Deep Security 10.1 has reached end of support. Use the version selector (above) to see more recent versions of the Help Center.
Set vNetwork behavior when appliances shut down
In NSX Manager 6.3.0 or later, there is an important networking change. Protected guest VMs might lose vNetwork connectivity if:
-
On Deep Security Manager, for protected VMs, you enable any feature that can use network introspection:
- firewall
- IPS
- web reputation
and select Deep Security Virtual Appliance as the protection source.
- Configure NSX 6.3.0 or later to provide network introspection for guest VMs.
-
On the ESXi server, Deep Security Virtual Appliance is:
- deleted and re-deployed, or
- powered down, or
- its ds_agent service is unavailable.
This occurs because, if you don't configure failOpen (allow network traffic to continue while the appliance's protection isn't available), then NSX Manager 6.3.0 by default now fails closed (brings down the vNetwork). When the appliance reboots or is otherwise not available, NSX applies this policy option.
Failing closed eliminates risk of security compromise while the appliance is down, not securing the vNetwork. Down time is a bigger risk for many organizations, however.
If you require uninterrupted vNetwork connectivity, configure the option in vSphere.
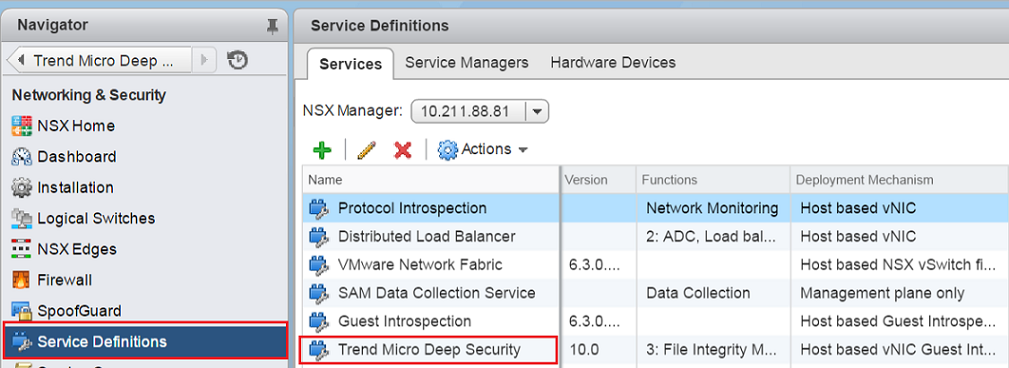
- In the vSphere Web Client, go to Home > Networking & Security > Service Definitions.
-
Double-click Trend Micro Deep Security service.
-
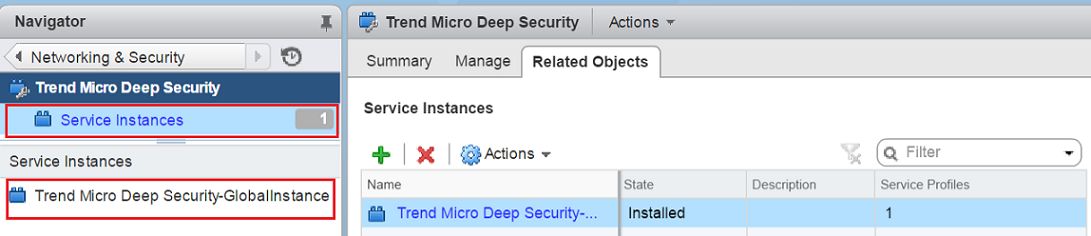
Click Service Instances and then click Trend Micro Deep Security-GlobalInstance.
-
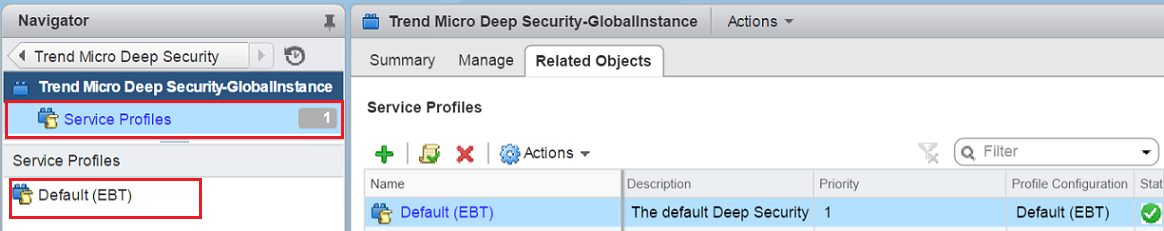
Click Service Profiles and then click Default (EBT) to display the contents of Trend Micro Deep Security service profile.
-
On Default (EBT), select Settings and then click Edit.
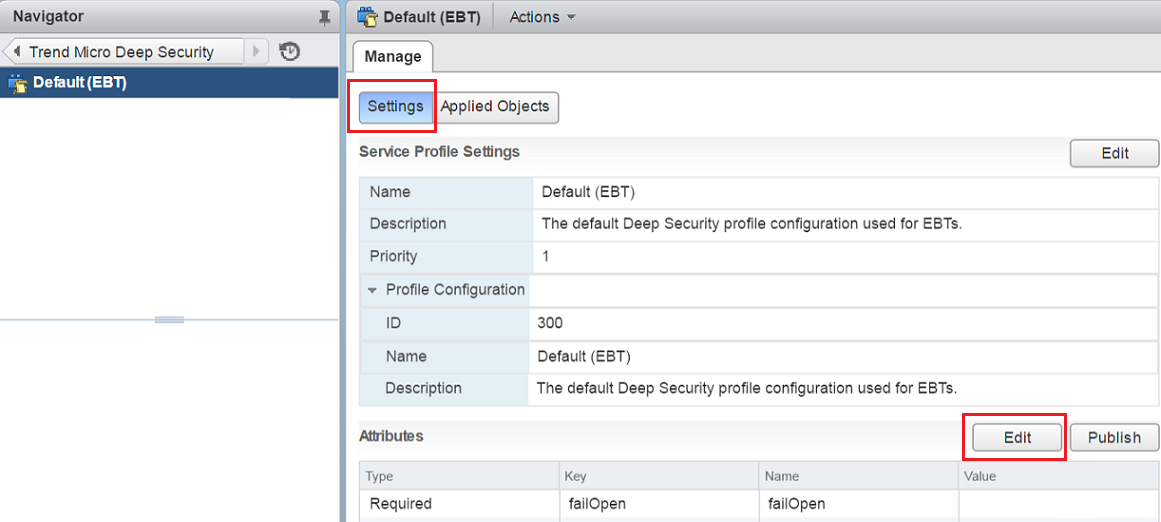
-
In the value of failOpen, type
true, and then click OK.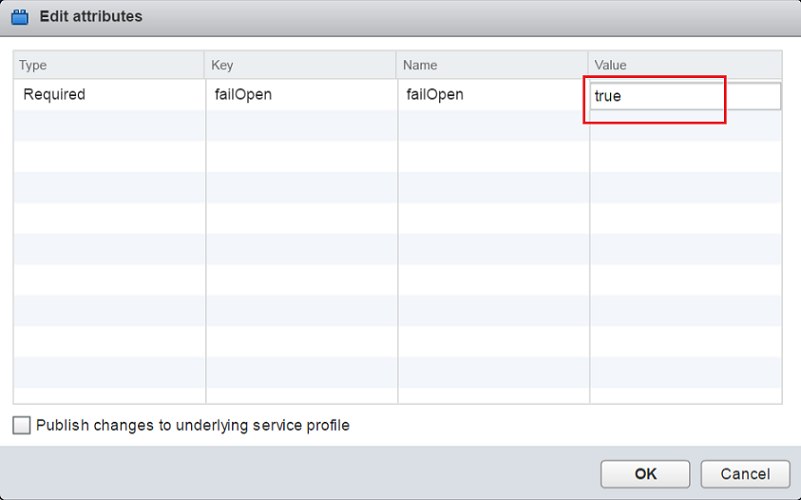
- Click Publish.
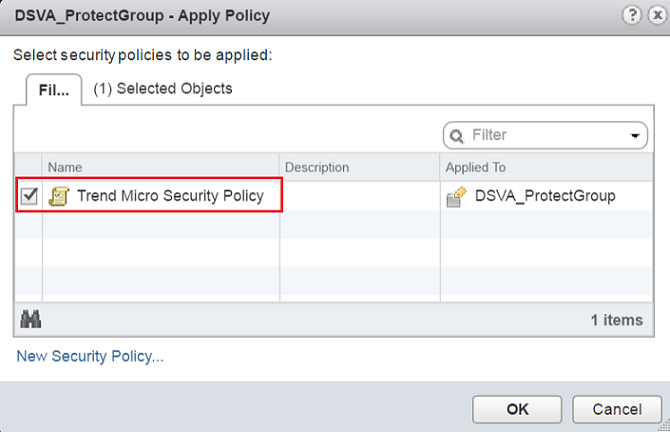
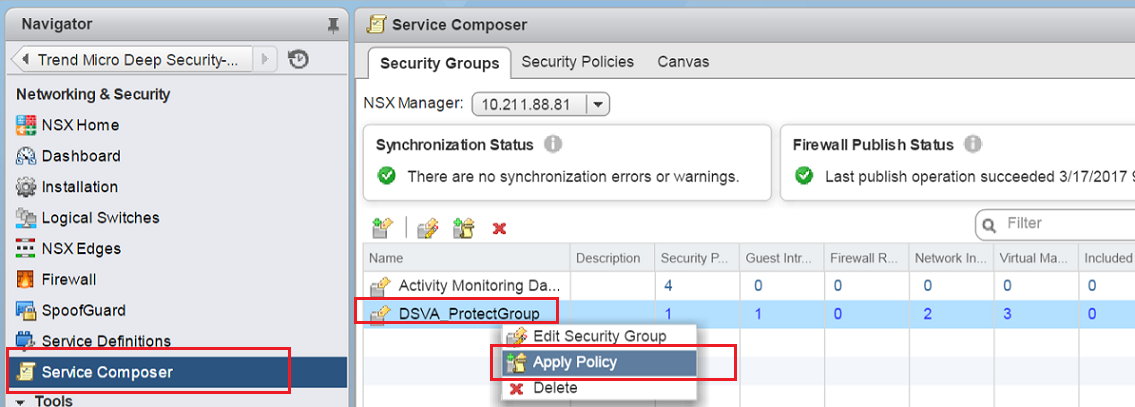
- Go to Networking & Security > Service Composer > Security Groups.
-
Right-click the security group and select Apply Policy.
-
If the policy was already deployed, and you are correcting the policy, you must unbind and re-bind it to the protected VMs' NSX security group in order to resend the policy. Deselect the security policy and then click OK. Select the security policy again, and then click OK.
You must immediately re-deploy the policy. Network connectivity for all protected guest VMs on the ESXi server may be interrupted until you do.