Deep Security 10.3 has reached end of support. Use the version selector (above) to see more recent versions of the Help Center.
Policies, inheritance, and overrides
Policies in Deep Security are intended to be created in a hierarchical structure. As an administrator, you begin with one or more base policies from which you create multiple levels of child policies that get progressively more granular in their detail. You can assign broadly applicable rules and other configuration settings at the top-level policies and then get more targeted and specific as you go down through levels of child policies, eventually arriving at rule and configuration assignments at the individual computer level.
As well as assigning more granular settings as you move down through the policy tree, you can also override settings from higher up the policy tree.
Deep Security provides a collection of policies that you can use as initial templates for the design of your own policies tailored to your environment:
In this topic:
Inheritance
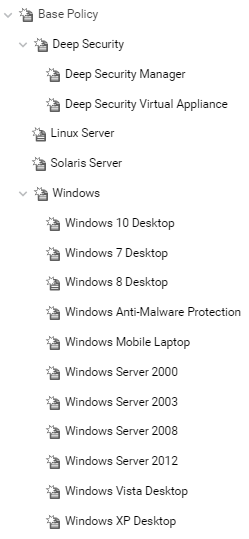
Child policies inherit their settings from their parent policies. This allows you to create a policy tree that begins with a base parent policy configured with settings and rules that will apply to all computers. This parent policy can then have a set of child and further descendant policies which have progressively more specific targeted settings. Your policy trees can be built based on any kind of classification system that suits your environment. For example, the branch in the policy tree that comes with Deep Security has two child policies, one designed for a server hosting the Deep Security Manager and one designed for the Deep Security Virtual Appliance. This is a role-based tree structure. Deep Security also has three branches designed for specific operating systems, Linux, Solaris, and Windows. The windows branch has further child policies for various sub-types of Windows operating systems.
Overrides
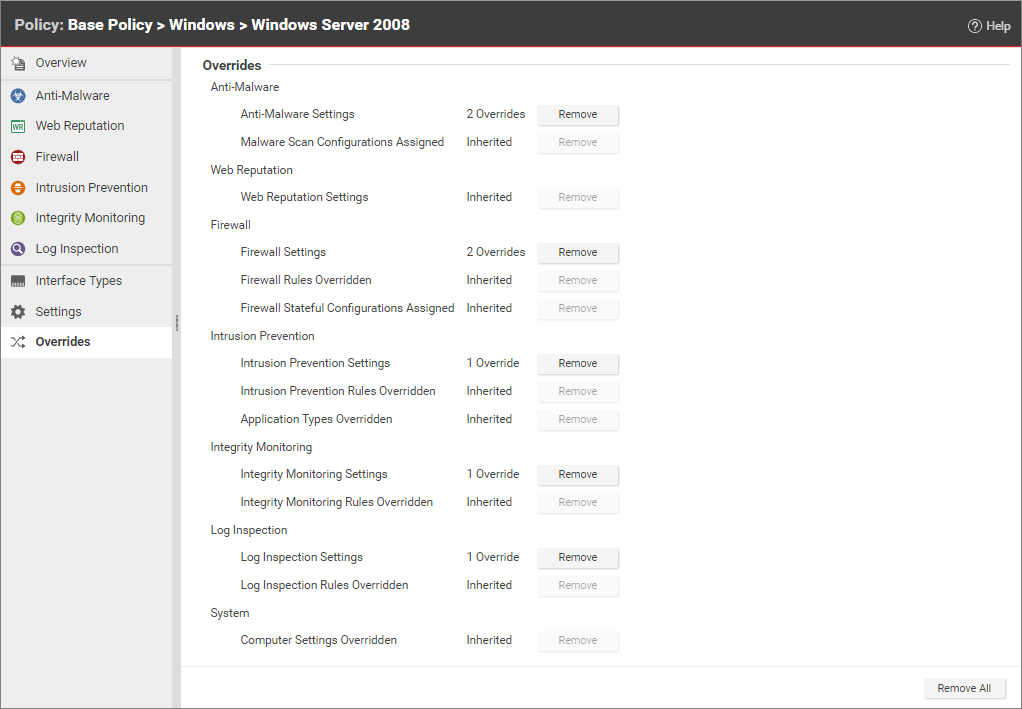
The Overrides page shows you how many settings have been overridden at this policy or specific computer level. To undo the overrides at this level, click the Remove button.
You can see the number of settings that have been overridden on a policy or a computer by going to the Overrides page in the computer or policy Editor: