Take note of the Username and Password for the user account. You will need these credentials when installing the management pack in VMware vRealize Operations Manager.
Enable SOAP Web Services in Deep Security Manager
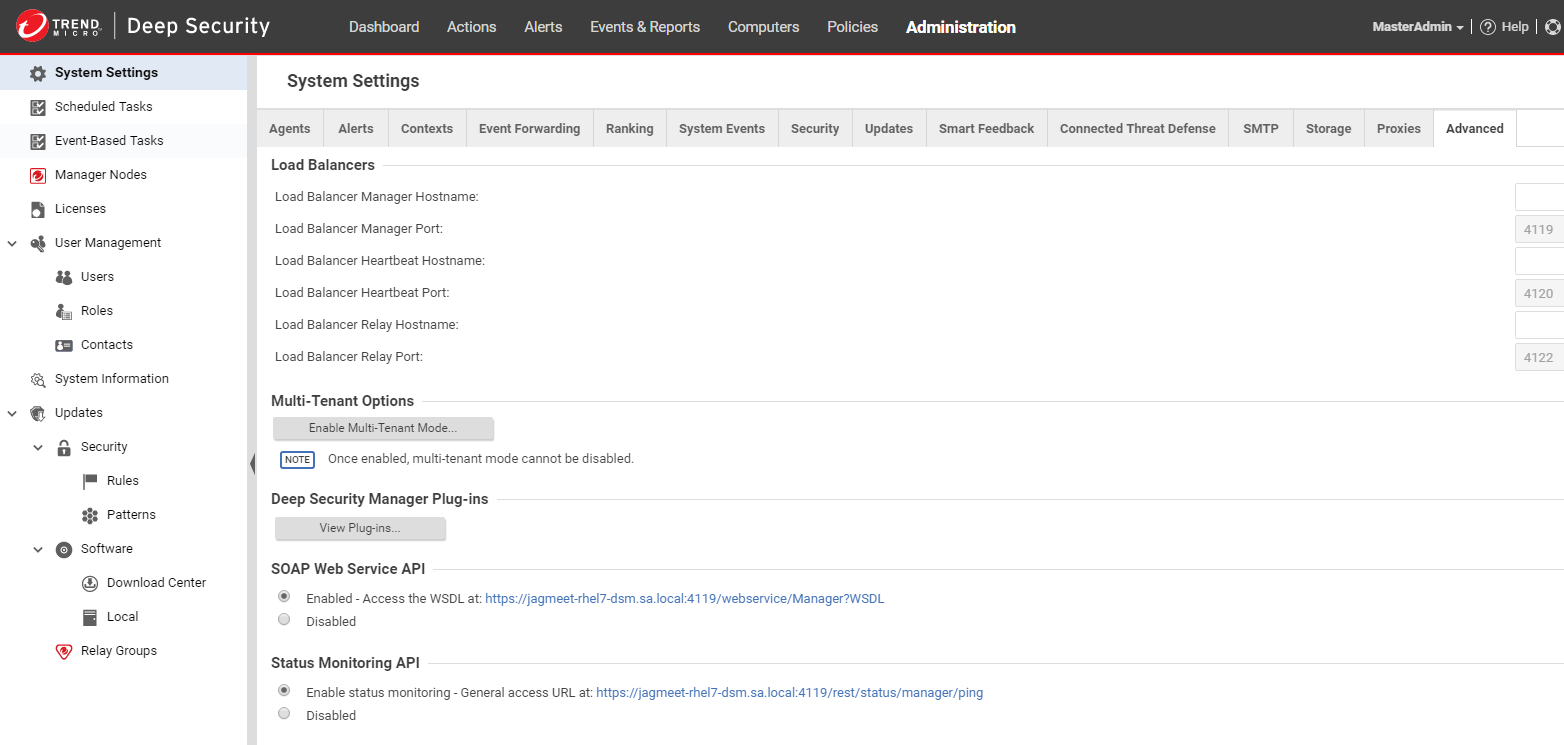
- In the Deep Security Manager console, click Administration > System Settings > Advanced.
- In the SOAP Web Service API section, select Enabled.
Export the Deep Security Manager certificate
The procedures for exporting a security certificate vary across browsers and browser versions. The following steps apply to Mozilla Firefox 33. If you are not using Firefox 33, see your browser’s documentation for instructions.
- Sign in to Deep Security Manager.
- Click Menu > Options.
- On the Advanced panel, click the Certificates tab and then click View Certificates to open the Certificates Manager window.
- In the Certificate Manager window, click the Servers tab and select the Deep Security Manager server name.
- Click Export and select "X.509 Certificate (DER)" as the format.
- Save the certificate.
Import the Deep Security Manager certificate into vRealize Operations Manager
In cluster-based environments, you must import the certificate on each collector node.
- On the vROps computer, as the root user copy the import-cert script and Deep Security Manager certificate to the /root directory. (You downloaded the script with the management pack. See Download the management pack.)
- In a terminal, enter the following command to change directories:
cd $VCOPS_DATA_VCOPS/user/conf/ssl - Enter the following command to view the storePass.properties file:
cat storePass.properties - Copy the ssl truststore password.
- Enter the following command to edit the import-cert file:
vi import-cert - Modify the file with your environment-specific information:
CERT="/root/xxxxxxx.der"
PASS="xxxxxxxxxx" - Save the import-cert file.
- Enter the following command to add the execute permission to the import-cert script:
chmod +x import-cert - Run the import-cert script:
./import-cert - Run the script again to ensure that the keytool error does not occur:
./import-cert>The output is similar to the following example:
/root/xxxxxxx.der will be imported into the vC Ops trust store.
Do you wish to import a different certificate ? (y/n) n
Deleting Deep Security Manager certificate (ignore errors) ...
Importing Deep Security Manager certificate /root/xxxxxxx.der ...
Certificate was added to keystore - Reboot all vRealize Operations nodes to ensure the certificate is recognized as trusted.
The output should look appear similar to the following example:
sslkeystorePassword=xxxxxxxxxxxxx
ssltruststorePassword=xxxxxxxxxxxxx
where /root/xxxxxxx.der is the certificate that you copied to the /root directory, and PASS is the ssl truststore password that you obtained in a previous step.
The script output is similar to the following example. The keytool error is expected:
/root/xxxxxx.der will be imported into the vC Ops trust store.
Do you wish to import a different certificate ? (y/n) n
Deleting Deep Security Manager certificate (ignore errors) ...
keytool error: java.lang.Exception: Alias <Deep_Security_Manager> does not exist
Importing Deep Security Manager certificate /root/xxxxxxx.der ...
Certificate was added to keystore
Install the Deep Security Management Pack in vRealize Operations
Install the pak file that you downloaded from the Deep Security Software page (see Download the management pack).
The Deep Security Management Pack for vRealize Operations is distributed as a .pak file. Before installing the .pak file in vROps, read the included release notes and back up any customized dashboards because they are overwritten during the installation.
- Save the .pak file in a temporary folder.
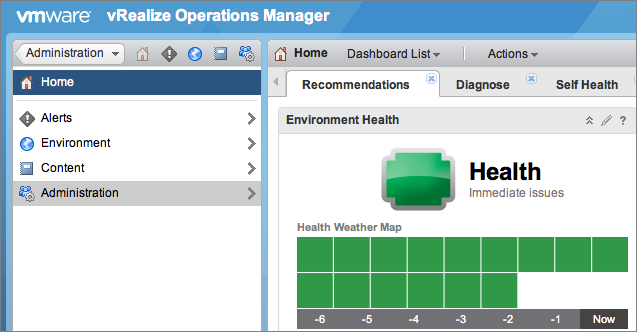
- Log in to vROps as an admin user.
- Click the Home icon, then click the Administration icon in the left pane.

- To upload the .pak file to the vROps server, on the Solutions tab of the right-side pane, click the Add icon.

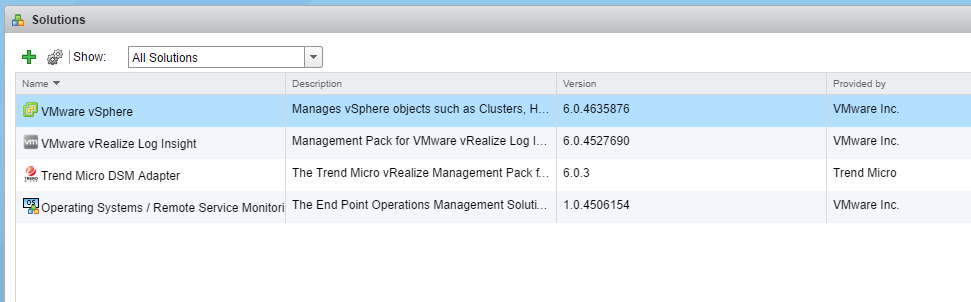
- In the dialog box that appears, browse to the location of the saved .pak file, then click Upload.
The .pak file can require several minutes to upload. Status information appears in the Installation Details text box throughout the installation process.
- Click Next when the upload is complete. Read the End User License Agreement (EULA), select the I accept the terms of this agreement checkbox to accept the terms, then click Next.
- Click Finish when the installation process is complete.
Configure the Deep Security Management Pack in vRealize Operations
Add an instance of the Deep Security Management adapter instance and specify the credentials to use. The adapter instance defines the adapter type and identifies the host from which the management pack retrieves data. The credential uses a DSM user name and password to connect to Deep Security Manager.
- In vROps, click the Administration icon.

- In the Solutions list, select Trend Micro DSM Adapter.
- Click the Configure icon to open the Manage Solution dialog.

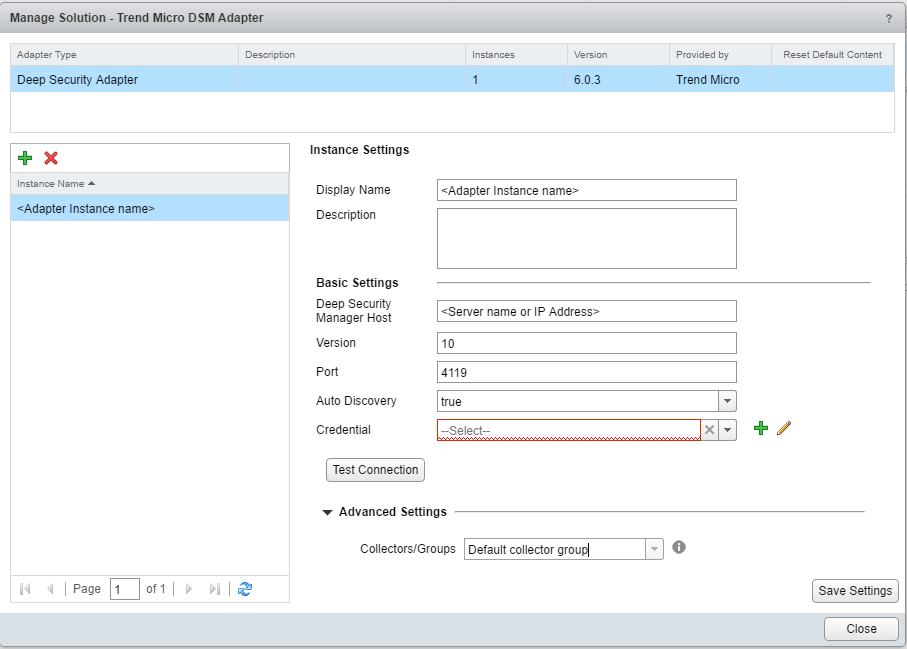
- In the Manage Solution window, enter the following property values:
- Display Name: A name to identify this instance of the Deep Security adapter
- Description: (Optional) A useful description of the adapter
- Auto Discovery: true
- Deep Security Manager Host: The server name or IP address of Deep Security Manager
- Port: 4119
- Version: The version number of Deep Security Manager (for example, 10.0)
- Credential: Click the Add icon.
 Enter the credentials for the Deep Security User Account that you created in the Create a vRealize Operations Manager user account in Deep Security Manager section:
Enter the credentials for the Deep Security User Account that you created in the Create a vRealize Operations Manager user account in Deep Security Manager section: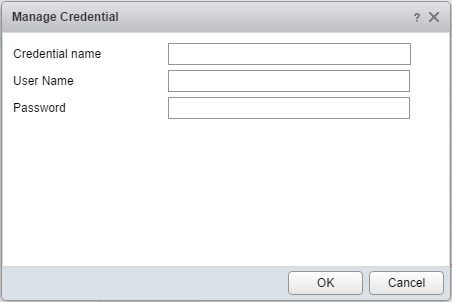
- Click the Test Connection button to ensure that vROps and the Deep Security Management Pack can connect to the Deep Security Manager account.
- Click Save Settings to save the credentials.
Validate Data Collection in vRealize Operations
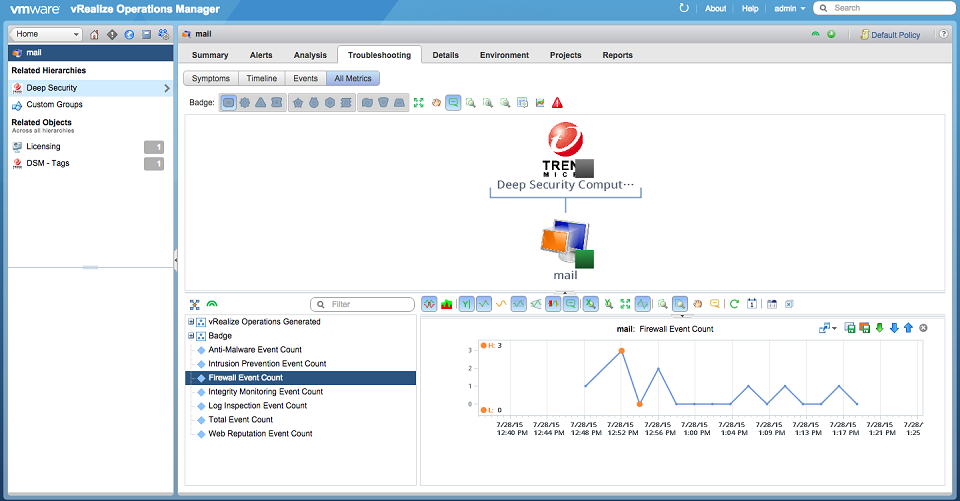
After adding a Deep Security adapter instance, you can validate the data that it collects within vROps.
- Select the Environment shortcut.
- Under Inventory Trees, select All Objects, then expand the Deep Security Adapter objects list.
- Select a resource from the list, then click the Troubleshooting tab and All Metrics to validate values against the data source.
Migrate from a 5.x Environment
Migration is not recommended due to significant changes that were made to object definitions. However, if you must migrate from a 5.x environment, perform the following procedure:
- Ensure that Auto Discovery is set to False before migrating from the 5.x version of the Deep Security Management Pack.
- Remove the 5.x versions of the Deep Security dashboards after migrating.
- For each Deep Security Computer and Deep Security ESXi Host, fill in the Parent Deep Security Adapter Instance identifier with the name of the adapter instance.
- Start collection for all Deep Security resources.
Navigate Deep Security in vROps
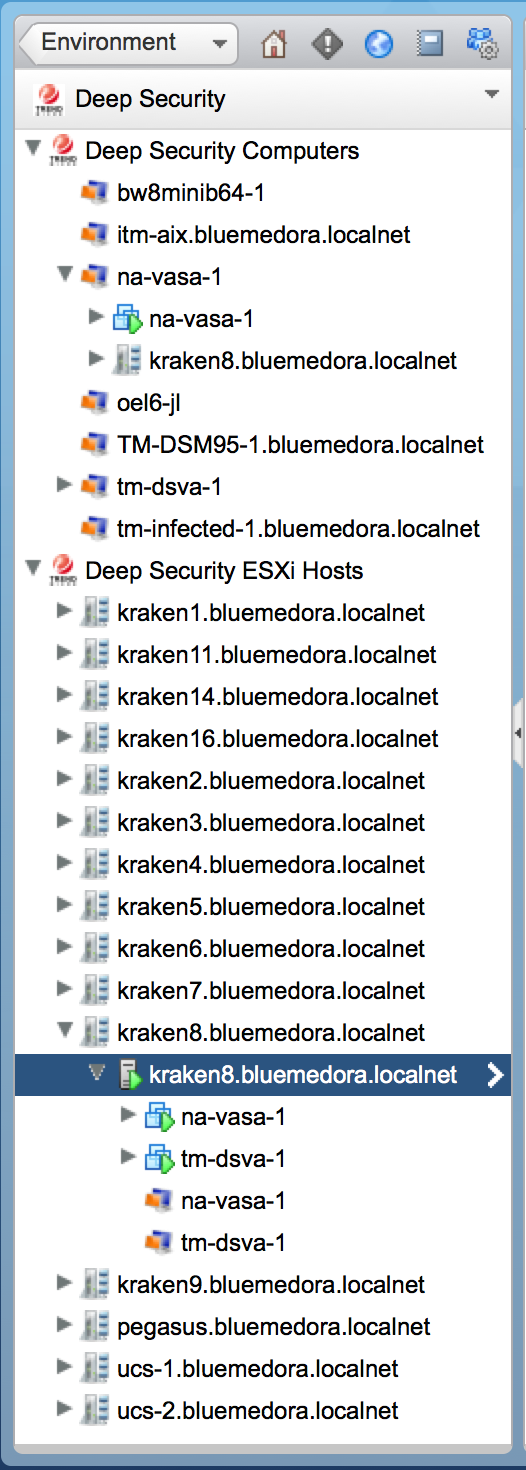
Use the vROps Inventory Tree (TraversalSpec) to navigate your Deep Security environment. The adapter recognizes the following resource kinds:
| Resource Kind | Description | Icon | Identifiers |
| Deep Security Adapter Instance | Your configured adapter instance for the Management Pack |

|
Deep Security Manager Host Version Port Auto Discovery |
| Deep Security ESXi Host | ESXi Host monitored by Deep Security |

|
Deep Security ID Virtual Machine Uuid Virtual Machine Moid |
| Deep Security Computer | Server monitored by Deep Security |

|
Deep Security ID Virtual Machine Uuid Virtual Machine Moid |
| DSM - Tags | Used for creating tags related to Trend Micro Deep Security Manager systems |

|
N/A |
The hierarchical structure shows relationships among resource kinds and enables you to drill down to root-cause issues.
Dashboards
Dashboards are the primary user interface for monitoring and troubleshooting Deep Security issues in vROps. The following custom dashboards are available in the management pack:
- Deep Security Top 10 Analysis
- Deep Security Troubleshooting
- Deep Security Total Event Count Heat Map
To see the Deep Security dashboards in vROps, go to Dashboard List > Trend Micro.
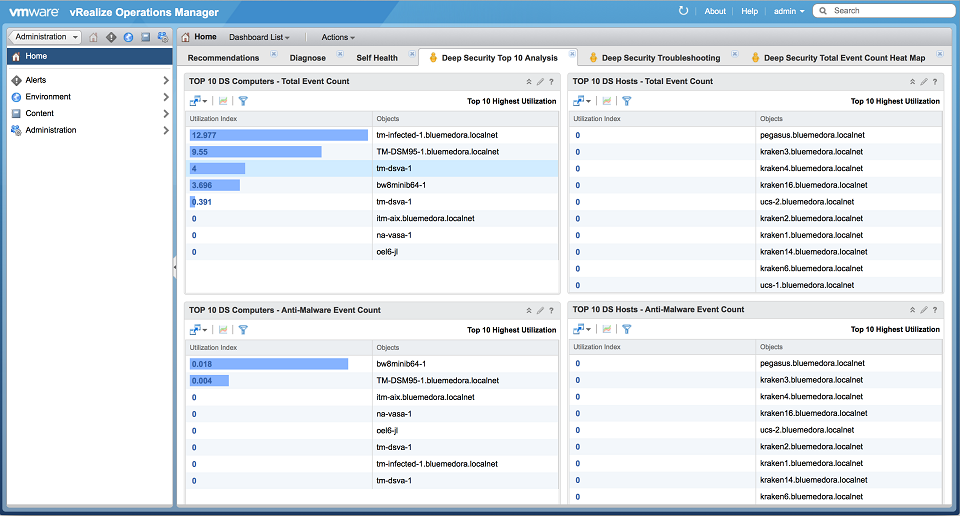
Deep Security Top 10 Analysis
This dashboard displays the top 10 resources by total event count for key performance metrics (KPIs).
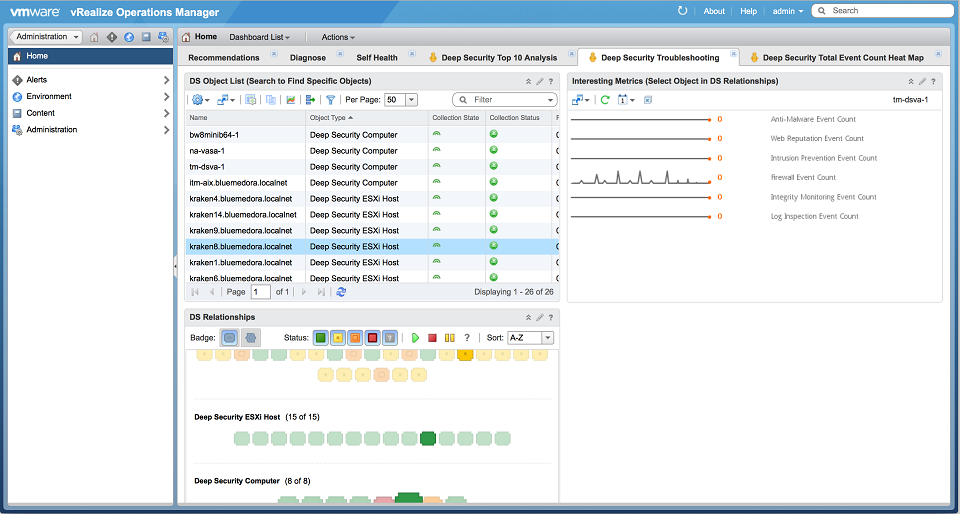
Deep Security Troubleshooting
This dashboard displays health information regarding Deep Security resources in a relationships view as well as KPIs for the selected Deep Security resource.
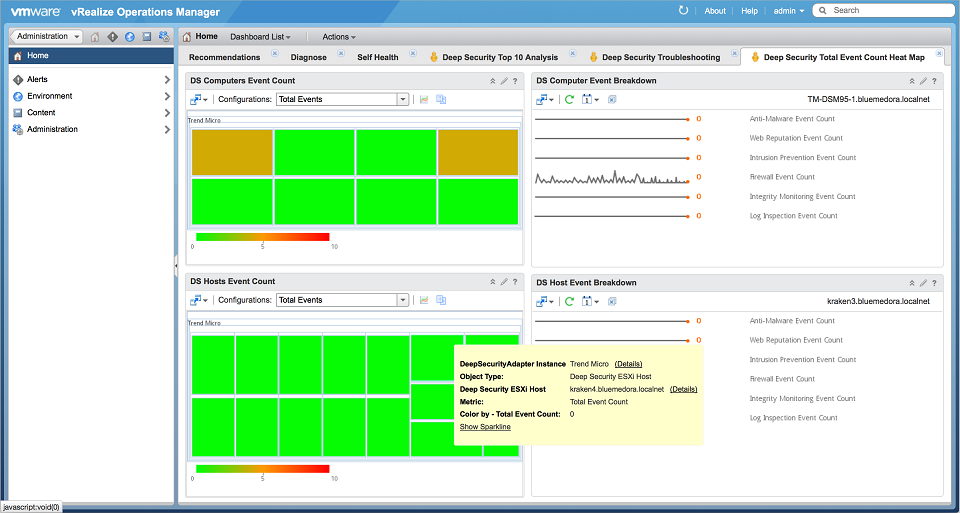
Deep Security Total Event Count Heat Map
This dashboard displays at-a-glance data regarding all Deep Security Manager events, using heat maps and event breakdown charts.
Metrics
The Management Pack collects data for the following metrics for Deep Security resource kinds.
| Metric Name | Type | Description |
| Intrusion Prevention Event Count | integer | Number of Intrusion Prevention Events recorded |
| Firewall Event Count | integer | Number of Firewall Events recorded |
| Integrity Monitoring Event Count | integer | Number of Integrity Events recorded |
| Log Inspection Event Count | integer | Number of Log Inspection Events recorded |
| Total Event Count | integer | Number of Total Events recorded |
| Anti-Malware Event Count | integer | Number of Anti-Malware Events recorded |
| Web Reputation Event Count | integer | Number of Web Reputation Events recorded |
Alerts, Symptoms, and Recommendations
The Management Pack creates alerts and provides recommended actions based on various symptoms that it detects in the environment. The table below provides details about each alert.
| Name | Description or Symptom | Recommendation |
| alert_Abnormal_Restart_Detected | Abnormal Restart Detected | An abnormal restart was detected on the computer. This event can have many causes. If you suspect that the agent or appliance is the root cause, invoke the diagnostics package (located in the Support section of the Computer Details dialog). |
| alert_Activation_Failed | Activation Failed | The agent or appliance could not be activated. Check the affected computers. |
| alert_A_Deep_Security_Relay_cannot_download_security_components | A Deep Security Relay cannot download security components | A Deep Security Relay can't successfully download security components. This might be due to network connectivity issues or misconfigurations in Deep Security Manager under Administration > System Settings > Updates. Check your network configurations (for example, the proxy settings of the relay group) and System Settings, and then manually initiate an update on the relay using the Download Security Update option on the Administration > Updates > Software page. |
| alert_Agent_configuration_package_too_large | Agent configuration package too large | This alert is usually caused by too many firewall and intrusion prevention rules being assigned. Run a recommendation scan on the computer to determine whether any rules can be safely unassigned. |
| alert_Agent_Installation_Failed | Agent Installation Failed | The agent failed to install successfully on one or more computers. The computers are currently unprotected. Reboot the computers to automatically install the agent. |
| alert_Agent_Upgrade_Recommended_Incompatible_with_Appliance | Agent Upgrade Recommended (Incompatible with Appliance) | A computer is running a version of the agent that is not compatible with the appliance. In this situation, the appliance filters network traffic, resulting in redundant protection. |
| alert_Agent_Appliance_Upgrade_Recommended | Agent or Appliance Upgrade Recommended | A computer is running an older version of the agent or appliance that does not support all available features. An upgrade of the agent or appliance software is recommended. |
| alert_Agent_Appliance_Upgrade_Recommended_Incompatible_ Security_Updates |
Agent or Appliance Upgrade Recommended (Incompatible Security Update(s) | A computer is running a version of the agent or appliance that is not compatible with one or more security updates assigned to it. An upgrade of the agent or appliance software is recommended. |
| alert_Agent_Appliance_Upgrade_Recommended_ New_Version_Available |
Agent or Appliance Upgrade Recommended (New Version Available | One or more computers is running a version of the agent or appliance that is older than the latest version imported into the manager. An upgrade of the agent or appliance software is recommended. |
| alert_Agent_Appliance_Upgrade_Required | Agent or Appliance Upgrade Required | A computer is running a version of the agent or appliance that is not compatible with this version of the manager. Upgrade of the agent or appliance software. |
| alert_An_update_to_the_Rules_is_available | An update to the Rules is available | A rules update is available. Go to Administration > Updates > Security > Rules and reapply the most recently applied rule update. If you do not reapply the rule update now, the new features in the update will be applied with the application of the next rule update. |
| alert_Anti-Malware_Alert | Anti-Malware Alert | A malware scan configuration has raised an alert on one or more computers. |
| alert_Anti-Malware_Component_Failure | Anti-Malware Component Failure | An anti-malware component failed on one or more computers. See the event descriptions on the individual computers for specific details. |
| alert_Anti-Malware_Component_Update_ Failed |
Anti-Malware Component Update Failed | One or more agents or relays failed to update its anti-malware components. See the affected computers for more information. |
| alert_Anti-Malware_Engine_Offline | Anti-Malware Engine Offline | The agent or appliance has reported that the anti-malware engine is not responding. Check the system events for the computer to determine the cause of the failure. |
| alert_Anti-Malware_protection_is_absent_or_out_of_date | Anti-Malware protection is absent or out of date | The agent on this computer has not received its initial anti-malware protection package, or its anti-malware protection is out of date. Make sure a relay is available and that the agent is configured to communicate with it. To configure relays and other update options go to Administration > System Settings > Updates. |
| alert_Anti-Malware_Quarantine_Alert_for_Storage_Limit | Anti-Malware Quarantine Alert for Storage Limit | Anti-malware failed to quarantine a file because the storage limit has been reached. |
| alert_Application_Type_Misconfiguration | Application Type Misconfiguration | Misconfiguration of application types can prevent proper security coverage. Review the system events for details. |
| alert_Application_Type_Recommendation | Application Type Recommendation |
A computer on the network should be assigned an application type due to one of the following scenarios:
To assign the application type to the computer, open the Computer Details dialog box, click Intrusion Prevention Rules and assign the Application Type. |
| alert_Certified_Safe_Software_Service_Offline | Certified Safe Software Service Offline | A Deep Security Manager node cannot connect to the Trend Micro Certified Safe Software Service to perform file signature comparisons for the integrity monitoring module. A locally-cached database will be used until connectivity is restored. Make sure the manager node has Internet connectivity and that proxy settings (if used) are correct. |
| alert_Clock_Change_Detected | Clock Change Detected | A clock change has been detected. Unexpected clock changes may indicate a problem on the computer and should be investigated before the alert is dismissed. |
| alert_Communications_Problem_Detected | Communications Problem Detected | A communications problem has been detected. Communications problems indicate that the computer cannot initiate communication with the Deep Security Manager(s) due to network configuration or load issues. Check the system events and verify that communications can be established to the Deep Security Manager(s). The cause of the problem should be investigated before the alert is dismissed. |
| alert_Computer_Not_Receiving_Updates | Computer Not Receiving Updates | One or more computers have stopped receiving updates. Manual intervention may be required. |
| alert_Computer_Reboot_Required | Computer Reboot Required | An agent software upgrade was successful but the computer must be rebooted to complete the install. Reboot the computer before you dismiss the alert. |
| alert_Computer_Reboot_Required_for_Anti-Malware_Protection | Computer Reboot Required for Anti-Malware Protection | The anti-malware protection on the agent indicates that the computer needs to be rebooted. Please check the system events for the computer to determine the reason for the reboot. |
| alert_Configuration_Required | Configuration Required | One or more computers are using a policy that defines multiple interface types and not all interfaces have been mapped. |
| alert_Connection_to_Filter_Driver_Failure | Connection to Filter Driver Failure | An appliance failed to connect to the filter driver. This may indicate a configuration issue with the filter driver running on the ESXi or with the appliance. The appliance must connect to the filter driver to protect guests. Investigate and resolve the cause of the issue. |
| alert_CPU_Critical_Threshold_Exceeded | CPU Critical Threshold Exceeded | The CPU critical threshold has been exceeded. |
| alert_CPU_Warning_Threshold_Exceeded | CPU Warning Threshold Exceeded | The CPU warning threshold has been exceeded. |
| alert_Duplicate_Computer_Detected | Duplicate Computer Detected | A duplicate computer has been activated or imported. Remove the duplicate computer and, if necessary, reactivate the original computer. |
| alert_Duplicate_Unique_Identifiers_Detected | Duplicate Unique Identifiers Detected | Consult Assign unique UUIDs to new virtual machines and VM BIOS UUIDs are not unique when virtual machines are deployed from vApp templates for information about troubleshooting duplicate UUIDs. |
| alert_Empty_Relay_Group_Assigned | Empty Relay Group Assigned | These computers have been assigned an empty relay group. Assign a different relay group or add relays to the empty relay group. |
| alert_Events_Suppressed | Events Suppressed | The agent or appliance encountered a high volume of events. As a result, one or more events were suppressed (not recorded) to prevent a potential denial of service. Check the firewall events to determine the cause of the suppression. |
| alert_Events_Truncated | Events Truncated | Some events were lost because the data file grew too large for the agent or appliance to store. The cause can be an unexpected increase in the number of events or the inability of the agent or appliance to send the data to Deep Security Manager. For more information see the properties of the events truncated system event on the computer. |
| alert_Firewall_Engine_Offline | Firewall Engine Offline | The firewall engine is offline. Check the status of the engine on the agent or appliance. |
| alert_Firewall_Rule_Alert | Firewall Rule Alert | A firewall rule raised an alert on one or more computers. |
| alert_Firewall_Rule_Recommendation | Firewall Rule Recommendation | A computer on your network should be assigned a firewall rule. Either an agent was installed on a new computer and vulnerable applications were detected, or a new vulnerability was discovered in an installed application that was previously thought to be safe. To assign the firewall rule to the computer, open the Computer Details dialog box, click the Firewall Rules node and assign the firewall rule. |
| alert_Heartbeat_Server_Failed | Heartbeat Server Failed | The heartbeat server failed to start properly. A port conflict can cause this problem. Agents or appliances will not be able to contact the Manager until this problem is resolved. Ensure that another service is not using the port reserved for use by the heartbeat server and restart the Deep Security Manager service. If you do not want to use the heartbeat, turn this alert off in the Alert Configuration section. |
| alert_Incompatible_Agent_Appliance_Version | Incompatible Agent or Appliance Version | The version of the agent or appliance on the computer is more recent than the version of the manager and is not compatible. Upgrade the manager software. |
| alert_Insufficient_Disk_Space | Insufficient Disk Space | The agent or appliance was forced to delete an old log file to free up disk space for a new log file. Immediately free up disk space to prevent loss of intrusion prevention, firewall, and agent or appliance events. |
| alert_Integrity_Monitoring_Engine_Offline | Integrity Monitoring Engine Offline | The agent or appliance has reported that the integrity monitoring engine is not responding. Check the system events for the computer to determine the cause of the problem. |
| alert_Integrity_Monitoring_information_collection_has_been_delayed | Integrity Monitoring information collection has been delayed | The collection of integrity monitoring information is delayed due to an increase of integrity monitoring data. During this time, the baseline and Integrity Event views may not be current for some computers. This alert will be dismissed automatically when integrity monitoring data collection is no longer delayed. |
| alert_Integrity_Monitoring_Rule_Alert | Integrity Monitoring Rule Alert | An integrity monitoring rule produced an alert on one or more computers. |
| alert_Integrity_Monitoring_Rule_Compilation_Error | Integrity Monitoring Rule Compilation Error | An error was encountered when compiling an integrity monitoring rule on a computer. The rule might not operate as expected. |
| alert_Integrity_Monitoring_Rule_Recommendation | Integrity Monitoring Rule Recommendation | A computer on your network should be assigned an integrity monitoring rule. To assign the integrity monitoring rule to the computer, open the Computer Details dialog box, click the Integrity Monitoring > Integrity Monitoring Rules node and assign the integrity monitoring rule. |
| alert_Integrity_Monitoring_Rule_Requires_Configuration | Integrity Monitoring Rule Requires Configuration | An integrity monitoring rule that requires configuration before use has been assigned to one or more computers. This rule will not be sent to the computer(s). Open the integrity monitoring rule properties and select the Configuration tab for more information. |
| alert_Integrity_Monitoring_Trusted_Platform_Module_Not_Enabled | Integrity Monitoring Trusted Platform Module Not Enabled | Ensure that the hardware is installed and the BIOS setting is correct. |
| alert_Integrity_Monitoring_Trusted_Platform_Module_Register_ Value_Changed |
Integrity Monitoring Trusted Platform Module Register Value Changed | If you did not modify the ESXi hypervisor configuration, this alert can indicate an attack. |
| alert_Intrusion_Prevention_Engine_Offline | Intrusion Prevention Engine Offline | The intrusion prevention engine is offline. Check the status of the engine on the agent or appliance. |
| alert_Intrusion_Prevention_Rule_Alert | Intrusion Prevention Rule Alert | An intrusion prevention rule raised an alert on one or more computers. |
| alert_Intrusion_Prevention_Rule_Recommendation | Intrusion Prevention Rule Recommendation | A computer on your network should be assigned a intrusion prevention rule. Either an agent was installed on a new computer and vulnerable applications were detected, or a new vulnerability was discovered in an installed application that was previously thought to be safe. To assign the intrusion prevention rule to the computer, open the Computer Details dialog box, click Intrusion Prevention Rules and assign the rule. |
| alert_Intrusion_Prevention_Rule_Removal_Recommendation | Intrusion Prevention Rule Removal Recommendation | A computer on your network has an intrusion prevention rule assigned to it that is not required. Either a vulnerable application was uninstalled, an existing vulnerability was patched, or the rule was assigned unnecessarily. To unassign the intrusion prevention rule from the computer, open the Computer Details dialog box click Intrusion Prevention > Intrusion Prevention Rules. |
| alert_Intrusion_Prevention_Rule_Requires_Configuration | Intrusion Prevention Rule Requires Configuration | An intrusion prevention rule that requires configuration before use has been assigned to one or more computers. This rule will not be sent to the computer(s). Open the intrusion prevention rule properties and select the Configuration tab for more information. |
| alert_Log_Inspection_Engine_Offline | Log Inspection Engine Offline | The log inspection engine has failed to initialize. Check the system events for the computer to determine the cause of the failure. |
| alert_Log_Inspection_Rule_Alert | Log Inspection Rule Alert | A log inspection rule that is configured to produce alerts has been encountered on one or more computers. |
| alert_Log_Inspection_Rule_Recommendation | Log Inspection Rule Recommendation | A computer on your network should be assigned a log inspection rule. To assign the log inspection rule to the computer, open the Computer Details dialog box, click the Log Inspection > Log Inspection Rules node, and assign the log inspection rule. |
| alert_Log_Inspection_Rule_Requires_Configuration | Log Inspection Rule Requires Configuration | A log inspection rule that requires configuration before use has been assigned to one or more computers. This rule will not be sent to the computer(s). Open the log inspection rule properties and select the Configuration tab for more information. |
| alert_Low_Disk_Space | Low Disk Space | A Deep Security Manager node has less than 10% remaining disk space. Delete old or unnecessary files or add more storage capacity. |
| alert_Manager_Offline | Manager Offline | A Deep Security Manager node is offline. Either the computer has experienced a hardware or software problem, or it lost network connectivity. Check the status of the manager computer. |
| alert_Manager_Time_Out_of_Sync | Manager Time Out of Sync | The clock on each manager computer must be synchronized with the clock on the database. If the clocks are more than 30 seconds out of sync the manager does not function correctly. Synchronize the clock on the manager with the clock on the database. |
| alert_Memory_Critical_Threshold_Exceeded | Memory Critical Threshold Exceeded | The memory critical threshold has been exceeded. |
| alert_Memory_Warning_Threshold_Exceeded | Memory Warning Threshold Exceeded | The memory warning threshold has been exceeded. |
| alert_Multiple_Activated_Appliances_Detected | Multiple Activated Appliances Detected | Multiple connections have been made to the filter driver on the same ESXi. There may be multiple activated appliances running on the same ESXi, which is not supported. Investigate the cause of the problem before you dismiss the alert. |
| alert_Network_Engine_Mode_Incompatibility | Network Engine Mode Incompatibility | Setting Network Engine Mode to Tap is only available on agent versions 5.2 or higher. Review and update the agent's configuration or upgrade the agent. |
| alert_New_Pattern_Update_is_Downloaded_and_Available | New Pattern Update is Downloaded and Available | New patterns are available as part of a security update. The patterns have been downloaded to Deep Security Manager but have not yet applied to your computers. To apply the update to your computers go to the Administration > Updates > Security page. |
| alert_New_Rule_Update_is_Downloaded_and_Available | New Rule Update is Downloaded and Available | New rules are available as part of a security update. The rules have been downloaded to Deep Security Manager but have not yet been applied to policies and sent to your computers. To apply the update and send the updated policies to your computers go to the Administration > Updates > Security page. |
| alert_Newer_Version_of_Deep_Security_Manager_is_Available | Newer Version of Deep Security Manager is Available | A new version of Deep Security Manager is available. Download the latest version from the Trend Micro Download Center at http://downloadcenter.trendmicro.com. |
| alert_Newer_Versions_of_Software_Available | Newer Versions of Software Available | New software is available. Software can be downloaded from the Download Center. |
| alert_Number_of_Computers_exceeds_database_limit | Number of Computers exceeds database limit | The number of activated computers has exceeded the recommended limit for an embedded database. Performance will degrade rapidly if more computers are added. Consider another database option (Oracle or SQL Server). Contact Trend Micro for more information about upgrading your database. |
| alert_Protection_Module_Licensing_Expired | Protection Module Licensing Expired | The protection module license has expired. |
| alert_Protection_Module_Licensing_Expires_Soon | Protection Module Licensing Expires Soon | The protection module licensing will expire soon. Change your license on the Administration > Licenses page. |
| alert_Recommendation | Recommendation | The security configuration of one of your computers should be updated. To see what changes are recommended, open the computer's editor window and look through the module pages for warnings of unresolved recommendations. In the Assigned Rules area click Assign/Unassign... to display the list of available rules. Filter the rules using the Show Recommended for Assignment filter . |
| alert_Reconnaissance_Detected_Computer_OS_Fingerprint_Probe | Reconnaissance Detected: Computer OS Fingerprint Probe | An attempt to identify the computer operating system via a fingerprint probe was detected. Such activity is often a precursor to an attack that targets specific vulnerabilities. Check the computer's events to see the details of the probe. |
| alert_Reconnaissance_Detected_Network_or_Port_Scan | Reconnaissance Detected: Network or Port Scan | The agent or appliance detected network activity typical of a network or port scan. Such activity is often a precursor to an attack that targets specific vulnerabilities. Check the computer's events to see the details of the scan. |
| alert_Reconnaissance_Detected_TCP_Null_Scan | Reconnaissance Detected: TCP Null Scan | The agent or appliance detected a TCP Null scan. Such activity is often a precursor to an attack that targets specific vulnerabilities. Check the computer's events to see the details of the scan. |
| alert_Reconnaissance_Detected_TCP_SYNFIN_Scan | Reconnaissance Detected: TCP SYNFIN Scan | The agent or appliance detected a TCP SYNFIN scan. Such activity is often a precursor to an attack that targets specific vulnerabilities. Check the computer's events to see the details of the scan. |
| alert_Reconnaissance_Detected_TCP_Xmas_Scan | Reconnaissance Detected: TCP Xmas Scan | The agent or appliance detected a TCP Xmas scan. Such activity is often a precursor to an attack that targets specific vulnerabilities. Check the computer's events to see the details of the scan. |
| alert_Scheduled_Malware_Scan_Missed | Scheduled Malware Scan Missed | Scheduled malware scan tasks were initiated on computers that already have pending scan tasks. The scanning frequency might be too high. Either lower the scanning frequency or scan fewer computers during each scheduled scan job. |
| alert_Send_Policy_Failed | Send Policy Failed | Inability to send a policy may indicate a problem with the agent or appliance. Please check the affected computers. |
| alert_Smart_Protection_Server_Connection_Failed | Smart Protection Server Connection Failed | Failed to connect to a smart protection server. This could be due to a configuration issue or due to network connectivity. |
| alert_Software_Package_Not_Found | Software Package Not Found | An agent software package is required for the proper operation of one or more virtual appliances. Import a Red Hat Enterprise 6 (64 bit) agent Software Package with the correct version for each appliance. If the required version is not available, import the latest package and upgrade the appliance accordingly. |
| alert_Software_Updates_Available_for_Import | Software Updates Available for Import | New software is available. To import new software, go to Administration > Updates > Software > Download Center. |
| alert_Unable_to_communicate | Unable to communicate | Deep Security Manager has been unable to query the agent or appliance for its status within the configured period. Please check your network configuration and the affected computer's connectivity. |
| alert_Unable_to_Upgrade_the_Agent_Software | Unable to Upgrade the Agent Software | Deep Security Manager was unable to upgrade the agent software on the computer. |
| alert_Upgrade_of_the_Deep_Security_Manager_Software_ Recommended_Incompatible_Security_Updates |
Upgrade of the Deep Security Manager Software Recommended (Incompatible Security Update(s)) | Deep Security Manager has detected a computer that is using security updates that are not compatible with the current version of Deep Security Manager. An upgrade of Deep Security Manager software is recommended. |
| alert_Upgrade_of_the_Filter_Driver_Recommended_New_Version_Available | Upgrade of the Filter Driver Recommended (New Version Available) | The filter driver that one or more ESXi servers uses is not the latest available version. An upgrade of the Filter Driver is recommended. |
| alert_User_Locked_Out | User Locked Out | Users can be manually locked out either from repeated sign-in attempts, their password expires, or they have been imported but not yet unlocked. |
| alert_User_Password_Expires_Soon | User Password Expires Soon | The password expiry setting is enabled and one or more users have passwords that will expire within the next 7 days. |
| alert_Virtual_Appliance_is_Incompatible_With_Filter_Driver | Virtual Appliance is Incompatible With Filter Driver | The appliance is incompatible with the filter driver. Ensure both are upgraded to their latest versions. |
| alert_Virtual_Machine_Interfaces_Out_of_Sync | Virtual Machine Interfaces Out of Sync | The interfaces of one or more of the virtual machines that are monitored by a Deep Security virtual appliance are out of sync with the filter driver. The appliance may not be properly monitoring the virtual machine's interfaces. The virtual machine may require manual intervention, such as a configuration change or a restart, to correct the issue. |
| alert_Virtual_Machine_Moved_to_Unprotected_ESXi_Server | Virtual Machine Moved to Unprotected ESXi Server | A virtual machine was moved to an ESXi server that does not have an activated Deep Security virtual appliance. |
| alert_Virtual_Machine_Unprotected_after_move_to_another_ESXi | Virtual Machine Unprotected after move to another ESXi | A virtual machine that was protected by an appliance has been unprotected while or after it was moved to another ESXi. This may be due to an appliance reboot or power off during the move or it may indicate a configuration issue. The cause of the issue should be investigated before the alert is dismissed. |
| alert_VMware_Tools_Not_Installed | VMware Tools Not Installed | A protected virtual machine in an NSX environment does not have VMware Tools installed. VMware Tools is required to protect virtual machines in an NSX environment. |
| alert_Web_Reputation_Event_Alert | Web Reputation Event Alert | A web reputation event has occurred on one or more computers. |