Deep Security 10.2 has reached end of support. Use the version selector (above) to see more recent versions of the Help Center.
Computer and agent statuses
On the Computers page in Deep Security Manager:
- The Status column displays the state of the computer's network connectivity and the state (in parentheses) of the agent providing protection, if present. The status column might also display system or agent events. See Status column - computer statesand Status column - agent or appliance states
- The Task(s) column displays the state of the tasks. See Task(s) column.
For a list of the events, see Agent events and System events.
Also on this page:
- Computer errors
- Protection module status
- Perform other actions on your computers
- Computers icons
- Status information for different types of computers
Status column - computer states
| State | Description |
| Activated | The agent is activated. See Perform other actions on your computers. |
| Discovered | Computer has been added to the computers list via the discovery process. (See Discover computers.) |
| Managed | An agent is present and activated, with no pending operations or errors. |
| Multiple Errors | Multiple errors have occurred on this computer. See the computer's system events for details. |
| Multiple Warnings | Multiple warnings are in effect on this computer. See the computer's system events for details. |
| Reactivation Required | The agent is installed and listening and is waiting to be reactivated a Deep Security Manager. |
| Unmanaged | The computer's agent is not managed by this Deep Security Manager because it hasn't been activated. Deep Security Manager can't communicate with the agent until you activate it. |
| Upgrade Recommended | A newer version of the agent or appliance is available. An software upgrade is recommended. |
| Upgrading Agent | The agent software on this computer is in the process of being upgraded to a newer version. |
Status column - agent or appliance states
| State | Description |
| Activated | The agent has been successfully activated and is ready to be managed by the Deep Security Manager. |
| Activation Required | An unactivated agent has been detected on the target machine. It must be activated before it can be managed by the Deep Security Manager. |
| Deactivation Required | The manager has attempted to activate an agent that has already been activated by another Deep Security Manager. The original Deep Security Manager must deactivate the agent before it can be activated by the new manager. |
| No Agent | No agent was detected on the computer. |
| Offline |
The agent has not connected to the manager for the number of heartbeats specified on Computer or Policy editor This can occur when connectivity is interrupted by a network firewall or proxy, AWS security group, agent software update, or when a computer is powered down for repair. Verify that firewall settings allow the required port numbers, and that the computer is powered on. If you use Deep Security as a Servicee, also see Use agent-initiated communication with cloud accounts. |
| Online | The agent is online and operating as expected. |
| Unknown | No attempt has been made to determine whether an agent is present. |
Task(s) column
| State | Description |
| Activating | The manager is activating the agent. |
| Activating (Delayed) | The activation of the agent is delayed by the amount of time specified in the relevant event-based task. |
| Activation Pending | A command to activate the agent has been queued. |
| Agent Software Deployment Pending | An instruction to deploy the agent software is queued to be sent to the computer. |
| Agent Software Removal Pending | An instruction to remove the agent software is queued to be sent to the computer. |
| Application Control Inventory Scan In Progress | An application control inventory scan is being performed. |
| Application Control Inventory Scan Pending (Heatbeat) | An instruction to start an application control inventory scan will be sent from the manager during the next heartbeat. |
| Application Control Inventory Scan Pending (Offline) | The agent is currently offline. The manager will initiate an application control inventory scan when communication is reestablished. |
| Application Control Ruleset Update In Progress | The application control ruleset is being updated. |
| Application Control Ruleset Update Pending (Heartbeat) | An instruction to perform an application control ruleset update will be sent from the manager during the next heartbeat. |
| Application Control Ruleset Update Pending (Offline) | The agent is currently offline. The manager will initiate an application control ruleset update when communication is reestablished. |
| Baseline Rebuild In Progress | The Integrity Monitoring engine is currently rebuilding a system baseline. |
| Baseline Rebuild Paused | A baseline rebuild has been paused |
| Baseline Rebuild Pending | An instruction to rebuild a system baseline for Integrity Monitoring is queued to be sent. |
| Baseline Rebuild Pending (Offline) | The agent is currently offline. The Integrity Monitoring engine will rebuild a system baseline when communication between the manager and this computer is reestablished. |
| Baseline Rebuild Queued | The instruction to perform a baseline rebuild is queued. |
| Checking Status | The agent state is being checked. |
| Deactivate Pending (Heartbeat) | A deactivate instruction will be sent from the manager during the next heartbeat. |
| Deactivating | The manager is deactivating the agent. This means that the agent is available for activation and management by another Deep Security Manager. |
| Deploying Agent Software | Agent software is being deployed on the computer. |
| File Backup Cancellation In Progress | A file backup is being canceled. |
| File Backup Cancellation Pending | An instruction to cancel a file backup is queued to be sent. |
| File Backup Cancellation Pending (Offline) | The agent or appliance is currently offline. The manager will initiate the cancellation of the file backup when communication is reestablished. |
| File Backup In Progress | A file backup is being performed. |
| File Backup Pending | An instruction to start a file backup is queued to be sent. |
| File Backup Pending (Offline) | The agent or appliance is currently offline. The manager will initiate a file backup when communication is reestablished. |
| File Backup Queued | The instruction to perform a file backup is queued. |
| Getting Events | The manager is retrieving events from the agent. |
| Integrity Scan In Progress | An Integrity Scan is currently in progress. |
| Integrity Scan Paused | An integrity scan has been paused. |
| Integrity Scan Pending | A command to start an integrity scan is queued to be sent. |
| Integrity Scan Pending (Offline) | The agent is currently offline. The manager will initiate an Integrity Scan when communication is reestablished. |
| Integrity Scan Queued | An instruction to start an integrity scan is queued to be sent. |
| Malware Manual Scan Cancellation In Progress | The instruction to cancel a manually-initiated Malware Scan has been sent. |
| Malware Manual Scan Cancellation Pending | The command to cancel a manually-initiated malware scan is queued to be sent. |
| Malware Manual Scan Cancellation Pending (Offline) | The appliance is offline. The instruction to cancel a manually-initiated Malware Scan will be sent when communication is reestablished. |
| Malware Manual Scan In Progress | A manually-initiated Malware Scan is in progress. |
| Malware Manual Scan Paused | A manually-initiated Malware Scan has been paused. |
| Malware Manual Scan Pending | The instruction to perform a manually-initiated Malware Scan has not yet been sent. |
| Malware Manual Scan Pending (Offline) | The agent is offline. The instruction to start a manually-initiated Malware Scan will be sent when communication is reestablished. |
| Malware Manual Scan Queued | The instruction to perform a manually-initiated Malware Scan is queued. |
| Malware Scheduled Scan Cancellation In Progress | The instruction to cancel a scheduled Malware Scan has been sent. |
| Malware Scheduled Scan Cancellation Pending | The instruction to cancel a scheduled Malware Scan is queued to be sent. |
| Malware Scheduled Scan Cancellation Pending (Offline) | The agent is offline. The instruction to cancel a scheduled Malware Scan will be sent when communication is reestablished. |
| Malware Scheduled Scan In Progress | A scheduled Malware Scan is in progress. |
| Malware Scheduled Scan Paused | A scheduled Malware Scan has been paused. |
| Malware Scheduled Scan Pending | The command to cancel a scheduled malware scan has not yet been sent. |
| Malware Scheduled Scan Pending (Offline) | The agent is offline. The instruction to start a scheduled Malware Scan will be sent when communication is reestablished. |
| Malware Scheduled Scan Queued | The instruction to cancel a scheduled Malware Scan is queued. |
| Quick Malware Scan Cancellation In Progress | A quick malware scan is being canceled. |
| Quick Malware Scan Cancellation Pending | An instruction to cancel a quick malware scan is queued to be sent. |
| Quick Malware Scan Cancellation Pending (Offline) | The agent is currently offline. The manager will initiate the cancellation of a quick malware scan when communication is reestablished. |
| Quick Malware Scan In Progress | A quick malware scan is being performed. |
| Quick Malware Scan Paused | A quick malware scan has been paused. |
| Quick Malware Scan Pending | An instruction to start a quick malware scan is queued to be sent. |
| Quick Malware Scan Pending (Offline) | The agent is currently offline. The manager will initiate a quick malware scan when communication is reestablished. |
| Quick Malware Scan Queued | The instruction to perform a quick malware scan is queued. |
| Removing Agent Software | The agent software is being removed from the computer. |
| Rollback of Security Update In Progress | A security update is being rolled back. |
| Rollback of Security Update Pending | An instruction to roll back a security update is queued to be sent. |
| Rollback of Security Update Pending (Heartbeat) | An instruction to roll back a security update will be sent from the manager during the next heartbeat. |
| Rollback of Security Update Pending (Offline) | The agent is currently offline. The manager will initiate a rollback of the security update when communication is reestablished. |
| Scan for Recommendations Pending (Heartbeat) | The manager will initiate a recommendation scan at the next heartbeat. |
| Scan for Recommendations Pending (Offline) | The agent is currently offline. The manager will initiate a recommendation scan when communication is reestablished. |
| Scanning for Open Ports | The manager is scanning the computer for open ports. |
| Scanning for Recommendations | A recommendation scan is underway. |
| Security Update In Progress | A security update is being performed. |
| Security Update Pending | An instruction to perform a security update is queued to be sent. |
| Security Update Pending (Heartbeat) | An instruction to perform a security update will be sent from the manager during the next heartbeat. |
| Security Update Pending (Offline) | The agent is currently offline. The manager will initiate a security update when communication is reestablished. |
| Sending Policy | A policy is being sent to the computer. |
| Update of Configuration Pending (Heartbeat) | An instruction to update the configuration to match the policy changes will be sent from the manager during the next heartbeat. |
| Update of Configuration Pending (Offline) | The agent is currently offline. The manager will initiate the configuration update to match the policy changes when communication is reestablished. |
| Upgrading Software (In Progress) | A software upgrade is being performed. |
| Upgrading Software (Install Program Sent) | A software upgrade is being performed. The install program has been sent to the computer. |
| Upgrading Software (Pending) | An instruction to perform a software upgrade is queued to be sent. |
| Upgrading Software (Results Received) | A software upgrade is being performed. The results have been received. |
| Upgrading Software (Schedule) | A software upgrade will be performed once the computer's access schedule permits. |
Computer errors
| State | Description |
| Communication error | General network error. |
| No route to computer | Typically the remote host cannot be reached because of an intervening firewall or if an intermediate router is down. |
| Unable to resolve hostname | Unresolved socket address. |
| Activation required | An instruction was sent to the agent when it was not yet activated. |
| Unable to communicate with Agent | Unable to communicate with agent. |
| Protocol Error |
Communication failure at the IP, TCP, or HTTP layer. For example, if the Deep Security Manager IP address is unreachable because the connection is being blocked by a firewall, router, or AWS security group, then it would cause a connection to fail. To resolve the error, verify that the activation port number is allowed and that a route exists. |
| Deactivation Required | The agent is currently activated by another Deep Security Manager. |
| No Agent | No agent was detected on the target. |
| No valid software version | Indicates that no installer can be found for the platform and version requested. |
| Send software failed | There was an error in sending a binary package to the computer. |
| Internal error | Internal error. Please contact your support provider. |
| Duplicate Computer | Two computers in the Deep Security Manager's computers list share the same IP address. |
| Unresolved software change limit reached |
Software changes detected on the file system exceeded the maximum amount. Application control will continue to enforce existing rules, but will not record any more changes, and it will stop displaying any of that computer's software changes. |
Protection module status
When you hover over a computer name on the Computers page, the Preview icon (![]() ) is displayed. Click the icon to display the state of the computer's protection modules.
) is displayed. Click the icon to display the state of the computer's protection modules.
On and Off States:
| State | Description |
| On | Module is configured in Deep Security Manager and is installed and operating on the Deep Security Agent. |
| Off | Module is either not configured in Deep Security Manager, not installed and operating on the Deep Security Agent, or both. |
| Unknown | Indicates an error with the protection modules. |
Install state:
| State | Description |
| Not Installed | The software package containing the module has been downloaded in Deep Security Manager, but the module has not been turned on in Deep Security Manager or installed on the agent. |
| Installation Pending | Module is configured in the manager but is not installed on the agent. |
| Installation in Progress | Module is being installed on the agent. |
| Installed | Module is installed on the agent. This state is only displayed when the state of the module is "Off". (If the state is "On", the module has been installed on the agent.) |
| Matching Module Plug-In Not Found | The version of the software package containing the module imported into the manager does not match the version reported by the agent. |
| Not Supported/Update Not Supported | A matching software package was found on the agent, but it does not contain a module supported by the platform. "Not Supported" or "Update Not Supported" is displayed depending on whether there is already a version of this module installed on the agent. |
Perform other actions on your computers
On the Computers page, the Actions button provides several actions that you can perform on the selected computers.
| Action | Description |
|---|---|
| Check Status | Checks the status of a computer without performing a scan or activation attempt. |
| Activate/Reactivate | Activates or reactivates the agent on the computer. See Activate the agent |
| Deactivate | You may want to transfer control of a computer from one Deep Security Manager installation to another. If so, the agent has to be deactivated and then activated again by the new manager. |
| Assign Policy |
Opens a window with a list that allows you to assign a policy to the computer. The name of the policy assigned to the computer will appear in the Policy column on the Computers page. If you apply other settings to a computer (for example, adding additional Firewall Rules, or modifying Firewall Stateful Configuration settings), the name of the policy will be in bold, indicating that the default settings have been changed.
|
| Send Policy |
When you use Deep Security Manager to change the configuration of an agent or appliance on a computer (apply a new intrusion prevention rule, change logging settings, etc.), the Deep Security Manager has to send the new information to the agent or appliance. This is a Send Policy instruction. Policy updates usually happen immediately but you can force an update by clicking Send Policy. |
| Download Security Update | Downloads the latest security update from the configured relay to the agent or appliance. See Get and distribute security updates. |
| Rollback Security Update | Rolls back the latest security update for the agent or appliance. |
| Get Events | Override the normal event retrieval schedule (usually every heartbeat) and retrieve the event logs from the computer(s) now. |
| Clear Warnings/Errors |
Use this command to clear all warnings and errors for the computer. This command is useful in these situations:
|
| Upgrade Agent Software |
To upgrade an agent, you first need to import a newer version of the agent software package into the Deep Security Manager (see Update Deep Security software). |
| Scan for Recommendations |
Deep Security Manager can scan computers and then make recommendations for Security Rules. The results of a recommendation scan appear in the computer's Details window in the Rules pages. See Manage and run recommendation scans. |
| Clear Recommendations |
Clears rule recommendations resulting from a recommendation scan on this computer. Clearing also removes the computer from those listed in an alert produced as a result of a recommendation scan. This action will not un-assign any rules that were assigned because of past recommendations.
|
| Full Scan for Malware |
Performs a full malware scan on the selected computers. The actions taken by a full scan depend on the Malware Manual Scan Configuration in effect on this computer. See Configure malware scans. |
| Quick Scan for Malware |
Scans critical system areas for currently active threats. Quick Scan looks for currently-active malware but does not perform deep file scans to look for dormant or stored infected files. On larger drives, Quick Scan is significantly faster than a Full Scan. Quick Scan is only available on-demand. You cannot schedule a Quick Scan as part of a scheduled task.
|
| Scan for Open Ports | Performs a port scan on all selected computers and checks the agent installed on the computer to determine whether its state is either Deactivation Required, Activation Required, Agent Reactivate Required, or Online. The scan operation, by default, scans ports 1-1024. This range can be changed in Computer or Policy editor
The agent's listening port number for heartbeats is always scanned regardless of port range settings. When the Manager connects to communicate with the agent, it uses that port number. If communication direction is set to "Agent/Appliance Initiated" for a computer (Computer or Policy editor
New computers on the network will not be detected. To find new computers, use the Discover tool.
|
| Cancel Currently Executing Port Scans | If you have initiated a set of port scans to a large number of computers or over a large range of ports and the scan is taking too long, use the Cancel Currently Executing Port Scans option to cancel the scans. |
| Scan for integrity |
Integrity Monitoring tracks changes to a computer's system and files. It does by creating a baseline and then performing periodic scans to compare the current state of the computer to the baseline. For more information see Set up integrity monitoring. |
| Rebuild Integrity Baseline | Rebuilds a baseline for Integrity Monitoring on this computer. |
| Assign Asset Value |
Asset values allow you to sort computers and events by importance. The various security rules have a severity value. When rules are triggered on a computer, the severity values of the rules are multiplied by the asset value of the computer. This value is used to rank events in order of importance. See Rank events to quantify their importance. |
| Assign a Relay Group | To select a relay group for this computer to download updates from, right-click the computer and choose Actions > Assign a Relay Group. |
Computers icons
-
 Ordinary computer
Ordinary computer -
 Deep Security Relay (a computer with a Relay-enabled Agent)
Deep Security Relay (a computer with a Relay-enabled Agent) -
 Deep Security Scanner (a computer with a Scanner-enabled agent)
Deep Security Scanner (a computer with a Scanner-enabled agent) -
 Docker host (physical computer)
Docker host (physical computer) -
 Azure virtual machine with Docker
Azure virtual machine with Docker -
 Amazon EC2 with Docker
Amazon EC2 with Docker -
 Azure virtual machine with Scanner
Azure virtual machine with Scanner -
 Azure virtual machine with Scanner (started)
Azure virtual machine with Scanner (started) -
 Azure virtual machine with Scanner (stopped)
Azure virtual machine with Scanner (stopped) -
 Azure virtual machine with Scanner (suspended)
Azure virtual machine with Scanner (suspended) -
 Amazon WorkSpace (started)
Amazon WorkSpace (started)
Status information for different types of computers
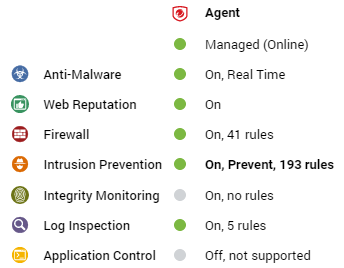
Ordinary computer
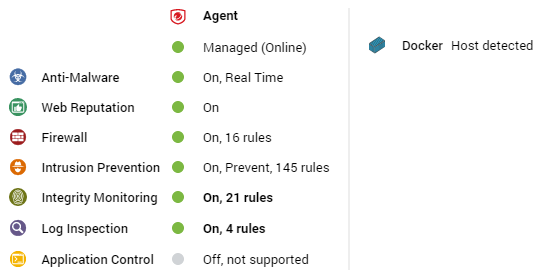
The preview pane for an ordinary computer displays the presence of an agent, its status, and the status of the protection modules.
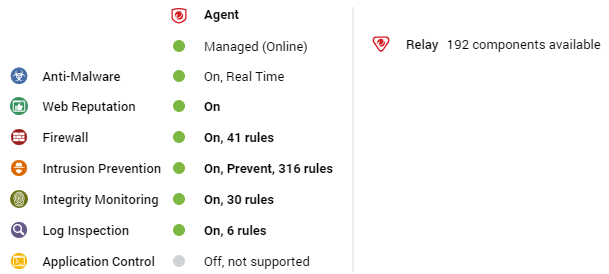
Relay
The preview pane for a Deep Security relay-enabled agent displays its status, the number of security update components it has available for distribution, and the status of the protection modules provided by its embedded Deep Security agent.
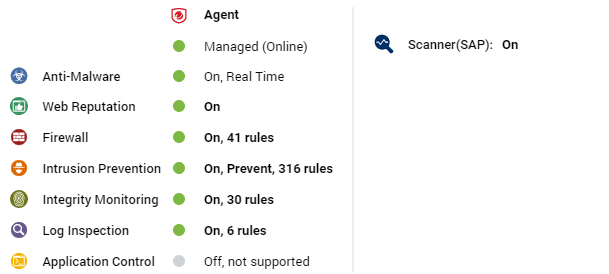
Deep Security Scanner
The preview pane for a Deep Security Scanner displays the presence of an agent or combined mode (agent and appliance), its status, the status of the protection modules, and the scanner status (SAP).
Docker hosts
The preview pane for a docker host displays the presence of an agent and its status, the status of the protection modules, and the Docker status.