Deep Security 10.2 has reached end of support. Use the version selector (above) to see more recent versions of the Help Center.
Detect emerging threats using Connected Threat Defense
In the modern data center, more and more security breaches are a result of targeted attacks using techniques such as phishing and spear-phishing. In these cases, malware writers can bypass traditional malware scanners by creating malware specifically targeted for your environment. Deep Security provides enhanced malware protection for new and emerging threats through its Connected Threat Defense feature.
In this article:
- How does Connected Threat Defense work?
- Check the Connected Threat Defense prerequisites
- Set up the connection to Deep Discovery Analyzer
- Set up the connection to Trend Micro Control Manager
- Create a malware scan configuration for use with Connected Threat Defense
- Enable Connected Threat Defense for your computers
- Manually submit a file to Deep Discovery for analysis
- Allow a file that has raised a false alarm
- Configure the scan action for a suspicious file
- Update the suspicious objects list in Deep Security
- Configure Connected Threat Defense in a multi-tenant environment
- Supported file types
For an overview of the anti-malware module, see Protect against malware.
How does Connected Threat Defense work?
- When all of the components are configured properly, the Deep Security Agent uses heuristic detection to analyze files on the protected computer and determines whether they are suspicious.
- Optionally, you can manually or automatically send suspicious files from Deep Security to Deep Discovery Analyzer, which executes and observes the suspicious file in a sandbox (a secure, isolated virtual environment).
- Deep Security Manager gets the sandbox analysis results from Deep Discovery Analyzer.
The sandbox analysis report doesn’t provide protection; it simply provides information on the Deep Discovery analysis. For complete protection, this feature requires a connection to the Trend Micro Control Manager. The report is retrieved from Deep Discovery Analyzer every 15 minutes.
- Deep Discovery Analyzer pushes the analysis results to Trend Micro Control Manager, where an action can be specified for the file based on the analysis. Once the action is specified, a list of emerging threats called a suspicious object list is created or updated. Other Trend Micro products, such as Deep Discovery Inspector or Deep Discovery Email Inspector, may also be connected to Trend Micro Control Manager and able to update the list.
- Optionally, you can configure Deep Security Manager to receive the list of suspicious objects from Trend Micro Control Manager and send the list of suspicious objects to Deep Security Agents.
Check the Connected Threat Defense prerequisites
Before connecting Deep Security to Deep Discovery, check that your environment meets these requirements:
- Deep Security Manager is installed and configured with Deep Security Agents, Deep Security Agents protecting computers, or both.
Optional:
- Deep Discovery Analyzer 5.5 is installed and the sandbox virtual machines are provisioned.
- Trend Micro Control Manager 6.0 SP3 Patch 2 or later is installed.
- Deep Discovery Analyzer has been added to the Trend Micro Control Manager Managed Servers. See the Trend Micro Control Manager documentation for details.
To use Connected Threat Defense with the Deep Security Virtual Appliance, you must be using VMware NSX 6.x.
Set up the connection to Deep Discovery Analyzer
If you want Deep Security Manager to send suspicious files to Deep Discovery Analyzer for analysis, you'll need to set up a connection.
If Control Manager is already managing Deep Security:
- In Deep Security Manager, go to Administration > System Settings > Connected Threat Defense.
- Select Enable submission of suspicious file to Deep Discovery Analyzer.
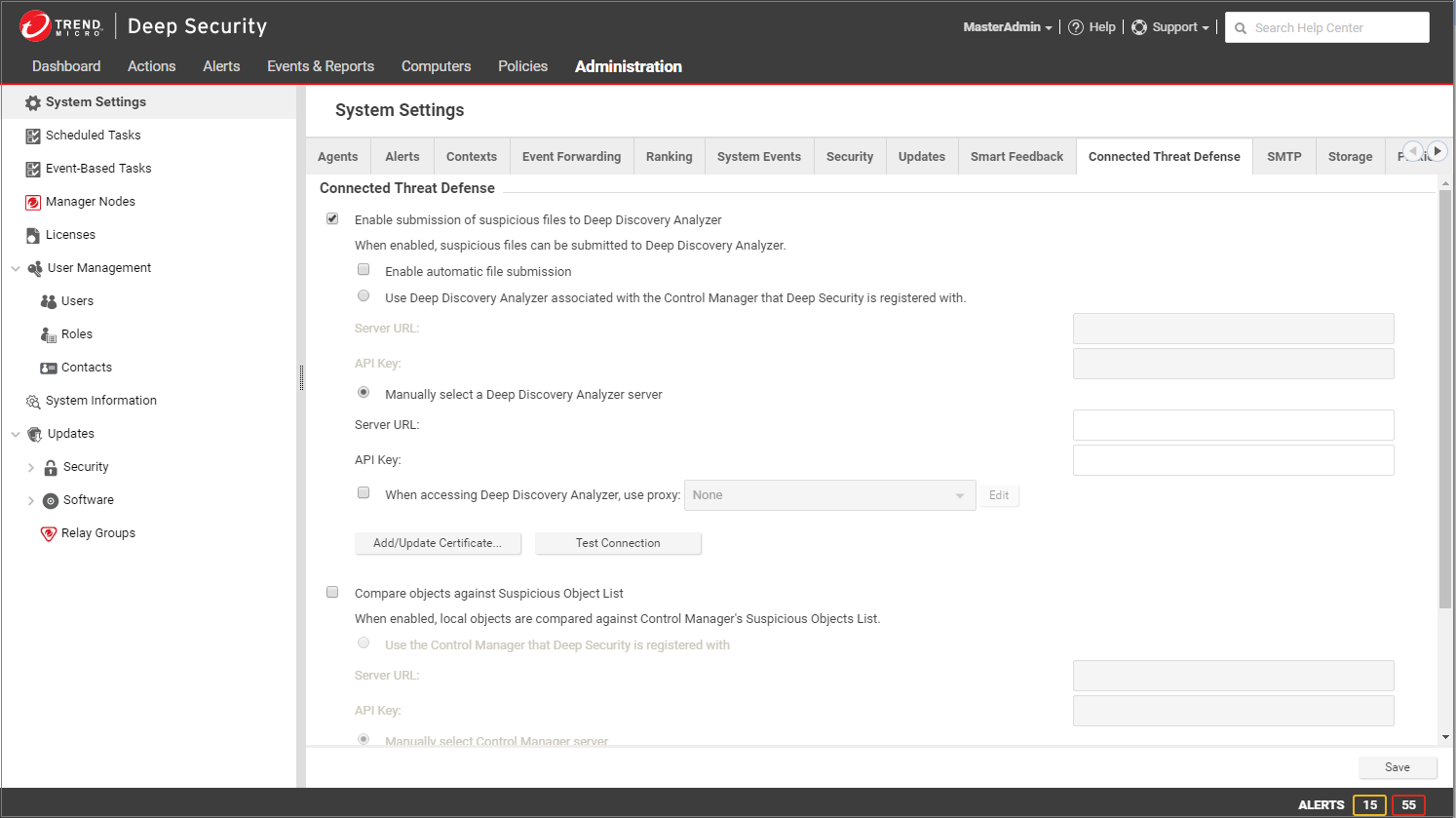
- If you want Deep Security Manager to automatically submit files to Deep Discovery Analyzer, select Enable automatic file submission.
Automatic Submission to Deep Discovery Analyzer occurs every 15 minutes and will submit a maximum of 100 files per submission
- Select Use Deep Discovery Analyzer associated with the Control Manager that Deep Security is registered with.
- Click Test Connection. If you get an error saying that Deep Security is unable to connect due to a missing or invalid certificate, click Add/Update Certificate to update to the correct Deep Discovery Analyzer certificate.
- Click Save.
If Control Manager is not yet managing Deep Security:
- In Deep Discovery Analyzer, go to Help > About and note the Service URL and API key. You will need these values later, so copy them into a text file temporarily.
- In Deep Security Manager, go to Administration > System Settings > Connected Threat Defense.
- Select Enable submission of suspicious file to Deep Discovery Analyzer.

- If you want Deep Security Manager to automatically submit files to Deep Discovery Analyzer, select Enable automatic file submission.
Automatic Submission to Deep Discovery Analyzer occurs every 15 minutes and will submit a maximum of 100 files per submission
- Select Manually select a Deep Discovery Analyzer server, and enter the Server URL and API key that you found in step 1.
- Click Test Connection. If you get an error saying that Deep Security is unable to connect due to a missing or invalid certificate, click Add/Update Certificate to update to the correct Deep Discovery Analyzer certificate.
- Click Save.
Set up the connection to Trend Micro Control Manager
When you configure these settings, Deep Security Manager will be able to retrieve the suspected object list from Trend Micro Control Manager, share it with protected computers, and compare local objects against the Control Manager's Suspicious Object List.
If Control Manager is already managing Deep Security:
- In Deep Security Manager, go to Administration > System Settings > Connected Threat Defense.
- Select Compare objects against Suspicious Object List.
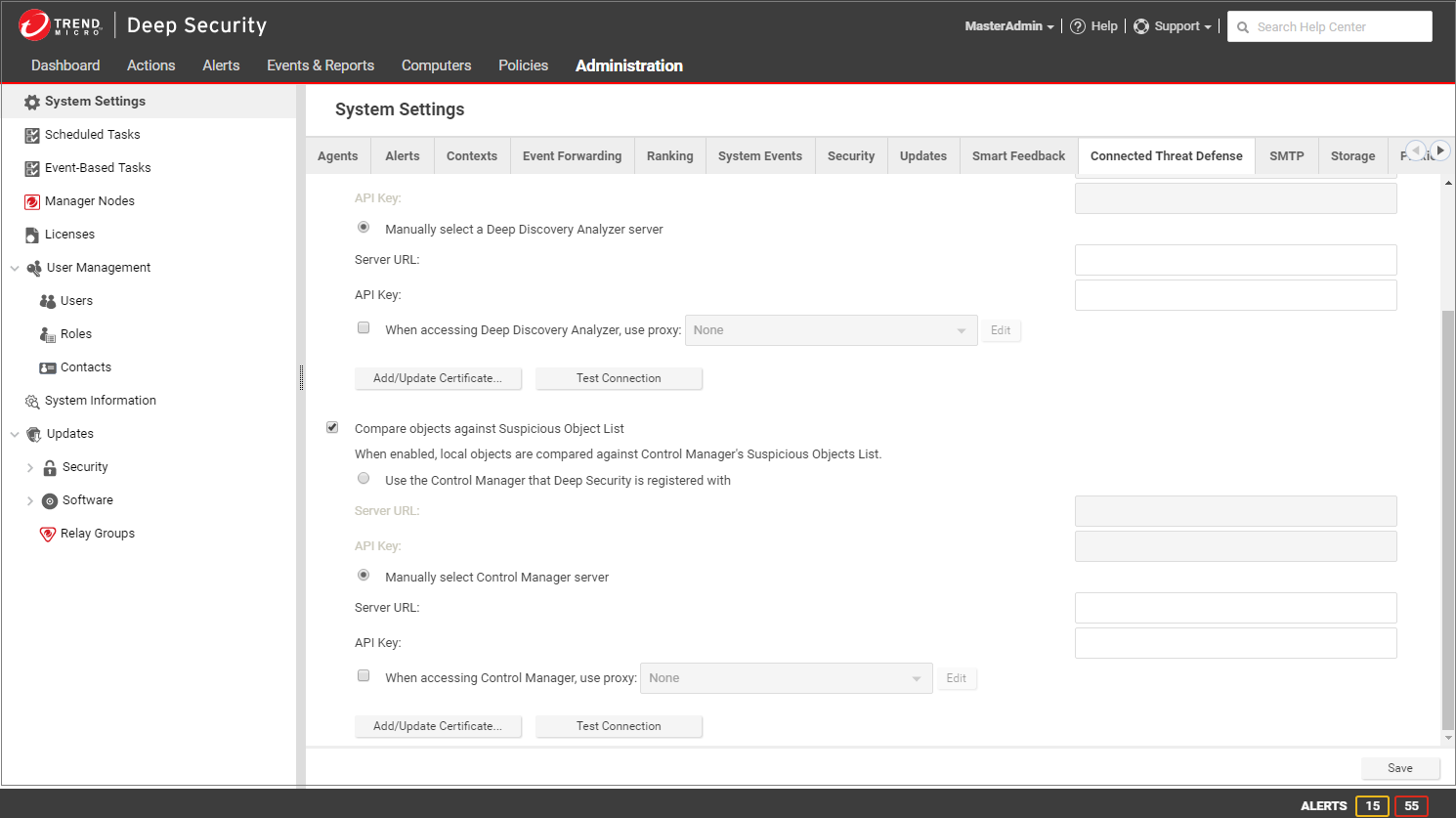
- If Trend Micro Control Manager is already managing Deep Security, select Use the Control Manager that Deep Security is registered with.
- Click Test Connection. If you get an error saying that Deep Security is unable to connect due to a missing or invalid certificate, click Add/Update Certificate to update to the correct Trend Micro Control Manager certificate.
- Click Save.
If Control Manager is not yet managing Deep Security:
- In Trend Micro Control Manager, go to Administration > Suspicious Objects > Distribution Settings. Note the Service URL and API key. You will need these values later, so copy them into a text file temporarily.
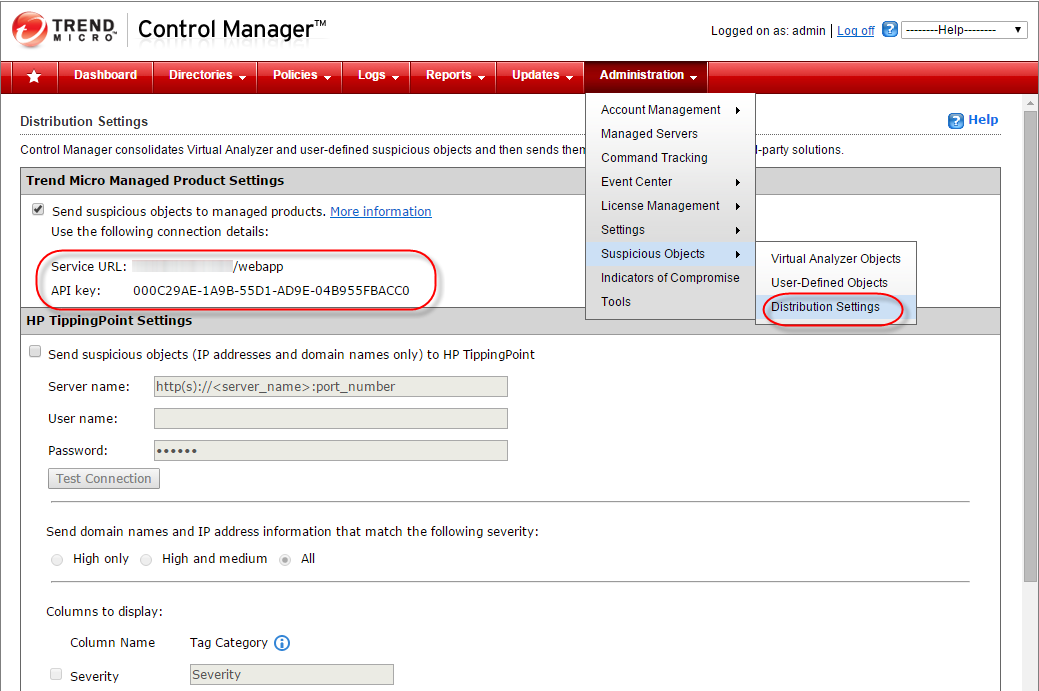
- In Deep Security Manager, go to Administration > System Settings > Connected Threat Defense.
- Select Compare objects against Suspicious Object List.
- Select Manually select a Control Manager server and enter the Server URL and API key that you found in step 1.
- Click Test Connection. If you get an error saying that Deep Security is unable to connect due to a missing or invalid certificate, click Add/Update Certificate to update to the correct Trend Micro Control Manager certificate.
- Click Save.
Create a malware scan configuration for use with Connected Threat Defense
The following configuration allows Deep Security to detect suspicious files, back up the suspicious files, and automatically send them to Deep Discovery Analyzer for further analysis.
- In Deep Security Manager, go to Policies > Common Objects > Other > Malware Scan Configurations.
- Create a new scan configuration or edit an existing configuration.
- On the General tab, under Document Exploit Protection, select Scan documents for exploits and select one of these options:
- Scan for exploits against known critical vulnerabilities only: Only detects known critical vulnerabilities. The CVE Exploit vulnerability type is associated with this option (See Customize malware remedial actions.)
- Scan for exploits against known critical vulnerabilities and aggressive detection of unknown suspicious exploits: Detects more issues but may also result in more false positives. If you want to detect suspicious files and submit them to Deep Discovery Analyzer, you must select this option. The Aggressive Detection Rule vulnerability type is associated with this option. (See Customize malware remedial actions.)
- Configure the other malware scan settings as described in Configure malware scans.
Enable Connected Threat Defense for your computers
You can enable Connected Threat Defense in policies or for individual computers.
- In the Computer or Policy editor
 You can change these settings for a policy or for a specific computer.
To change the settings for a policy, go to the Polices page and double-click the policy that you want to edit (or select the policy and click Details).
To change the settings for a computer, go to the Computers page and double-click the computer that you want to edit (or select the computer and click Details)., go to Anti-Malware > General.
You can change these settings for a policy or for a specific computer.
To change the settings for a policy, go to the Polices page and double-click the policy that you want to edit (or select the policy and click Details).
To change the settings for a computer, go to the Computers page and double-click the computer that you want to edit (or select the computer and click Details)., go to Anti-Malware > General. - Ensure that the Anti-Malware State is On or Inherited (On).
- The General tab contains sections for Real-Time Scan, Manual Scan, and Scheduled Scan. (For information on the different types of scans, see Enable and configure anti-malware.) In the appropriate sections, use the Malware Scan Configuration list to select the scan configuration that you created above.
- Go to the Connected Threat Defense tab and adjust these settings as required:
- If you want Deep Security to send suspicious files to Deep Discovery Analyzer, set the option under Sandbox Analysis to Yes or Inherited (Yes).
- If you have set up a connection between Deep Security and Trend Micro Control Manager and you want to use the suspicious object list from the Control Manager to detect malicious files, set Use Control Manager’s Suspicious Object List (under Suspicious Objects List) to Yes or Inherited (Yes).
- Click Save.
Manually submit a file to Deep Discovery for analysis
You can manually submit files that appear on the Events & Reports > Events > Anti-Malware Events > Identified Files page.
- Select the file that you want to submit and click the Analyze button.
- Follow the steps in the wizard that appears.
- After the file is submitted, you can check the progress of its analysis in the Submission Status column on the Identified Files page.
- When the analysis is finished, the Submission Status column will display "Results Ready". You can click the Results Ready link to see details.
Allow a file that has raised a false alarm
If a file is identified as malware on the Events & Reports > Events > Anti-Malware Events > Identified Files page but you know it's not malware, you can add it to the Document Exploit Protection Rule Exceptions list on the Anti-Malware > Advanced tab of the Computer or Policy editor![]() You can change these settings for a policy or for a specific computer.
To change the settings for a policy, go to the Polices page and double-click the policy that you want to edit (or select the policy and click Details).
To change the settings for a computer, go to the Computers page and double-click the computer that you want to edit (or select the computer and click Details)..
You can change these settings for a policy or for a specific computer.
To change the settings for a policy, go to the Polices page and double-click the policy that you want to edit (or select the policy and click Details).
To change the settings for a computer, go to the Computers page and double-click the computer that you want to edit (or select the computer and click Details)..
To allow the file, right-click it, click Allow, and follow the steps in the wizard that appears.
Configure the scan action for a suspicious file
You can view the suspicious objects list in the Trend Micro Control Manager console and configure the action (log, block, or quarantine) that should be taken when a suspicious object is found. (See Suspicious Object Management and Handling Process for details on configuring the actions.) If you have configured Deep Security Manager to obtain the suspicious object list from Control Manager, Deep Security will perform the specified action when it finds the suspected object.
Deep Security supports file suspicious objects. It also supports URL suspicious objects if the web reputation protection module is configured to use the Trend Micro Smart Protection Server. Deep Security does not support IP and domain suspicious objects.
Trend Micro Control Manager 6.0 SP3 User-Defined Objects do not work with Deep Security. Virtual Analyzer objects for files do work with Deep Security.
Update the suspicious objects list in Deep Security
After the analysis of a suspicious object has been completed and the action for the file has been set in Trend Micro Control Manager, Deep Security can use the Suspicious Object list from Trend Micro Control Manager to protect your computers. To manually update the suspicious file list in Deep Security Manager, go to Administration > Updates > Security and use the controls in the Suspicious Object List Updates column to get the latest list and send it to your protected computers. You can also create a scheduled task that regularly checks for an updated list (see Schedule Deep Security to perform tasks).
In Trend Micro Control Manager, the default suspicious object setting is "Log". You may want to consider changing the default setting to "Quarantine" or "Block".
Once the suspicious object list has been updated in Deep Security and the computer policies have been updated with the action specified, the Deep Security Agent will then check the affected computers and use this action any time this file is encountered again on a protected computer.
Configure Connected Threat Defense in a multi-tenant environment
In a multi-tenant environment, the primary tenant (t0) can choose whether to share their Deep Discovery Analyzer and Trend Micro Control Manager settings with their tenants. The setting that controls this behavior is Administration > System Settings > Tenants > Allow Tenants to use Primary Tenant's Trend Micro Control Manager and Deep Discovery Analyzer Server settings:
- When the setting is enabled and a tenant goes to Administration > System Settings > Connected Threat Defense, they will see an additional Use default server settings checkbox. When this checkbox is selected, the tenant will use the primary tenant's settings. When Use default server settingsis not selected, the tenant can configure their own Connected Threat Defense settings.
- When the setting is not enabled, tenants must use their own Trend Micro Control Manager and Deep Discovery Analyzer if they want to use Connected Threat Defense.
Supported file types
Deep Security can send these file types to Deep Discovery Analyzer:
- doc - Microsoft Word document
- docx - Microsoft Office Word 2007 document
- gul - JungUm Global document
- hwp - Hancom Hangul Word Processor (HWP) document
- hwpx - Hancom Hangul Word Processor 2014 (HWPX) document
- jar - Java Applet Java application
- js - JavaScript file
- jse - JavaScript encoded script file
- jtd - JustSystems Ichitaro document
- lnk - Microsoft Windows Shell Binary Link shortcut
- mov - Apple QuickTime media
- pdf - Adobe Portable Document Format (PDF)
- ppt - Microsoft Powerpoint presentation
- pptx - Microsoft Office PowerPoint 2007 Presentation
- ps1 - Microsoft Windows PowerShell script file
- rtf - Microsoft Rich Text Format (RTF) document
- swf - Adobe Shockwave Flash file
- vbe - Visual Basic encoded script file
- vbs - Visual Basic script file
- xls - Microsoft Excel spreadsheet
- xlsx - Microsoft Office Excel 2007 Spreadsheet
- xml - Microsoft Office 2003 XML file