Deep Security 10.1 has reached end of support. Use the version selector (above) to see more recent versions of the Help Center.
Examine a Log Inspection rule
The Log Inspection feature in Deep Security enables real-time analysis of 3rd party log files. The Log Inspection Rules and Decoders provide a framework to parse, analyze, rank and correlate events across a wide variety of systems. As with Intrusion Prevention and Integrity Monitoring, Log Inspection content is delivered in the form of rules included in a security update. These Rules provide a high level means of selecting the applications and logs to be analyzed.
Log Inspection rules are found in the Deep Security Manager at Policies > Common Objects > Rules > Log Inspection Rules.
Log Inspection Rule Structure and the Event Matching Process
This screen shot displays the contents of the Configuration tab of the Properties window of the "Microsoft Exchange" Log Inspection Rule:
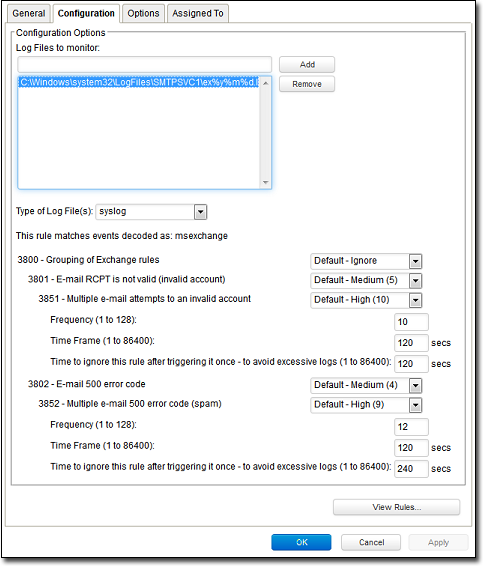
Here is the structure of the Rule:
- 3800 - Grouping of Exchange Rules - Ignore
- 3801 - Email rcpt is not valid (invalid account) - Medium (4)
- 3851 - Multiple email attempts to an invalid account - High (9)
- Frequency - 10
- Time Frame - 120
- Ignore - 120
- 3851 - Multiple email attempts to an invalid account - High (9)
- 3802 - Email 500 error code - Medium (4)
- 3852 - Email 500 error code (spam) - High (9)
- Frequency - 12
- Time Frame - 120
- Ignore - 240
- 3852 - Email 500 error code (spam) - High (9)
- 3801 - Email rcpt is not valid (invalid account) - Medium (4)
The Log Inspection engine will apply Log Events to this structure and see if a match occurs. Let's say that an Exchange event occurs, and this event is an email receipt to an invalid account. The event will match line 3800 (because it is an Exchange event). The event will then be applied to line 3800's sub-rules: 3801 and 3802.
If there is no further match, this "cascade" of matches will stop at 3800. Because 3800 has a severity level of "Ignore", no Log Inspection Event would be recorded.
However, an email receipt to an invalid account does match one of 3800's sub-rules: sub-rule 3801. Sub-rule 3801 has a severity level of "Medium(4)". If the matching stopped here, a Log Inspection Event with a severity level of "Medium(4)" would be recorded.
But there is still another sub-rule to be applied to the event: sub-rule 3851. Sub-rule 3851 with its three attributes will match if the same event has occurred 10 times within the last 120 seconds. If so, a Log Inspection Event with a severity "High(9)" is recorded. (The "Ignore" attribute tells sub-rule 3851 to ignore individual events that match sub-rule 3801 for the next 120 seconds. This is useful for reducing "noise".)
Assuming the parameters of sub-rule 3851 have been matched, a Log Inspection Event with Severity "High(9)" is now recorded.
Looking at the Options tab of the Microsoft Exchange Rule, we see that Deep Security Manager will raise an Alert if any sub-rules with a severity level of "Medium(4)" have been matched. Since this is the case in our example, the Alert will be raised (if "Alert when this rule logs an event" is selected).
Duplicate Sub-rules
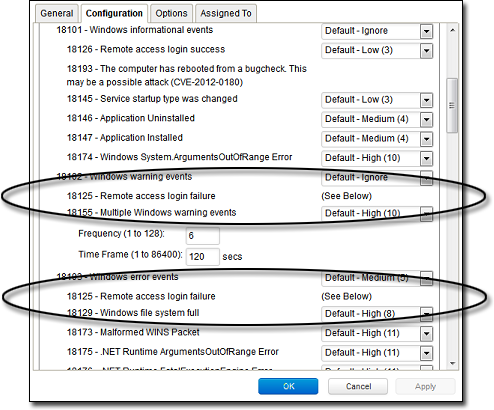
Some Log Inspection Rules have duplicate sub-rules. To see an example, open the "Microsoft Windows Events" rule and click on the Configuration tab. Note that sub-rule 18125 (Remote access login failure) appears under sub-rules 18102 and 18103. Also note that in both cases sub-rule 18125 does not have a severity value, it only says "See Below".
Instead of being listed twice, Rule 18125 is listed once at the bottom of the Configuration page: