Deep Security 10.2 has reached end of support. Use the version selector (above) to see more recent versions of the Help Center.
Event collection in Deep Security
Deep Security Agents record when a protection module rule or condition is triggered (a "security event"). Agents and Deep Security Manager also record when administrative or system-related events occur (a "system event"), such as an administrator logging in, or agent software being upgraded. Event data is used to populate the various reports and graphs in Deep Security Manager.
To view events, go to Events & Reports tab in Deep Security Manager.
Where are event logs on the agent?
Location varies by the computer's operating system. On Windows, event logs are stored in this location:
C:\Program Data\Trend Micro\Deep Security Agent\Diag
On Linux, event logs are stored here:
/var/opt/ds_agent/diag
When are events sent to the manager?
Most events that take place on a computer are sent to the Deep Security Manager during the next heartbeat operation except the following, which will be sent right away if communication settings allow relays/agents/appliances to initiate communication:
- Smart Scan Server is offline
- Smart Scan Server is back online
- Integrity Monitoring scan is complete
- Integrity Monitoring baseline created
- Unrecognized elements in an Integrity Monitoring Rule
- Elements of an Integrity Monitoring Rule are unsupported on the local platform
- Abnormal restart detected
- Low disk space warning
- Log Inspection offline
- Log Inspection back online
- Reconnaissance scan detected (if the setting is enabled in Computer or Policy editor
 You can change these settings for a policy or for a specific computer.
To change the settings for a policy, go to the Polices page and double-click the policy that you want to edit (or select the policy and click Details).
To change the settings for a computer, go to the Computers page and double-click the computer that you want to edit (or select the computer and click Details). > Firewall > Reconnaissance
You can change these settings for a policy or for a specific computer.
To change the settings for a policy, go to the Polices page and double-click the policy that you want to edit (or select the policy and click Details).
To change the settings for a computer, go to the Computers page and double-click the computer that you want to edit (or select the computer and click Details). > Firewall > Reconnaissance
How long are events stored?
Once collected by the Deep Security Manager, events are kept for a period of time, which is specified on the Administration > System Settings > Storage page. For details, see Log and event storage best practices.
System events
All the Deep Security system events are listed and can be configured on the Administration > System Settings > System Events tab. You can set whether to record the individual events and whether to forward them to a SIEM system. For details on system events, see System events.
Security events
Each protection module generates events when rules are triggered or other configuration conditions are met. Some of this security event generation is configurable. For information on specific types of security events, refer to these articles:
- Anti-malware events
- View and restore identified malware
- Firewall events
- Integrity monitoring events
- Intrusion prevention events
- Log inspection events
- Web reputation events
The firewall stateful configuration in effect on a computer can be modified to enable or disable TCP, UDP, and ICMP event logging. To edit the properties of a stateful firewall configuration, go to Policies > Common Objects > Other > Firewall Stateful Configurations. The logging options are in the TCP, UDP, and ICMP tabs of the firewall stateful configuration's Properties window. For more information about firewall events, see Firewall events.
See the events associated with a policy or computer
The Policy editor![]() To open the Policy editor, go to the Policies page and double-click the policy that you want to edit (or select the policy and click Details). and theComputer editor
To open the Policy editor, go to the Policies page and double-click the policy that you want to edit (or select the policy and click Details). and theComputer editor ![]() To open the Computer editor, go to the Computers page and double-click the computer that you want to edit (or select the computer and click Details).both have Events tabs for each protection module. The policy editor displays events associated with the current policy. The computer editor displays events specific to the current computer.
To open the Computer editor, go to the Computers page and double-click the computer that you want to edit (or select the computer and click Details).both have Events tabs for each protection module. The policy editor displays events associated with the current policy. The computer editor displays events specific to the current computer.
View details about an event
To see details about an event, double-click it.
The General tab displays:
- Time: The time according to the system clock on the computer hosting the Deep Security Manager.
- Level: The severity level of event that occurred. Event levels include Info, Warning, and Error.
- Event ID: The event type's unique identifier.
- Event: The name of the event (associated with the event ID.)
- Target: The system object associated with the event will be identified here. Clicking the object's identification will display the object's properties sheet.
- Event Origin: The Deep Security component from which the event originated.
- Action Performed By: If the event was initiated by a user, that user's username will be displayed here. Clicking the username will display the User Properties window.
- Manager: The hostname of the Deep Security Manager computer.
- Description: If appropriate, the specific details of what action was performed to trigger this event are displayed here.
The Tags tab displays tags that have been attached to this event. For more information on event tagging, see Policies > Common Objects > Other > Tags, and Apply tags to identify and group events.
Filter the list to search for an event
The Period toolbar lets you filter the list to display only those events that occurred within a specific timeframe.
The Computers toolbar lets you organize the display of event log entries by computer groups or computer policies.
Clicking Search > Open Advanced Search toggles the display of the advanced search bar.
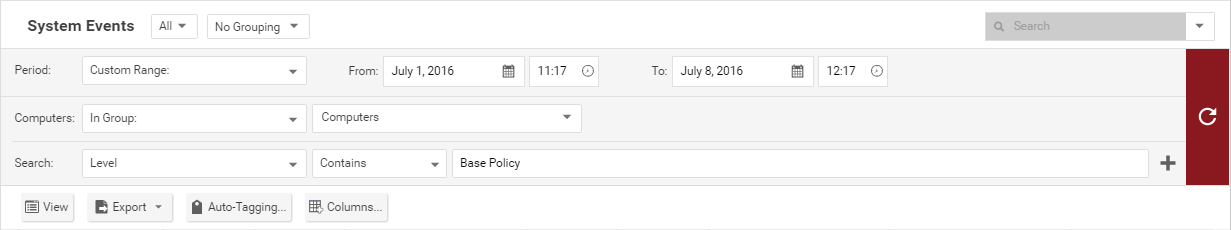
Clicking the "Add Search Bar" button (+) to the right of the search bar will display an additional search bar so you can apply multiple parameters to your search. When you are ready, press the "Submit Request" button (at the right of the toolbars with the right-arrow on it).
Export events
You can export displayed events to a CSV file. (Paging is ignored, all pages will be exported.) You have the option of exporting the displayed list or the selected items.
Improve logging performance
Here are some suggestions to help maximize the performance of event collection:
- Reduce or disable log collection for computers that are not of interest.
- Consider reducing the logging of firewall rule activity by disabling some logging options in the firewall stateful configuration Properties window. For example, disabling the UDP logging will eliminate the "Unsolicited UDP" log entries.