Deep Security 10.1 has reached end of support. Use the version selector (above) to see more recent versions of the Help Center.
Computer and policy editor settings
The Settings section of the policy editor and computer editor has the following tabbed sections:
General tab
Communication Direction
- Bidirectional: By default, communications are bidirectional. This means that the agent/appliance normally initiates the heartbeat but still listens on the agent's listening port number for connections from the Deep Security Manager. The manager is still free to contact the agent/appliance in order to perform operations as required. This allows the manager to apply changes to the security configuration to the agent/appliance
as they occur.
The Deep Security Virtual Appliance can only operate in bidirectional mode. Changing this setting to any other mode for a virtual appliance will disrupt functionality.
- Manager Initiated: With this option selected, all manager to agent/appliance communications are initiated by the manager. This includes security configuration updates, heartbeat operations, and requests for event logs.
- Agent/Appliance Initiated:
With this option selected, the agent/appliance does not listen for connections from its Manager. Instead it contacts the manager on the port number where the Manager listens for agent heartbeats. Once the agent/appliance has established a TCP connection with the manager, all normal communication takes place: the manager first asks the agent/appliance for its status and for any events. (This is the
heartbeat operation.) If there are outstanding operations that need to be performed on the computer (for example, the policy needs to be updated), these operations are performed before the connection is closed. In this mode, communications between the manager and the agent/appliance only occur on every heartbeat. If an agent/appliance's security configuration has changed, it will not be updated until the next heartbeat.
Before configuring an agent/appliance for agent/appliance initiated communication, ensure that the manager URL and heartbeat port can be reached by the Agent\Appliance. If the Agent\Appliance is unable to resolve the Manager URL or is unable to reach the IP and port, Agent/Appliance initiated communications will fail for this Agent/Appliance. The Manager URL and the heartbeat port are listed in the System Details area in Administration > System Information .
action: force allow or bypass
priority: 4 - highest
packet's direction: incoming
frame type: IP
protocol: TCP
packet's destination port: agent's listening port number for heartbeat connections from the Manager (or a list that includes the port number)
While these settings are in effect, the new rule will replace the hidden rule. You can then type packet source information for IP or MAC addresses, or both, to restrict traffic to the computer.
Heartbeat
- Heartbeat Interval (in minutes): How much time passes between heartbeats.
- Number of Heartbeats that can be missed before an alert is raised: This setting determines how many missed heartbeats are allowed to go by before the manager triggers an alert. (For example, entering three will cause the manager to trigger an alert on the fourth missed heartbeat.)
If the computer is a server, too many missed heartbeats in a row may indicate a problem with the agent/appliance or the computer itself. However if the computer is a laptop or any other system that is likely to experience a sustained loss of connectivity, this setting should be set to "unlimited".
- Maximum change (in minutes) of the local system time on the computer between heartbeats before an alert is raised: For agents that are capable of detecting changes to the system clock (Windows agents only) these events are reported to the manager as agent event 5004. If the change exceeds the clock change listed here then an alert is triggered. For agents that do not support this capability, the manager monitors the system time reported by the agent at each heartbeat operation and will trigger an alert if it detects a change greater than the permissible change specified in this setting.Once a Computer-Clock-Changed alert is triggered, it must be dismissed manually.
- Raise Offline Errors For Inactive Virtual Machines: Sets whether an offline error is raised if the virtual machine is stopped.
Send policy changes immediately
By default, the value for the Automatically send Policy changes to computers setting is "Yes". This means that any changes to a security policy are automatically applied to the computers that use the policy. If you change this setting to "No", you will need find affected computers on the Computers page, right-click them, and choose "Send Policy" from the context menu.
Troubleshooting
You can increase the granularity of the logging level and record more events for troubleshooting purposes, however you should exercise caution when using this option since this can significantly increase the total size of your event logs.
Choose whether to inherit the logging override settings from the policy assigned to this computer ("Inherited"), to not override logging settings ("Do Not Override"), to log all triggered firewall rules ("Full Firewall Event Logging"), to log all triggered intrusion prevention rules ("Full Intrusion Prevention Event Logging"), or to log all triggered rules ("Full Logging").
Agent self-protection
Use these settings to prevent local users from interfering with agent functionality.
- Prevent local end-users from uninstalling, stopping, or otherwise modifying the agent: This will prevent local users from uninstalling the agent, stopping the agent service, modifying agent-related Windows Registry entries, or modifying agent-related files. These restrictions can be overridden by issuing local instructions from the command line. (See command-line utilities.) When agent self-protection is enabled, attempts to make modfications to the agent via the local operating system graphical user interface will be met with a message similar to "Removal or modification of this application is prohibited by its security settings".
- Local override requires password: It is possible that a Deep Security Manager loses the ability to communicate with an agent. In such cases you will have to interact with the agent locally using the agent's command-line interface. Enter a password here to password-protect the local command-line functionality. (Recommended.)
Store this password in a safe location. If you lose or forget the password you will have to contact your support provider for assistance in overriding this protection.
- Local override requires password: It is possible that a Deep Security Manager loses the ability to communicate with an agent. In such cases you will have to interact with the agent locally using the agent's command-line interface. Enter a password here to password-protect the local command-line functionality. (Recommended.)
Anti-malware protection must be "On" to prevent the following:
- Stopping the agent service
- Modifying agent-related Windows Registry entries
- Modifying agent related files
Anti-malware protection is not required to prevent local users from uninstalling the agent.
Turn agent self-protection off or on from the command line
- Log in to the local computer as an administrator
- Run a command prompt from the agent's (or relay's) installation directory
- Enter the following command (where "password" is the password set using the Local override requires password setting):
- to turn Self-Protection off:
dsa_control --selfprotect=0 --passwd=password - to turn Self-Protection on
dsa_control --selfprotect=1 --passwd=password
If no password was set, omit the "--passwd" parameter. - to turn Self-Protection off:
Open ports
Select a port list to be used when the Deep Security Manager performs a port scan on discovered computers. (The port lists in the list are the same ones defined in the Port Lists page in the Shared section.)
Recommendations
Periodically, the agents can scan their computer for common applications and then make rule recommendations based on what is detected. This setting sets the interval between scans on computers that have been configured to allow them.
Virtual appliance scans (Policy editor only)
The virtual appliance has various settings that can significantly improve the efficiency of security scans in large virtual machine environments where agentless protection has been implemented.
- Max Concurrent Scans: Scan requests are queued by the virtual appliance and carried out in the order in which they arrive. However, the virtual appliance is capable of carrying out concurrent scans on multiple VMs. The recommended number of concurrent scans is five. Beyond 10, the performance of the virtual appliance may begin to decline. This setting applies to manual and scheduled scans.
- Max On-Demand Malware Scan Cache Entries: This determines, for manual (on-demand) malware scans, the maximum number of records that identify and describe a file or other type of scannable content to keep. One million entries will use approximately 100MB of memory.
- Max Real Time Malware Scan Cache Entries: This determines, for real-time malware scans, the maximum number of records that identify and describe a file or other type of scannable content to keep. One million entries will use approximately 100MB of memory.
- Max Integrity Monitoring Scan Cache Entries: This determines, for integrity monitoring, the maximum number of entities included in the baseline data for integrity monitoring. Two hundred thousand entities will use approximately 100MB of memory.
Environment variable overrides
Environment variables are used by the integrity monitoring module to represent some standard locations in the directory system of the Windows operating system. For example, the Microsoft Windows - 'Hosts' file modified integrity monitoring rule, which monitors changes to the Windows hosts file, looks for that file in the C:\WINDOWS\system32\drivers\etc folder. However not all Windows installations use the C:\WINDOWS\ directory, so the integrity monitoring rule uses the WINDIR environment variable and represents the directory this way as %WINDIR%\system32\drivers\etc.
The following are the default environment variables used by the integrity monitoring module:
| Name | Value |
| ALLUSERSPROFILE | C:\ProgramData |
| COMMONPROGRAMFILES | C:\Program Files\Common Files |
| PROGRAMFILES | C:\Program Files |
| SYSTEMDRIVE | C: |
| SYSTEMROOT | C:\Windows |
| WINDIR | C:\Windows |
Override any of the environment variables
- Click the View Environment Variables button to display the Environment Variable Overrides page.
- Click New in the menu bar and enter a new name-value pair (for example, WINDIR and D:\Windows) and click OK.
Advanced tab
Network Engine Mode
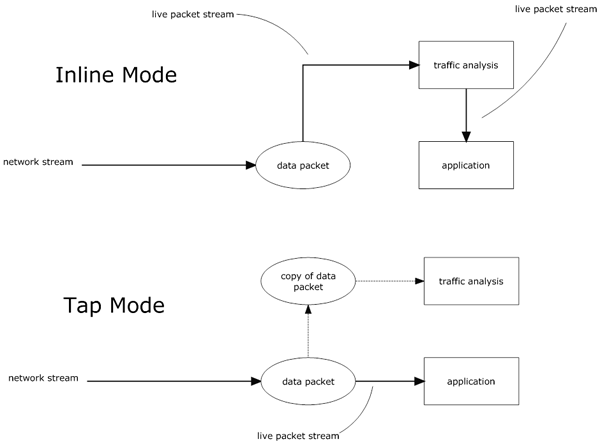
The agent/appliance's network engine can operate Inline or in tap mode. When operating Inline, the packet stream passes through the network engine. Stateful tables are maintained, firewall rules are applied and traffic normalization is carried out so that intrusion prevention rules can be applied to payload content. When operating in tap mode, the packet stream is cloned and diverted from the main stream. In tap mode, the packet stream is not modified; all operations are carried out on the cloned stream.
Events
You can set the maximum size of each individual log file and how many of the most recent files are kept. Event log files will be written to until they reach the maximum allowed size, at which point a new file will be created and written to until it reaches the maximum size and so on. Once the maximum number of files is reached, the oldest will be deleted before a new file is created. Event log entries usually average around 200 bytes in size and so a 4MB log file will hold about 20,000 log entries. How quickly your log files fill up depends on the number of rules in place.
- Maximum size of the event log files (on Agent/Appliance): Maximum size that the log file can reach before a new log file is created.
- Number of event log files to retain (on Agent/Appliance):
Maximum number of log files that will be kept. Once the maximum number of log files is reached, the oldest file will be deleted before a new one is created.
Events are records of individual events. Counters are a record of the number of times individual events have occurred. Events are used to populate the Events pages. Counters are used to populate the Dashboard Widgets (number of firewall events over the last 7 days, etc.) and the reports. You might want to collect only counters if, for example, you are using syslog for event collection; events can potentially take up a lot of disk space and you may not want to store the data twice.
- Do Not Record Events with Source IP of: This option is useful if you want Deep Security to not make record events for traffic from certain trusted computers.
The following three settings let you fine tune event aggregation. To save disk space, Deep Security agents/appliances will take multiple occurrences of identical events and aggregate them into a single entry and append a "repeat count", a "first occurrence" timestamp, and a "last occurrence" timestamp. To aggregate event entries, Deep Security agents/appliances need to cache the entries in memory while they are being aggregated before writing them to disk.
- Cache Size: Determines how many types of events to track at any given time. Setting a value of 10 means that 10 types of events will be tracked (with a repeat count, first occurrence timestamp, and last occurrence timestamp). When a new type of event occurs, the oldest of the 10 aggregated events will be flushed from the cache and written to disk.
- Cache Lifetime: Determines how long to keep a record in the cache before flushing it to disk. If this value is 10 minutes and nothing else causes the record to be flushed, any record that reaches an age of 10 minutes gets flushed to disk.
- Cache Stale time: Determines how long to keep a record whose repeat count has not been recently incremented. If Cache Lifetime is 10 minutes and Cache Staletime is two minutes, an event record which has gone two minutes without being incremented will be flushed and written to disk.
Regardless of the above settings, the cache is flushed whenever events are sent to the Deep Security Manager.
Anti-evasion settings
Anti-evasion settings control the network engine handling of abnormal packets that may be attempting to evade analysis.
Security Posture: There are three options for the posture setting. This setting can be inherited from the parent policy:
- Normal: This is the default setting. It is tuned to prevent the evasion of IPS rules, without false positives.
- Strict: Strict mode performs more stringent checking than Normal mode but it could result in some false-positive results. Strict mode is useful for penetration testing but should not be enabled under normal circumstances.
| Setting | Description | Normal value | Strict value |
|---|---|---|---|
| Invalid TCP Timestamps | Action to take when a TCP timestamp is too old |
|
Deny |
| TCP Timestamp PAWS Window | Packets can have timestamps. When a timestamp has an earlier timestamp than the one that came before it, it can be suspicious. The tolerance for the difference in timestamps depends on the operating system. For Windows systems, select 0 (the system will only accept packets with a timestamp that is equal to or newer than the previous packet). For Linux systems, select 1 (the system will accept packets with a timestamp that is a maximum of one second earlier than the previous packet). | 1 for Linux agents, otherwise 0 | 1 for Linux agents, otherwise 0 |
| Timestamp PAWS Zero Allowed | Action to take when a TCP timestamp is zero | Deny for Linux agents or NDIS5, otherwise Allow | Deny for Linux agents or NDIS5, otherwise Allow |
| Fragmented Packets | Action to take when a packet is fragmented | Allow | Allow |
| TCP Zero Flags | Action to take when a packet has zero flags set | Deny | Deny |
| TCP Congestion Flags | Action to take when a packet has congestion flags set | Allow | Allow |
| TCP Urgent Flags | Action to take when a packet has urgent flags set | Allow | Deny |
| TCP Syn Fin Flags | Action to take when a packet has both SYN and FIN flags set | Deny | Deny |
| TCP Syn Rst Flags | Action to take when a packet has both SYN and RST flags set | Deny | Deny |
| TCP Rst Fin Flags | Action to take when a packet has both RST and FIN flags set | Deny | Deny |
| TCP Syn with Data | Action to take when a packet has a SYN flag set and also contains data | Deny | Deny |
| TCP Split Handshake | Action to take when a SYN is received instead of SYNACK, as a reply to a SYN. | Deny | Deny |
| RST Packet Out of Connection | Action to take for a RST packet without a known connection | Allow | Deny |
| FIN Packet Out of Connection | Action to take for a FIN packet without a known connection | Allow | Deny |
| OUT Packet Out of Connection | Action to take for an outgoing packet without a known connection | Allow | Deny |
| Evasive Retransmit | Action to take for a packet with duplicated or overlapping data | Allow | Deny |
| TCP Checksum | Action to take for a packet with an invalid checksum | Allow | Deny |
Advanced Network Engine settings
Generate an Alert when Agent configuration package exceeds maximum size: Yes or No. The default is Yes.
If you deselect the Default checkbox, you can customize these settings:
- CLOSED timeout: For gateway use. When a gateway passes on a "hard close" (RST), the side of the gateway that received the RST will keep the connection alive for this amount of time before closing it.
- SYN_SENT Timeout: How long to stay in the SYN-SENT state before closing the connection.
- SYN_RCVD Timeout: How long to stay in the SYN_RCVD state before closing the connection.
- FIN_WAIT1 Timeout: How long to stay in the FIN-WAIT1 state before closing the connection.
- ESTABLISHED Timeout: How long to stay in the ESTABLISHED state before closing the connection.
- ERROR Timeout: How long to maintain a connection in an Error state. (For UDP connections, the error can be caused by any of a variety of UDP problems. For TCP connections, the errors are probably due to packets being dropped by the firewall.)
- DISCONNECT Timeout: How long to maintain idle connections before disconnecting.
- CLOSE_WAIT Timeout: How long to stay in the CLOSE-WAIT state before closing the connection.
- CLOSING Timeout: How long to stay in the CLOSING state before closing the connection.
- LAST_ACK Timeout: How long to stay in the LAST-ACK state before closing the connection.
- ACK Storm timeout: The maximum period of time between retransmitted ACKs within an ACK Storm. In other words, if ACKs are being retransmitted at a lower frequency then this timeout, they will NOT be considered part of an ACK Storm.
- Boot Start Timeout: For gateway use. When a gateway is booted, there may already exist established connections passing through the gateway. This timeout defines the amount of time to allow non-SYN packets that could be part of a connection that was established before the gateway was booted to close.
- Cold Start Timeout: Amount of time to allow non-SYN packets that could belong to a connection that was established before the stateful mechanism was started.
- UDP Timeout: Maximum duration of a UDP connection.
- ICMP Timeout: Maximum duration of an ICMP connection.
- Allow Null IP: Allow or block packets with no source or destination IP address.
- Block IPv6 on Agents and Appliances versions 8 and earlier: Block or Allow IPv6 packets on older version 8.0 agents and appliances.
Deep Security Agents and Appliances versions 8.0 and older are unable to apply firewall or DPI rules to IPv6 network traffic and so the default setting for these older versions is to block IPv6 traffic.Block IPv6 on Agents and Appliances versions 8 and earlier: Block or Allow IPv6 packets on older version 8.0 Agents and Appliances.Deep Security Agents and Appliances versions 8.0 and older are unable to apply firewall or DPI Rules to IPv6 network traffic and so the default setting for these older versions is to block IPv6 traffic.
- Block IPv6 on Agents and Appliances versions 9 and later: Block or Allow IPv6 packets on agents and appliances that are version 9 or later.
- Connection Cleanup Timeout: Time between cleanup of closed connections (see next).
- Maximum Connections per Cleanup: Maximum number of closed connections to cleanup per periodic connection cleanup (see previous).
- Block Same Src-Dest IP Address: Block or allow packets with same source and destination IP address. (Doesn't apply to loopback interface.)
- Maximum TCP Connections: Maximum simultaneous TCP Connections.
- Maximum UDP Connections: Maximum simultaneous UDP Connections.
- Maximum ICMP Connections: Maximum simultaneous ICMP Connections.
- Maximum Events per Second: Maximum number of events that can be written per second.
- TCP MSS Limit: The MSS is the Maximum Segment Size (or largest amount of data) that can be sent in a TCP packet without being fragmented. This is usually established when two computers establish communication. However, in some occasions, the traffic goes through a router or switch that has a smaller MSS. In this case the MSS can change. This causes retransmission of the packets and the agent or appliance logs them as "Dropped Retransmit". In cases where there are large numbers of dropped retransmit event entries, you may wish to lower this limit and see if the volume is reduced.
- Number of Event Nodes: The maximum amount of kernel memory the driver will use to store log/event information for folding at any one time.
Event folding occurs when many events of the same type occur in succession. In such cases, the agent/appliance will "fold" all the events into one.
- Ignore Status Code: This option lets you ignore certain types of events. If, for example, you are getting a lot of "Invalid Flags" you can simply ignore all instances of that event.
- Ignore Status Code: Same as above.
- Ignore Status Code: Same as above.
- Advanced Logging Policy:
- Bypass: No filtering of events. Overrides the "Ignore Status Code" settings (above) and other advanced settings, but does not override logging settings defined in the Deep Security Manager. For example, if firewall stateful configuration logging options set from a Firewall Stateful Configuration Properties window in the Deep Security Manager will not be affected.
- Normal: All events are logged except dropped retransmits.
- Default: Will switch to "Tap Mode" (below) if the engine is in tap mode, and will switch to "Normal" (above) if the engine is in inline mode.
- Backwards Compatibility Mode: For support use only.
- Verbose Mode: Same as "Normal" but including dropped retransmits.
- Stateful and Normalization Suppression: Ignores dropped retransmit, out of connection, invalid flags, invalid sequence, invalid ack, unsolicited udp, unsolicited ICMP, out of allowed policy.
- Stateful, Normalization, and Frag Suppression: Ignores everything that "Stateful and Normalization Suppression" ignores as well as events related to fragmentation.
- Stateful, Frag, and Verifier Suppression: Ignores everything "Stateful, Normalization, and Frag Suppression" ignores as well as verifier-related events.
- Tap Mode: Ignores dropped retransmit, out of connection, invalid flags, invalid sequence, invalid ack, max ack retransmit, packet on closed connection.
For a more comprehensive list of which events are ignored in Stateful and Normalization Suppression; Stateful, Normalization, and Frag Suppression; Stateful, Frag, and Verifier Suppression; and Tap modes, see Reduce the number of logged events. - Silent TCP Connection Drop: When Silent TCP Connection Drop is on, a RST packet is only sent to the local stack. No RST packet is sent on the wire. This reduces the amount of information sent back to a potential attacker.
If you enable the Silent TCP Connection Drop you must also adjust the DISCONNECT Timeout. Possible values for DISCONNECT Timeout range from 0 seconds to 10 minutes. This must be set high enough that the connection is closed by the application before it is closed by the Deep Security agent/appliance. Factors that will affect the DISCONNECT Timeout value include the operating system, the applications that are creating the connections, and network topology.
- Enable Debug Mode: When in debug mode, the agent/appliance captures a certain number of packets (specified by the setting below: Number of Packets to retain in Debug Mode). When a rule is triggered and debug mode is on, the agent/appliance will keep a record of the last X packets that passed before the rule was triggered. It will return those packets to the manager as debug events.
Debug mode can very easily cause excessive log generation and should only be used under Client Services supervision.
- Number of Packets to retain in Debug Mode: The number of packets to retain and log when debug mode is on.
- Log All Packet Data: Record the packet data for events that are not associated with specific firewall or intrusion prevention rules. That is, log packet data for events such as "Dropped Retransmit" or "Invalid ACK".
Events that have been aggregated because of event folding cannot have their packet data saved.
- Log only one packet within period: If this option is enabled and Log All Packet Data is not, most logs will contain only the header data. A full packet will be attached periodically, as specified by the Period for Log only one packet within period setting.
- Period for Log only one packet within period: When Log only one packet within period is enabled, this setting specifies how often the log will contain full packet data.
- Maximum data size to store when packet data is captured: The maximum size of header or packet data to be attached to a log.
- Generate Connection Events for TCP: Generates a firewall event every time a TCP connection is established.
- Generate Connection Events for ICMP: Generates a firewall event every time an ICMP connection is established.
- Generate Connection Events for UDP: Generates a firewall event every time a UDP connection is established.
- Bypass CISCO WAAS Connections: This mode bypasses stateful analysis of TCP sequence numbers for connections initiated with the proprietary CISCO WAAS TCP option selected. This protocol carries extra information in invalid TCP Sequence and ACK numbers that interfere with stateful firewall checks. Only enable this option if you are using CISCO WAAS and you are seeing connections with Invalid SEQ or Invalid ACK in the firewall logs. When this option is selected, TCP stateful sequence number checks are still performed for non WAAS enabled connections.
- Drop Evasive Retransmit: Incoming packets containing data that has already been processed will be dropped to avoid possible evasive retransmit attack techniques.
- Verify TCP Checksum: The segment's checksum field data will be used to assess the integrity of the segment.
- Minimum Fragment Offset: Defines the minimum acceptable IP fragment offset. Packets with offsets less than this will be dropped with reason "IP fragment offset too small". If set to 0 no limit is enforced. (default 60)
- Minimum Fragment Size: Defines the minimum acceptable IP fragment size. Fragmented packets that are smaller than this will be dropped with reason "First fragment too small" as potentially malicious. (default 120)
- SSL Session Size: Sets the maximum number of SSL session entries maintained for SSL session keys.
- SSL Session Time: Sets how long SSL session renewal keys are valid before they expire.
- Filter IPv4 Tunnels: Not used by this version of Deep Security.
- Filter IPv6 Tunnels: Not used by this version of Deep Security.
- Strict Teredo Port Check: Not used by this version of Deep Security.
- Drop Teredo Anomalies: Not used by this version of Deep Security.
- Maximum Tunnel Depth: Not used by this version of Deep Security.
- Action if Maximum Tunnel Depth Exceeded: Not used by this version of Deep Security.
- Drop IPv6 Extension Type 0: Not used by this version of Deep Security.
- Drop IPv6 Fragments Lower Than minimum MTU: Drop IPv6 fragments that do not meet the minimum MTU size specified by IETF RFC 2460.
- Drop IPv6 Reserved Addresses: Drop these reserved addresses:
- IETF reserved 0000::/8
- IETF reserved 0100::/8
- IETF reserved 0200::/7
- IETF reserved 0400::/6
- IETF reserved 0800::/5
- IETF reserved 1000::/4
- IETF reserved 4000::/2
- IETF reserved 8000::/2
- IETF reserved C000::/3
- IETF reserved E000::/4
- IETF reserved F000::/5
- IETF reserved F800::/6
- Drop IPv6 Site Local Addresses: Drop site local addresses FEC0::/10.
- Drop IPv6 Bogon Addresses: Drop these addresses:
- "loopback ::1
- "IPv4 compatible address", ::/96
- "IPv4 mapped address" ::FFFF:0.0.0.0/96
- "IPv4 mapped address", ::/8
- "OSI NSAP prefix (deprecated by RFC4048)" 0200::/7
- "6bone (deprecated)", 3ffe::/16
- "Documentation prefix", 2001:db8::/32
- Drop 6to4 Bogon Addresses: Drop these addresses:
- "6to4 IPv4 multicast", 2002:e000:: /20
- "6to4 IPv4 loopback", 2002:7f00:: /24
- "6to4 IPv4 default", 2002:0000:: /24
- "6to4 IPv4 invalid", 2002:ff00:: /24
- "6to4 IPv4 10.0.0.0/8", 2002:0a00:: /24
- "6to4 IPv4 172.16.0.0/12", 2002:ac10:: /28
- "6to4 IPv4 192.168.0.0/16", 2002:c0a8:: /32
- Drop IP Packet with Zero Payload: Drop IP packets that have a zero-length payload.
- Drop Unknown SSL Protocol: Drop connection if a client attempts to connect to the Deep Security Manager with the wrong protocol. By default, any protocol other than "http/1.1" will cause an error.
- Force Allow DHCP DNS: Controls whether the following hidden firewall rules are enabled:
Rule type Priority Direction Protocol Source
portDestination
portForce Allow 4 Outgoing DNS Any 53 Force Allow 4 Outgoing DHCP 68 67 Force Allow 4 Incoming DHCP 67 68 When the rules are enabled, agent computers can connect with manager using the listed protocols and ports. The following values for this property are available:
- Inherited: Inherits the setting from the policy
- Turn off rules: Disables the rules. Note that this setting can cause agent computers to appear offline
- Allow DNS Query: Enable only the DNS-related rule
- Allow DNS Query and DHCP Client: Enable all 3 rules
- Force Allow ICMP type3 code4: Controls
whether the following hidden firewall rules are enabled:
Rule type Priority Direction Protocol Type Code Force Allow 4 Incoming ICMP 3 4 When enabled, these rules allow relay computers to connect with the manager so that the relay's heartbeat is transmitted. The following values are available:
- Inherited: Inherits the setting from the policy.
- Turn off rules: Disables the rule. This value can cause connection timeouts or "Destination cannot be reached" responses.
- Add Force Allow rule for ICMP type3 code4: Enables the rule.
- Fragment Timeout: If configured to do so, the intrusion prevention rules will inspect the content of a packet (or packet fragment) if that content is considered suspicious. This setting determines how long after inspecting to wait for the remaining packet fragments before discarding the packet.
- Maximum number of fragmented IP packets to keep: Specifies the maximum number of fragmented packets that Deep Security will keep.
- Send ICMP to indicate fragmented packet timeout exceeded: When this setting is enabled and the fragment timeout is exceeded, an ICMP packet is sent to the remote computer.
Scanner tab
Deep Security Scanner provides integration with the SAP NetWeaver platform.
On the Settings > Scanner page in the Computer or Policy editor, you can enable the SAP integration module for individual computers or policies. You can configure the policy or computer to inherit these settings from its parent policy or you can lock the settings locally.
Note: To use the Deep Security Scanner feature, you must have both the Deep Security Scanner and anti-malware modules activated on the Licenses page.
Note: Deep Security Scanner is not supported on computers where the Deep Security Agent is enabled as a relay.
SIEM tab
Event Forwarding Frequency (From the Agent/Appliance)
Select how often events are sent from the agent/appliance to alert recipients. (Enter syslog configuration in the Event Forwarding areas.)
Event Forwarding
The events from each of the protection modules can be forwarded to a remote computer via syslog.