Deep Security 11.1 has reached end of support. Use the version selector (above) to see more recent versions of the Help Center.
Back up and restore your database
If you have a database backup, you can restore your Deep Security deployment if there is a catastrophic failure or if you move Deep Security Manager to another computer.
Microsoft SQL Server Database
You can back up databases using a scheduled task.
- Go to Administration > Scheduled Tasks.
- Click New.
- Select New Scheduled Task.
- Give a name to this task and select Backup.
- To perform a one-time-only backup, select Once Only and enter a time (5 minutes from now, for example).
- Select where to store the backup files.
- Finish the wizard.
A complete backup shouldn't take more than a minute or so to complete.
A "date-named" folder will be created in the backup location you specified. To restore this database, shut down the Trend Micro Deep Security Manager service (using the Services Microsoft Management Console), copy the backup folders into the corresponding folders of the install directory and restart Deep Security Manager.
If you are using a SQL Server database, a SQL Server database backup file named [timestamp].dsmbackup will be written to the backup folder specified in the scheduled task. For instructions on how to restore a SQL Server database refer to your SQL Server documentation.
Restore the database only
- Stop the Deep Security Manager service.
- Restore the database.
This must be a database from the same version number of the Deep Security Manager. - Start the Deep Security Manager service.
- Verify contents restored.
- Update all of the computers to ensure they have the proper configuration.
Restore both the Deep Security Manager and the database
- Remove any remnants of the lost or corrupted Deep Security Manager and database.
- Install a fresh Deep Security Manager using a fresh or empty database.
- Stop the Deep Security Manager service.
- Restore the database over the freshly installed one, must be the same database name (Must be a database from the same version number of the Manager).
- Start the Deep Security Manager service.
- Verify contents restored.
- Update all of the computers to ensure they have the proper configuration.
Export objects in XML or CSV format
- Events: Go to one of the Events pages and use the Advanced Search options to filter the event data. For example, you could search for all firewall events for computers in the Computers > Laptops computer group that were logged within the last hour whose reason column contains the word spoofed.
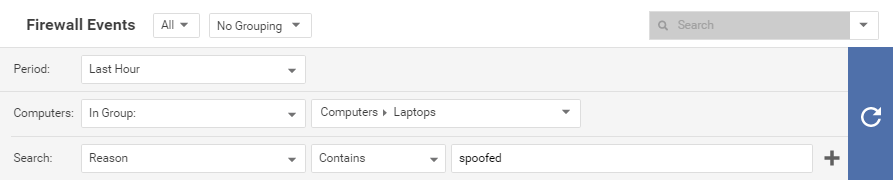
Click the submit button (with the right-facing arrow) to execute the "query". Then clickExport to export the filtered data in CSV format. You can export all the displayed entries or just selected data. The exporting of logs in this format is primarily for integration with third-party reporting tools. - Computer Lists: Computers lists can be exported in XML or CSV format from the Computers page. You might want to do this if you find you are managing too many computers from a single Deep Security Manager and are planning to set up a second Deep Security Manager to manage a collection of computers. Exporting a list of selected computers will save you the trouble of rediscovering all of the computers again and arranging them into groups.
Policy, firewall rule, and intrusion prevention rule settings will not be included. You will have to export your firewall rules, intrusion prevention rules, firewall stateful configurations, and policies as well and then reapply them to your computers.
- Policies: To export these in XML format, go to Policies.
When you export a selected policy to XML, any child policies the policy might have are included in the exported package. The export package contains all of the actual objects associated with the policy except: intrusion prevention rules, log inspection rules, integrity monitoring rules, and application types.
- Firewall Rules: Firewall rules can be exported to an XML or CSV file using the same searching and filtering techniques as above.
- Firewall Stateful Configurations: Firewall stateful configurations can be exported to an XML or CSV file using the same searching and filtering techniques as above.
- Intrusion Prevention Rules: Intrusion prevention rules can be exported to an XML or CSV file using the same searching and filtering techniques as above.
- Integrity Monitoring Rules: Integrity monitoring rules can be exported to an XML or CSV file using the same searching and filtering techniques as above.
- Log Inspection Rules: Log inspection rules can be exported to an XML or CSV file using the same searching and filtering techniques as above.
- Other Common Objects : All the reusable components common objects can be exported to an XML or CSV file the same way.
When exporting to CSV, only displayed column data is included. Use the Columns tool to change which data is displayed. Grouping is ignored so the data might not be in same order as on the screen.
Import objects
To import each of the individual objects into Deep Security, next to New in the object page's toolbar, select Import From File .