Use deployment scripts to add and protect computers
Adding a computer to your list of protected resources in Deep Security and implementing protection is a multi-step process. Almost all of these steps can be performed from the command line on the computer and can therefore be scripted. The Deep Security Manager contains a deployment script writing assistant which can be accessed from the Support menu.
Enable agent-initiated activation
If your deployment script will automatically activate the Deep Security Agent after it is installed, you must configure Deep Security Manager to allow agent-initiated activation. See the Enable agent-initiated activation section of Activate and protect agents using agent-initiated activation and communication.
Generate a deployment script
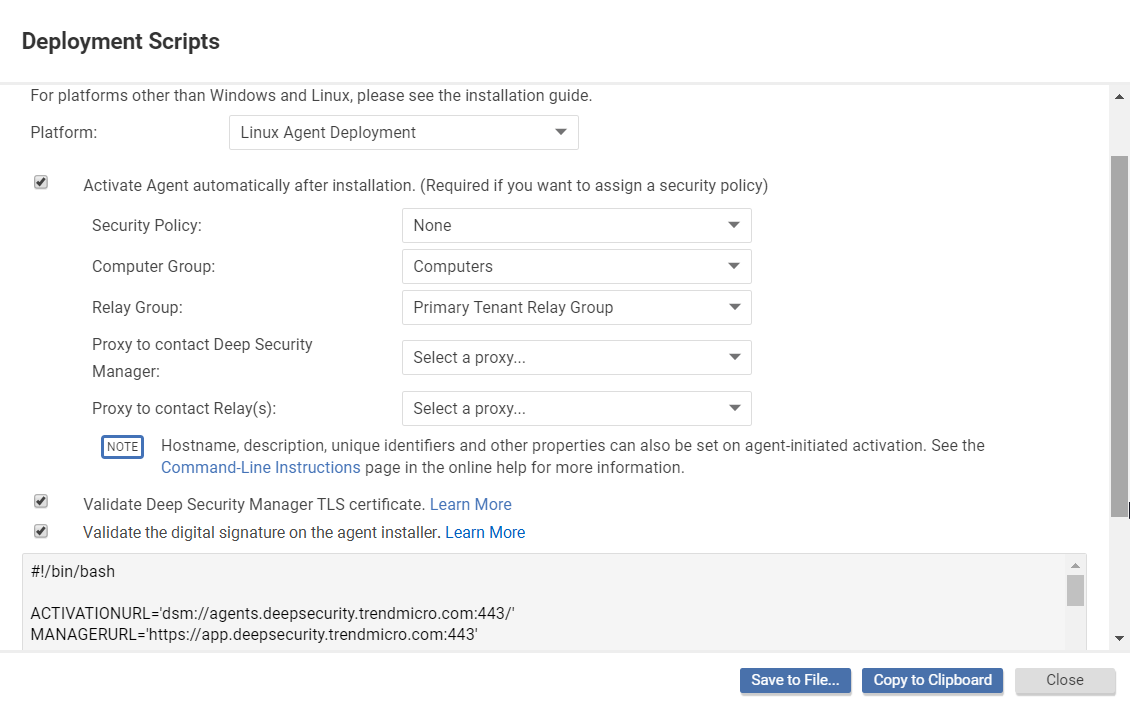
- In the upper right corner of the Deep Security Manager console, click Support > Deployment Scripts.
- Select the platform on which you are deploying the software.
The platforms in the list correspond to the agent software that you have imported into Deep Security Manager. For information on importing Deep Security software, see Get Deep Security Agent software.
- Select Activate agent automatically after installation.
Agents must be activated before you apply a policy to protect the computer. Activation registers the agent with the manager during an initial communication.
- Optionally, select the Security Policy, Computer Group, Relay Group, Proxy to contact Deep Security Manager, and Proxy to contact Relay(s).
- Optionally (but highly recommended), select Validate Deep Security Manager TLS certificate.
When this option is selected, it checks that Deep Security Manager is using a valid TLS certificate from a trusted certificate authority (CA) when downloading the agent software, which can help prevent a "man in the middle" attack. You can check whether Deep Security Manager is using a valid CA certificate by looking at the browser bar in the Deep Security Manager console. By default, Deep Security Manager uses a self-signed certificate, which is not compatible with the Validate Deep Security Manager TLS certificate option. If your Deep Security Manager is not behind a load balancer, see Replace the Deep Security Manager TLS certificate for instructions on replacing the default self-signed certificate with a certificate from a trusted certificate authority. If the manager is behind a load balancer, you will need to replace the load balancer's certificates.
- Optionally (but highly recommended), select Validate the signature on the agent installer to have the deployment script initiate a digital signature check on the agent installer file. If the check is successful, the agent installation proceeds. If the check fails, the agent installation is aborted. Before you enable this option, understand that:
- This option is only supported for Linux and Windows installers (RPM, DEB, or MSI files).
- (Linux only) This option requires that you import the public signing key to each agent computer where the deployment script will run. For details, see Check the signature on an RPM file and Check the signature on a DEB file.
- The deployment script generator displays the script. Click Copy to Clipboard and paste the deployment script in your preferred deployment tool, or click Save to File.
- Linux: Remove the --tls1.2 tag.
- Windows: Remove the #requires -version 4.0 line. Also remove the [Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12; line so that early TLS (version 1.0) is used to communicate with the manager.
If you are using Amazon Web Services and deploying new Amazon EC2, Amazon WorkSpace, or VPC instances, copy the generated script and paste it into the User Data field. This will let you launch existing Amazon Machine Images (AMIs) and automatically install and activate the agent at startup. The new instances must be able to access the URLs specified in the generated deployment script. This means that your Deep Security Manager must be either Internet-facing, connected to AWS via VPN or Direct Link, or that your Deep Security Manager be deployed on Amazon Web Services too.
When copying the deployment script into the User Data field for a Linux deployment, copy the deployment script as-is into the "User Data" field and CloudInit will execute the script with sudo. (If there are failures, they will be noted in /var/log/cloud-init.log.)
https://docs.aws.amazon.com/AWSCloudFormation/latest/UserGuide/aws-properties-waitcondition.html
Troubleshooting and tips
- If you are attempting to run a deployment script and see exit code 2 "TLS certificate validation for the agent package download has failed. Please check that your Deep Security Manager TLS certificate is signed by a trusted root certificate authority. For more information, search for "deployment scripts" in the Deep Security Help Center.", the deployment script was created with the Validate Deep Security Manager TLS certificate checkbox selected. This error appears if Deep Security Manager is using a certificate that is not publicly trusted (such as the default self-signed certificate) for the connection between Deep Security Manager and its agents, or if there is a problem with a third-party certificate, such as a missing certificate in the trust chain between your certificate and the trusted CA. For information on certificates, see Replace the Deep Security Manager TLS certificate. As an alternative to replacing the trusted certificate, you can clear the Validate Deep Security Manager TLS certificate checkbox when generating a deployment script. Note that this is not recommended for security reasons.
- If you are attempting to deploy the agent from PowerShell (x86), you will receive the following error : C:\Program Files (x86)\Trend Micro\Deep Security Agent\dsa_control' is not recognized as the name of a cmdlet, function, script file, or operable program. Check the spelling of the name, or if a path was included, verify that the path is correct and try again.
The PowerShell script expects the environment variable for ProgramFiles to be set to "Program Files", not "Program Files (x86)". To resolve the issue, close PowerShell (x86) and run the script in PowerShell as an administrator.
- On Windows computers, the deployment script will use the same proxy settings as the local operating system. If the local operating system is configured to use a proxy and the Deep Security Manager is accessible only through a direct connection, the deployment script will fail.
- The deployment script can be modified to perform agent updates instead of new installs by changing the rpm -ihv to rpm -U.